Ultimate Guide to IT Regulatory Compliance Management
Nour | Cyvitrix Train
8:17:34
Description
IT Compliance Regulatory Compliance Management, Governance Risk and Compliance GRC Introduction Course for IT/Non IT
What You'll Learn?
- Learn the fundamental principles of GRC and why it is critical in today's business environment.
- Understand how GRC integrates with IT functions to align with business objectives and ensure organizational success.
- Explore the relationship between IT functions and business operations, and how to effectively integrate them to support overall business goals.
- Gain insights into the importance of information security and cybersecurity in the context of GRC.
- Understand the structures and processes that define corporate, IT, and security governance.
- Learn how to develop and implement effective governance strategies, policies, and standards.
- Acquire in-depth knowledge of the risk management process, including risk identification, assessment, evaluation, and treatment.
- Understand the purpose of gap analysis and the distinctions between laws, acts, and regulations.
- Gain a thorough understanding of the auditing process, including different types of audits and the role of audit evidence.
- Understand best practices for governance, risk management, and compliance to enhance your organization's resilience.
- Learn about common challenges and biases in strategy development and how to navigate them.
- Explore the role of artificial intelligence in GRC, including AI usage policies and AI-driven auditing practices.
- Identify and understand the roles and responsibilities of senior leaders in security, risk, compliance, and IT.
Who is this for?
What You Need to Know?
More details
DescriptionWelcome to the Ultimate Guide to IT Regulatory Compliance Management GRC!
In today's fast-paced digital world, businesses must adhere to a myriad of regulatory and compliance standards to protect their operations and maintain trust with their stakeholders. This comprehensive course is designed to equip you with the essential knowledge and skills needed to master IT Regulatory Compliance Management, ensuring that your organization not only meets but exceeds the necessary requirements.
What Will You Learn?
Section 1: Introduction
1.1 - Why GRC is Crucial in Today's Business?
Understand the significance of Governance, Risk, and Compliance (GRC) in modern business environments.
1.2 - IT Functions and Integration with Business
Explore how IT functions align with business goals for seamless operations.
1.3 - Information Security & Cybersecurity
Delve into the essentials of safeguarding information in a digital landscape.
1.4 - Crowd Strike Issue in 2024, and Possible Proactive Solutions - Example
Learn from real-world examples to proactively manage cybersecurity threats.
1.5 - Understand Technical Infrastructure in Business
Grasp the complexities of technical infrastructure within business settings.
1.6 - The Three Lines of Defence Model!
Discover the three lines of defense model for risk management.
1.7 - Senior Roles in Security, Risk, Compliance and IT!
Identify key senior roles and their responsibilities in GRC.
Section 2: Corporate Governance, IT Governance & Security Governance
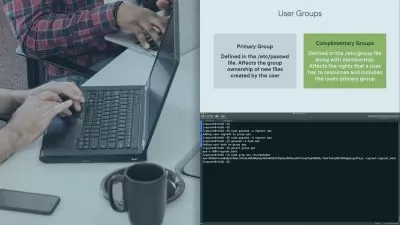
2.1 - Organizational Structure
Understand the foundational elements of corporate governance.
2.2 - Governance and Management Functions
Differentiate between governance and management roles.
2.3 - Governance Committees and their Importance
Learn about the critical role of governance committees.
2.4 - The Strategy and Goals and Objectives and Business Alignment
Align business strategies with governance objectives.
2.5 - The Security Governance Importance
Recognize the importance of security governance.
2.6 - Strategy Implementation Constrains
Identify constraints in strategy implementation.
2.7 - Strategy Development Pitfalls and Navigating Common Biases
Navigate common biases in strategy development.
2.8 - Policies
Understand the role of policies in governance.
2.9 - Policy Development Process and Key Recommendations
Learn best practices for developing effective policies.
2.10 - Top Down and Bottom UP!
Explore top-down and bottom-up approaches in governance.
2.11 - Example of Policies (AUP, CLEAR DESK PHYSICAL)
Examine real-world policy examples.
2.12 - Example of Policies (Network Access, BYOD)
Explore additional policy examples relevant to IT governance.
2.13 - Standards
Understand the significance of standards in IT governance.
2.14 - Procedures and Guidelines
Learn how procedures and guidelines support governance frameworks.
2.15 - Artificial Intelligence Usage Policies
Delve into the emerging field of AI governance.
2.16 - Building AI Strategy
Build a robust AI strategy for your organization.
Section 3: Risk Management
3.1 - What are we trying to Protect?
Identify critical assets and their protection requirements.
3.2 - Key Terminologies Related to Security - Must Be Known
Familiarize yourself with key security terminologies.
3.3 - Why Security is Crucial, what is the Security Objective
Understand the core objectives of security in risk management.
