Understanding Penetration Testing for Beginners - Hands On
Richard Ardelean
3:48:16
Description
Learn Penetration Testing: Discover, Exploit, and Protect! Learn real-world hacking techniques and defend against them!
What You'll Learn?
- Fundamentals of Penetration Testing
- Penetration Testing Phases
- Setting up hacking lab: Kali Linux and VMs
- Hacking Windows and Metasploitable (Linux)
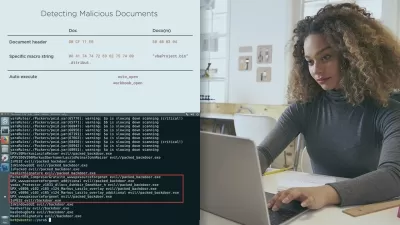
- Reconnaissance
- Metasploit framework for beginners
- Perform network and system scanning
- Nessus vulnerability scanning
- Networking and networking protocols
- Linux Basics and command line interface
- Hacking with ChatGPT
- Privilege escalation
Who is this for?
What You Need to Know?
More details
DescriptionEmbark on Your Cybersecurity Journey: Penetrate, Protect, and Excel in 2023!
Dive into the dynamic world of Penetration Testing, Security Testing, and Ethical Hacking, even with no prior experience. This course is your gateway to understanding the critical aspects of cybersecurity, giving you the tools and confidence to launch your career as a Junior Security Expert. With cybersecurity's growing importance in protecting data against theft and damage, there's no better time to enter this rapidly expanding field.
Why Cybersecurity? Major IT players are escalating their investments to safeguard against hackers, amplifying the demand for skilled Penetration Testers, Security Experts, and White Hat Hackers. Step into a world where your skills not only protect but also command an increasingly attractive salary.
What You'll Gain:
Comprehensive understanding of Penetration Testing, Security Testing, and Ethical Hacking.
Practical knowledge of setting up a hacking lab with Kali Linux and VMs.
Skills to exploit vulnerabilities in Windows and Metasploitable (Linux).
Mastery of network and system scanning, plus the Metasploit framework.
Insight into the critical OWASP Top 10 Vulnerabilities and how to guard against them.
Command over Linux basics and the command line interface.
Innovative techniques in hacking with ChatGPT.
Who Should Enroll:
Aspiring Penetration Testers, Security Experts, and Ethical Hackers.
Career changers eager to enter the IT field, especially in Security Testing.
Anyone looking to acquire a valuable, highly paid skill.
Why This Course?
No prior experience required! You'll be guided step-by-step through each topic.
It's not just a course; it's a positive life change, offering entry into the lucrative IT security field.
Enjoy support and answers throughout your learning journey, plus lifetime access and a certificate of completion.
Your Commitment:
This course demands initial effort, like all valuable pursuits in life. But imagine the satisfaction when you start making tangible, positive changes in your career and skills.
Who this course is for:
- Anyone interested in penetration testing / ethical hacking
- Anyone with the drive to learn
Embark on Your Cybersecurity Journey: Penetrate, Protect, and Excel in 2023!
Dive into the dynamic world of Penetration Testing, Security Testing, and Ethical Hacking, even with no prior experience. This course is your gateway to understanding the critical aspects of cybersecurity, giving you the tools and confidence to launch your career as a Junior Security Expert. With cybersecurity's growing importance in protecting data against theft and damage, there's no better time to enter this rapidly expanding field.
Why Cybersecurity? Major IT players are escalating their investments to safeguard against hackers, amplifying the demand for skilled Penetration Testers, Security Experts, and White Hat Hackers. Step into a world where your skills not only protect but also command an increasingly attractive salary.
What You'll Gain:
Comprehensive understanding of Penetration Testing, Security Testing, and Ethical Hacking.
Practical knowledge of setting up a hacking lab with Kali Linux and VMs.
Skills to exploit vulnerabilities in Windows and Metasploitable (Linux).
Mastery of network and system scanning, plus the Metasploit framework.
Insight into the critical OWASP Top 10 Vulnerabilities and how to guard against them.
Command over Linux basics and the command line interface.
Innovative techniques in hacking with ChatGPT.
Who Should Enroll:
Aspiring Penetration Testers, Security Experts, and Ethical Hackers.
Career changers eager to enter the IT field, especially in Security Testing.
Anyone looking to acquire a valuable, highly paid skill.
Why This Course?
No prior experience required! You'll be guided step-by-step through each topic.
It's not just a course; it's a positive life change, offering entry into the lucrative IT security field.
Enjoy support and answers throughout your learning journey, plus lifetime access and a certificate of completion.
Your Commitment:
This course demands initial effort, like all valuable pursuits in life. But imagine the satisfaction when you start making tangible, positive changes in your career and skills.
Who this course is for:
- Anyone interested in penetration testing / ethical hacking
- Anyone with the drive to learn
User Reviews
Rating
Richard Ardelean
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 50
- duration 3:48:16
- Release Date 2024/04/23