Windows Hacking and Security: Learn Win Hacking From Scratch
Cyber Security Online Training
10:03:09
Description
Learn the art of Windows hacking and security. Learn about kali linux, rhel, website attacks and reverse engineering.
What You'll Learn?
- Learn Windows Hacking and Security.
- Learn Common Website Attacks and Security.
- Learn kali linux from scratch.
- Learn about steganography, social engineering, reverse engineering and more.
Who is this for?
What You Need to Know?
More details
Description"This course is completely based on Ethical Hacking for Windows OS, Website, Social Engineering, Reverse Engineering, etc. This course is created for education purpose only. We are not promoting any illegal activities."
Welcome to the immersive and cutting-edge course on "Windows Hacking and Security: Learn Win Hacking From Scratch"! This comprehensive training program is designed to equip aspiring cybersecurity professionals, IT enthusiasts, and tech-savvy individuals with the knowledge and skills necessary to navigate the intricacies of Windows systems, explore ethical hacking techniques, and fortify System and Websites against potential threats.
Course Overview: In this dynamic course, By blending theoretical understanding with hands-on practical exercises, we ensure that you not only grasp the concepts but also gain invaluable experience applying them in real-world scenarios.
   - Windows Ethical Hacking Practical:
Discover the fundamentals of Windows operating systems and their architecture.
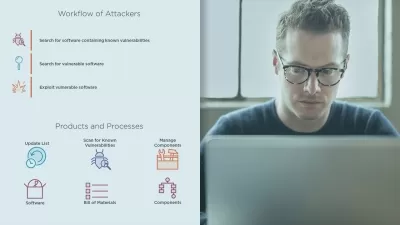
Learn about common vulnerabilities and weaknesses found in Windows environments.
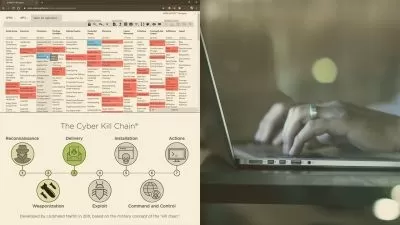
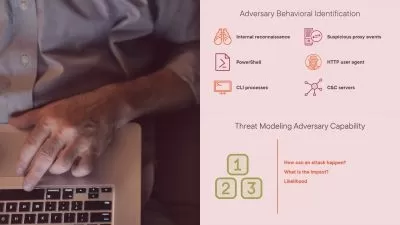
Explore various penetration testing methodologies and ethical hacking techniques.
Gain hands-on experience with tools and frameworks used by security professionals.
  - Advanced Windows Security:
Dive into advanced Windows security mechanisms and protocols.
Understand the principles of access control, privilege escalation, and user management.
Explore ways to secure Windows networks and prevent unauthorized access.
Conduct security audits and vulnerability assessments on Windows systems.
  - Learn KALI Linux
  - Learn Website Hacking and Security
  - Learn Social Engineering
  - Learn Additional Contents
Why Enroll in this Course?
Gain expertise in both Windows hacking and Security, KALI, two crucial areas in the cybersecurity landscape.
Hands-on labs and practical exercises ensure immediate application of knowledge.
Learn from industry experts with extensive experience in cybersecurity and database management.
Acquire the skills needed to pursue a career in cybersecurity, database administration, or IT security consulting.
Receive a completion certificate to showcase your newly acquired skills to employers and peers.
Join us on this exciting journey into the world of Windows Ethical Hacking and Security + KALIÂ Linux. Be prepared to challenge yourself, expand your technical horizons, and enhance your cyber-defense abilities. Enroll now and take your first steps towards a rewarding and promising career in cybersecurity!
Who this course is for:
- Anyone who want to learn Windows Hacking and Security with kali, rhel, website and much more.
"This course is completely based on Ethical Hacking for Windows OS, Website, Social Engineering, Reverse Engineering, etc. This course is created for education purpose only. We are not promoting any illegal activities."
Welcome to the immersive and cutting-edge course on "Windows Hacking and Security: Learn Win Hacking From Scratch"! This comprehensive training program is designed to equip aspiring cybersecurity professionals, IT enthusiasts, and tech-savvy individuals with the knowledge and skills necessary to navigate the intricacies of Windows systems, explore ethical hacking techniques, and fortify System and Websites against potential threats.
Course Overview: In this dynamic course, By blending theoretical understanding with hands-on practical exercises, we ensure that you not only grasp the concepts but also gain invaluable experience applying them in real-world scenarios.
   - Windows Ethical Hacking Practical:
Discover the fundamentals of Windows operating systems and their architecture.
Learn about common vulnerabilities and weaknesses found in Windows environments.
Explore various penetration testing methodologies and ethical hacking techniques.
Gain hands-on experience with tools and frameworks used by security professionals.
  - Advanced Windows Security:
Dive into advanced Windows security mechanisms and protocols.
Understand the principles of access control, privilege escalation, and user management.
Explore ways to secure Windows networks and prevent unauthorized access.
Conduct security audits and vulnerability assessments on Windows systems.
  - Learn KALI Linux
  - Learn Website Hacking and Security
  - Learn Social Engineering
  - Learn Additional Contents
Why Enroll in this Course?
Gain expertise in both Windows hacking and Security, KALI, two crucial areas in the cybersecurity landscape.
Hands-on labs and practical exercises ensure immediate application of knowledge.
Learn from industry experts with extensive experience in cybersecurity and database management.
Acquire the skills needed to pursue a career in cybersecurity, database administration, or IT security consulting.
Receive a completion certificate to showcase your newly acquired skills to employers and peers.
Join us on this exciting journey into the world of Windows Ethical Hacking and Security + KALIÂ Linux. Be prepared to challenge yourself, expand your technical horizons, and enhance your cyber-defense abilities. Enroll now and take your first steps towards a rewarding and promising career in cybersecurity!
Who this course is for:
- Anyone who want to learn Windows Hacking and Security with kali, rhel, website and much more.
User Reviews
Rating
Cyber Security Online Training
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 112
- duration 10:03:09
- Release Date 2023/12/09