Xage Zero Trust Blockchain-Protected Fabric for IIOT
Hatem Metwally
2:51:26
Description
Zero trust approach for access management for critical infrastructure
What You'll Learn?
- Zero trust approach for access management for critical infrastructure including the operational technology
- Zero trust secure local access for floor operations within the OT infrastructure itself
- Securely facilitate vendor and third-party OEM remote access into the critical infrastructure down to the OT devices the L1 devices the PLCs and the RTUs
- Enable Dynamic data security to secure the sharing of events and data streams from the OT devices to any external entity without exposing those OT systems
- Cyber-hardening Interconnected Operations with an Asset and Identity-centric Approach
- Modernizing Access Management with Zero Trust
Who is this for?
What You Need to Know?
More details
DescriptionXage is specialized in Zero Trust approach for access management for critical infrastructure including the operational technology to serve basically three key use cases:
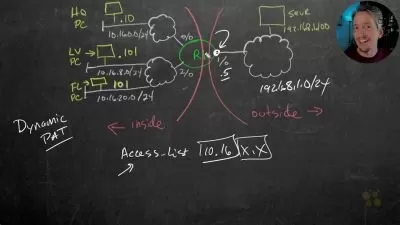
1) Zero trust secure local access for floor operations within the OT infrastructure itself, as well as
2)Â Securely facilitate vendor and third-party OEM remote access into the critical infrastructure down to the OT devices the L1 devices the PLCs and the RTUs, as well as
3) Enable Dynamic data security to secure the sharing of events and data streams from the OT devices to any external entity without exposing those OT systems to any other networks
So all the sessions will always be terminated within the OT infrastructure itself to achieve that
Xage is basically three different products bonded into one single fabric platform
1) Identity-based Access Management
2) Zero trust Remote Access
3) Zero Trust Data Security
Xage does privilege access management, it basically allows you to create or integrate with active directory and create user accounts with specific privileges to Target critical devices where the Xage fabric will be the interface for accessing those critical devices and all the critical device credentials will not be exposed to the user, however it will be closely managed by the Xage fabric itself
In this course we will try to cover the following
- Foundations and Architecture
- Zero Trust Remote Access, File Transfer, and Data Exchange
- Installation and Deployment
- GUI demstifyied
- Access Management
- Device Management
- Policies
- Configure Users & User Groups with MFA
- WebSSH Access Policy with Authorization
- Session Collaboration
Who this course is for:
- IT Support, Security administrators, System administrators, Network administrators, SOC analyst
Xage is specialized in Zero Trust approach for access management for critical infrastructure including the operational technology to serve basically three key use cases:
1) Zero trust secure local access for floor operations within the OT infrastructure itself, as well as
2)Â Securely facilitate vendor and third-party OEM remote access into the critical infrastructure down to the OT devices the L1 devices the PLCs and the RTUs, as well as
3) Enable Dynamic data security to secure the sharing of events and data streams from the OT devices to any external entity without exposing those OT systems to any other networks
So all the sessions will always be terminated within the OT infrastructure itself to achieve that
Xage is basically three different products bonded into one single fabric platform
1) Identity-based Access Management
2) Zero trust Remote Access
3) Zero Trust Data Security
Xage does privilege access management, it basically allows you to create or integrate with active directory and create user accounts with specific privileges to Target critical devices where the Xage fabric will be the interface for accessing those critical devices and all the critical device credentials will not be exposed to the user, however it will be closely managed by the Xage fabric itself
In this course we will try to cover the following
- Foundations and Architecture
- Zero Trust Remote Access, File Transfer, and Data Exchange
- Installation and Deployment
- GUI demstifyied
- Access Management
- Device Management
- Policies
- Configure Users & User Groups with MFA
- WebSSH Access Policy with Authorization
- Session Collaboration
Who this course is for:
- IT Support, Security administrators, System administrators, Network administrators, SOC analyst
User Reviews
Rating
Hatem Metwally
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 8
- duration 2:51:26
- Release Date 2023/09/13