3.4 - Security Attacks Typical Flow - Cyber Attack Abstraction
Analyze the flow of typical cyber-attacks.
3.5 - Controls and How it can be used
Explore various security controls and their applications.
3.6 - Example of Controls, Security, IT and General Controls
Review examples of security controls in practice.
3.7 - Control Selection and Evaluation and Best Practices
Learn best practices for selecting and evaluating controls.
3.8 - The Need for Risk Management, Risk Management Process
Understand the comprehensive risk management process.
3.9 - Risk Assessment - Identification Phase
Delve into the identification phase of risk assessment.
3.10 - Risk Assessment - Analysis Phase
Analyze risks effectively in the analysis phase.
3.11 - Risk Management Process - Evaluation and Treatment Phase
Learn how to evaluate and treat risks.
3.12 - Risk Reporting and Management
Master the art of risk reporting and management.
3.13 - Key Risk Management Frameworks Overview
Overview of key risk management frameworks.
3.14 - NIST RMF - SP800-37
Introduction to the NIST Risk Management Framework.
3.15 - COSO Framework Overview
Understand the COSO ERM Framework.
3.16 - ISO27005, ISO31000 ERM Overview
Learn about ISO 27005 and ISO 31000 frameworks.
3.17 - COBIT & Risk Management
Explore how COBIT integrates with risk management.
Section 4: Compliance and Regulatory and Standard Needs
4.1 - Key Regulations and Standards
Understand the key regulations and standards in compliance management.
4.2 - The Purpose of Gap Analysis Process
Learn the importance of gap analysis in compliance.
4.3 - Law vs Act vs Regulation
Differentiate between laws, acts, and regulations.
4.4 - Federal Laws Examples - 1
Explore examples of federal laws relevant to IT compliance.
4.5 - Federal Laws Examples - 2
Delve deeper into federal law examples.
4.6 - Data Privacy Overview
Understand the fundamentals of data privacy.
4.7 - Data Governance
Learn about data governance and its significance.
4.8 - Data Governance Roles
Identify key roles in data governance.
4.9 - Data Privacy Controls and Documentation
Master the controls and documentation needed for data privacy.
Section 5: Auditing and Monitoring and Performance Evaluation
5.1 - What is Auditing?
Gain a clear understanding of the auditing process.
5.2 - Types of Audit - Internal, External
Differentiate between internal and external audits.
5.3 - Typical Audit Process
Learn the steps involved in a typical audit process.
5.4 - Understand Audit Evidence and Chain of Custody and Making Evidence Admissible
Master the handling of audit evidence and chain of custody.
5.5 - Regulatory Compliance Impact and Need for Compliance Role
Explore the impact of regulatory compliance on organizations.
5.6 - Quality Assurance and Quality Control Roles in Organization
Understand the roles of QA and QC in performance evaluation.
5.7 - AI & Auditing
Explore the role of AI in modern auditing practices.
5.8 - Performance Evaluation Models
Learn about various models for performance evaluation.
5.9 - Metrics and Smart Metrics Role in Performance Review
Understand the role of smart metrics in performance reviews.
5.10 - Maturity Assessment Models
Learn how to assess organizational maturity effectively.
Why Enroll in This Course?
Comprehensive Curriculum: Covers all critical aspects of IT Regulatory Compliance Management, from risk management to auditing and performance evaluation.
Real-World Examples: Learn from actual case studies and examples.
Expert Instructor: Get taught by an experienced professional in the field.
Flexible Learning: Access course materials anytime, anywhere, and learn at your own pace.
Certifications and Career Advancement: Enhance your skills and knowledge to advance your career in IT compliance, governance, and risk management.
Who Should Take This Course?
IT Professionals
Compliance Officers
Risk Managers
Auditors
Business Leaders
Anyone interested in mastering IT Regulatory Compliance Management
Get Started Today!
Enroll now and take the first step toward mastering IT Regulatory Compliance Management. Equip yourself with the knowledge and skills to drive compliance and governance excellence in your organization.
Join thousands of professionals who have transformed their careers with our expert-led courses.
Take control of your career and ensure your organization’s compliance with this comprehensive guide. Don’t miss out on the opportunity to learn from the best and become a leader in IT Regulatory Compliance Management!
Who this course is for:
- Systems Administrators, IT Managers, and IT Directors who want to deepen their understanding of how IT governance aligns with business objectives and regulatory requirements.
- Cybersecurity Professionals looking to expand their knowledge of compliance and risk management in the context of information security.
- Compliance Officers, Professionals responsible for ensuring that their organizations comply with relevant laws, regulations, and standards.
- Individuals looking to strengthen their ability to manage and implement compliance frameworks across different sectors.
