White Hat Hacking v10 Online Training
Keith Barker
19:56:33
Description
In this intermediate White Hat Hacking training, Keith Barker prepares security professionals to become penetration and vulnerability testers.
Demand for security professionals is at an all-time high — and that’s particularly true for pen testers. With this security training, you'll learn how to scan networks for vulnerabilities, use Kali Linux to (legally) hack into systems, and write reports on how you did it.
More details
Security professionals who take this White Hat Hacking course will have the skills they need to advance into pen tester roles — and get one of the several offensive security certifications.
For anyone who manages security training, this White Hat Hacking training can be used for penetration and vulnerability exam prep, upskilling security professionals, or to create training plans for network or security professionals.
White Hat Hacking v10: What You Need to Know
While this White Hat Hacking training doesn’t map to a certification, it covers these security topics that are valuable to aspiring pen testers and more:
- Kali Linux VM and its benefits and uses for penetration testing
- Ethical hacking: vocabulary, concepts, and strategies, as well as attack categories, types, and vectors
- Hacker’s tools: search engine, website recon, metagoofil metadata tool, DNS tools, WHOIS, and more
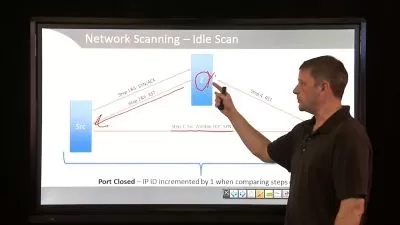
- Network Scanning: overview, methodology, port discovery, stealth idle scanning, vulnerability scanning, and network mapping
- Network technologies: SNMP, NetBios, LDAP, NTP, SMTP, proxy services
- Password cracking: overview, concepts, MITM and sniffing, with demonstration in the lab
- Malware: spyware, buffer overflow, trojans, viruses, detection, analysis, remedies
- Web application security: OWASP, SQL injection, man-in-the-middle, session hijacking
- Cloud computing security, mobile security, Wi-Fi security, and other special topics
Who Should Take White Hat Hacking v10 Training?
This White Hat training is considered expert-level security training, which means it was designed for experienced security professionals. This White Hat Hacking v10 course is valuable for new IT professionals with at least a year of experience with pen testing as well as experienced security professionals looking to validate their security skills.
New or aspiring security professionals. Network security professionals are in high demand these days. Those who are skilled in penetration testing can command a respectable income. Even those with no experience in ethical hacking techniques will gain a lot from our White Hat Hacking v10 training. It’s a great way to develop or accelerate a career as an IT security specialist.
Experienced security professionals. Penetration testers tend to learn a lot on their own. But there is only so much that you can get by self-study. Even experienced pen testers can pick up valuable new information and skills from our White Hat Hacking v10 course. Our coverage of the latest threats and vulnerabilities will help ethical hackers no matter how long they have been in the business.
User Reviews
Rating
Keith Barker
Instructor's CoursesThe best part of being a trainer is making a difference in the life of a student. When a motivated learner and the correct training meet at the right time, the results are amazing.
Keith Barker discovered a love for computers and networking in 1984 and began his IT career in 1985 at Electronic Data Systems (EDS). He has worked with companies including Paramount Pictures, Blue Cross, and several government agencies. Keith loves to teach and spends most of his time creating fun and useful videos for CBT Nuggets.
Certifications: Cisco CCIE (2x), CISSP, Network+, Security+, VMware, Palo Alto, Check Point
Areas of expertise: Networking and Security

CBT Nuggets
View courses CBT Nuggets- language english
- Training sessions 127
- duration 19:56:33
- Release Date 2023/07/17