- Risk Analysts and Risk Managers who want to enhance their skills in identifying, assessing, and mitigating risks within an organization.
- Internal and External Auditors who need to understand the IT compliance landscape to conduct effective audits.
- CIOs, CTOs, CISOs, and other C-suite executives responsible for driving governance and compliance initiatives within their organizations.
- Professionals involved in managing projects related to IT governance, risk management, or compliance.
- Students and recent graduates looking to start a career in IT governance, risk management, or compliance.
- Individuals from non-IT backgrounds who are transitioning into roles related to GRC and need a foundational understanding of these concepts.
- Professionals across various industries who want to gain a comprehensive understanding of IT Regulatory Compliance Management to enhance their career prospects.
- Those who are curious about the intersection of IT, governance, risk management, and compliance, and wish to explore it in depth.
Welcome to the Ultimate Guide to IT Regulatory Compliance Management GRC!
In today's fast-paced digital world, businesses must adhere to a myriad of regulatory and compliance standards to protect their operations and maintain trust with their stakeholders. This comprehensive course is designed to equip you with the essential knowledge and skills needed to master IT Regulatory Compliance Management, ensuring that your organization not only meets but exceeds the necessary requirements.
What Will You Learn?
Section 1: Introduction
1.1 - Why GRC is Crucial in Today's Business?
Understand the significance of Governance, Risk, and Compliance (GRC) in modern business environments.
1.2 - IT Functions and Integration with Business
Explore how IT functions align with business goals for seamless operations.
1.3 - Information Security & Cybersecurity
Delve into the essentials of safeguarding information in a digital landscape.
1.4 - Crowd Strike Issue in 2024, and Possible Proactive Solutions - Example
Learn from real-world examples to proactively manage cybersecurity threats.
1.5 - Understand Technical Infrastructure in Business
Grasp the complexities of technical infrastructure within business settings.
1.6 - The Three Lines of Defence Model!
Discover the three lines of defense model for risk management.
1.7 - Senior Roles in Security, Risk, Compliance and IT!
Identify key senior roles and their responsibilities in GRC.
Section 2: Corporate Governance, IT Governance & Security Governance
2.1 - Organizational Structure
Understand the foundational elements of corporate governance.
2.2 - Governance and Management Functions
Differentiate between governance and management roles.
2.3 - Governance Committees and their Importance
Learn about the critical role of governance committees.
2.4 - The Strategy and Goals and Objectives and Business Alignment
Align business strategies with governance objectives.
2.5 - The Security Governance Importance
Recognize the importance of security governance.
2.6 - Strategy Implementation Constrains
Identify constraints in strategy implementation.
2.7 - Strategy Development Pitfalls and Navigating Common Biases
Navigate common biases in strategy development.
2.8 - Policies
Understand the role of policies in governance.
2.9 - Policy Development Process and Key Recommendations
Learn best practices for developing effective policies.
2.10 - Top Down and Bottom UP!
Explore top-down and bottom-up approaches in governance.
2.11 - Example of Policies (AUP, CLEAR DESK PHYSICAL)
Examine real-world policy examples.
2.12 - Example of Policies (Network Access, BYOD)
Explore additional policy examples relevant to IT governance.
2.13 - Standards
Understand the significance of standards in IT governance.
2.14 - Procedures and Guidelines
Learn how procedures and guidelines support governance frameworks.
2.15 - Artificial Intelligence Usage Policies
Delve into the emerging field of AI governance.
2.16 - Building AI Strategy
Build a robust AI strategy for your organization.
Section 3: Risk Management
3.1 - What are we trying to Protect?
Identify critical assets and their protection requirements.
3.2 - Key Terminologies Related to Security - Must Be Known
Familiarize yourself with key security terminologies.
3.3 - Why Security is Crucial, what is the Security Objective
Understand the core objectives of security in risk management.
3.4 - Security Attacks Typical Flow - Cyber Attack Abstraction
Analyze the flow of typical cyber-attacks.
3.5 - Controls and How it can be used
Explore various security controls and their applications.
3.6 - Example of Controls, Security, IT and General Controls
Review examples of security controls in practice.
3.7 - Control Selection and Evaluation and Best Practices
Learn best practices for selecting and evaluating controls.
3.8 - The Need for Risk Management, Risk Management Process
Understand the comprehensive risk management process.
3.9 - Risk Assessment - Identification Phase
Delve into the identification phase of risk assessment.
3.10 - Risk Assessment - Analysis Phase
Analyze risks effectively in the analysis phase.
3.11 - Risk Management Process - Evaluation and Treatment Phase
Learn how to evaluate and treat risks.
3.12 - Risk Reporting and Management
Master the art of risk reporting and management.
3.13 - Key Risk Management Frameworks Overview
Overview of key risk management frameworks.
3.14 - NIST RMF - SP800-37
Introduction to the NIST Risk Management Framework.
3.15 - COSO Framework Overview
Understand the COSO ERM Framework.
3.16 - ISO27005, ISO31000 ERM Overview
Learn about ISO 27005 and ISO 31000 frameworks.
3.17 - COBIT & Risk Management
Explore how COBIT integrates with risk management.
Section 4: Compliance and Regulatory and Standard Needs
4.1 - Key Regulations and Standards
Understand the key regulations and standards in compliance management.
4.2 - The Purpose of Gap Analysis Process
Learn the importance of gap analysis in compliance.
4.3 - Law vs Act vs Regulation
Differentiate between laws, acts, and regulations.
4.4 - Federal Laws Examples - 1
Explore examples of federal laws relevant to IT compliance.
4.5 - Federal Laws Examples - 2
Delve deeper into federal law examples.
4.6 - Data Privacy Overview
Understand the fundamentals of data privacy.
4.7 - Data Governance
Learn about data governance and its significance.
4.8 - Data Governance Roles
Identify key roles in data governance.
4.9 - Data Privacy Controls and Documentation
Master the controls and documentation needed for data privacy.
Section 5: Auditing and Monitoring and Performance Evaluation
5.1 - What is Auditing?
Gain a clear understanding of the auditing process.
5.2 - Types of Audit - Internal, External
Differentiate between internal and external audits.
5.3 - Typical Audit Process
Learn the steps involved in a typical audit process.
5.4 - Understand Audit Evidence and Chain of Custody and Making Evidence Admissible
Master the handling of audit evidence and chain of custody.
5.5 - Regulatory Compliance Impact and Need for Compliance Role
Explore the impact of regulatory compliance on organizations.
5.6 - Quality Assurance and Quality Control Roles in Organization
Understand the roles of QA and QC in performance evaluation.
5.7 - AI & Auditing
Explore the role of AI in modern auditing practices.
5.8 - Performance Evaluation Models
Learn about various models for performance evaluation.
5.9 - Metrics and Smart Metrics Role in Performance Review
Understand the role of smart metrics in performance reviews.
5.10 - Maturity Assessment Models
Learn how to assess organizational maturity effectively.
Why Enroll in This Course?
Comprehensive Curriculum: Covers all critical aspects of IT Regulatory Compliance Management, from risk management to auditing and performance evaluation.
Real-World Examples: Learn from actual case studies and examples.
Expert Instructor: Get taught by an experienced professional in the field.
Flexible Learning: Access course materials anytime, anywhere, and learn at your own pace.
Certifications and Career Advancement: Enhance your skills and knowledge to advance your career in IT compliance, governance, and risk management.
Who Should Take This Course?
IT Professionals
Compliance Officers
Risk Managers
Auditors
Business Leaders
Anyone interested in mastering IT Regulatory Compliance Management
Get Started Today!
Enroll now and take the first step toward mastering IT Regulatory Compliance Management. Equip yourself with the knowledge and skills to drive compliance and governance excellence in your organization.
Join thousands of professionals who have transformed their careers with our expert-led courses.
Take control of your career and ensure your organization’s compliance with this comprehensive guide. Don’t miss out on the opportunity to learn from the best and become a leader in IT Regulatory Compliance Management!
Who this course is for:
- Systems Administrators, IT Managers, and IT Directors who want to deepen their understanding of how IT governance aligns with business objectives and regulatory requirements.
- Cybersecurity Professionals looking to expand their knowledge of compliance and risk management in the context of information security.
- Compliance Officers, Professionals responsible for ensuring that their organizations comply with relevant laws, regulations, and standards.
- Individuals looking to strengthen their ability to manage and implement compliance frameworks across different sectors.
- Risk Analysts and Risk Managers who want to enhance their skills in identifying, assessing, and mitigating risks within an organization.
- Internal and External Auditors who need to understand the IT compliance landscape to conduct effective audits.
- CIOs, CTOs, CISOs, and other C-suite executives responsible for driving governance and compliance initiatives within their organizations.
- Professionals involved in managing projects related to IT governance, risk management, or compliance.
- Students and recent graduates looking to start a career in IT governance, risk management, or compliance.
- Individuals from non-IT backgrounds who are transitioning into roles related to GRC and need a foundational understanding of these concepts.
- Professionals across various industries who want to gain a comprehensive understanding of IT Regulatory Compliance Management to enhance their career prospects.
- Those who are curious about the intersection of IT, governance, risk management, and compliance, and wish to explore it in depth.
User Reviews
Rating
Nour | Cyvitrix Train
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 67
- duration 8:17:34
- Release Date 2024/10/06