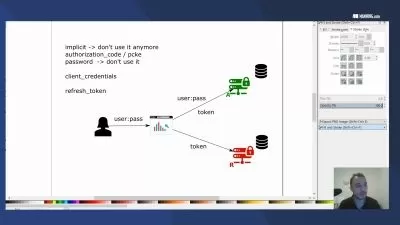
Ultimate Cybersecurity: Uncovering Hacker Strategies
Daniel Isbell
2:40:54
Description
Mastering Defense: Learn Fundamentals, Hacker Tactics, Security Best Practices, and Legal Frameworks in Cybersecurity
What You'll Learn?
- Understanding Cybersecurity Fundamentals: Students will gain a strong foundation in the core principles of cybersecurity.
- Exploring Hacker Mindset and Techniques: This course will delve into the psychology of hackers, their motivations, and common tactics.
- Uncovering Vulnerabilities and Threat Modeling: Students will learn how to identify vulnerabilities in a system and understand how these can be exploited.
- Implementing Security Measures and Protocols: Students will be taught how to design, implement, and maintain effective security measures and protocols.
- Incident Response and Disaster Recovery Planning: In this section, students will learn how to respond effectively to a security incident.
Who is this for?
What You Need to Know?
More details
DescriptionIn the course "Ultimate Cybersecurity: Uncovering Hacker Strategies," you will embark on a comprehensive exploration of the rapidly evolving world of cybersecurity. This course is designed to arm you with a deep understanding of the critical aspects of cybersecurity, whether you're an aspiring professional, an IT specialist, or an entrepreneur safeguarding your business.
The course begins by grounding you in the fundamentals of cybersecurity, ensuring you have a solid foundation on which to build your knowledge. From there, you'll delve into the mind of a hacker, learning about common strategies and tactics used in cyber attacks.
But understanding the threat is just the start. You'll discover best practices in cybersecurity, learning how to implement effective security measures and protocols to protect your digital assets. You'll also delve into the crucial area of incident response and recovery, gaining knowledge on how to limit damage, recover lost data, and prevent future attacks.
A crucial aspect of modern cybersecurity is navigating the complex landscape of laws, regulations, and compliance. This course will guide you through this often complex area, helping you understand the legal and ethical implications of cybersecurity.
Finally, you'll get hands-on with cybersecurity tools and resources, equipping you with practical skills and experience to tackle real-world cybersecurity challenges. The course concludes with a wealth of supplementary materials for you to explore and continue your learning journey.
Whether you're just starting out in the field of cybersecurity, or looking to upgrade your existing skills, this course provides a comprehensive, engaging, and practical exploration of the world of cybersecurity. Join us as we uncover hacker strategies and master the art of digital defense.
Who this course is for:
- Aspiring Cybersecurity Professionals: Individuals who are interested in pursuing a career in cybersecurity will find this course invaluable.
- IT Professionals: IT professionals looking to expand their knowledge base and skill set can benefit from this course.
- Entrepreneurs and Business Owners: Entrepreneurs and business owners who want to understand cybersecurity threats and how to protect their business assets online will find this course beneficial.
- Students Studying Computer Science or Related Fields: This course is also suitable for students in computer science or related fields who wish to broaden their understanding of cybersecurity.
In the course "Ultimate Cybersecurity: Uncovering Hacker Strategies," you will embark on a comprehensive exploration of the rapidly evolving world of cybersecurity. This course is designed to arm you with a deep understanding of the critical aspects of cybersecurity, whether you're an aspiring professional, an IT specialist, or an entrepreneur safeguarding your business.
The course begins by grounding you in the fundamentals of cybersecurity, ensuring you have a solid foundation on which to build your knowledge. From there, you'll delve into the mind of a hacker, learning about common strategies and tactics used in cyber attacks.
But understanding the threat is just the start. You'll discover best practices in cybersecurity, learning how to implement effective security measures and protocols to protect your digital assets. You'll also delve into the crucial area of incident response and recovery, gaining knowledge on how to limit damage, recover lost data, and prevent future attacks.
A crucial aspect of modern cybersecurity is navigating the complex landscape of laws, regulations, and compliance. This course will guide you through this often complex area, helping you understand the legal and ethical implications of cybersecurity.
Finally, you'll get hands-on with cybersecurity tools and resources, equipping you with practical skills and experience to tackle real-world cybersecurity challenges. The course concludes with a wealth of supplementary materials for you to explore and continue your learning journey.
Whether you're just starting out in the field of cybersecurity, or looking to upgrade your existing skills, this course provides a comprehensive, engaging, and practical exploration of the world of cybersecurity. Join us as we uncover hacker strategies and master the art of digital defense.
Who this course is for:
- Aspiring Cybersecurity Professionals: Individuals who are interested in pursuing a career in cybersecurity will find this course invaluable.
- IT Professionals: IT professionals looking to expand their knowledge base and skill set can benefit from this course.
- Entrepreneurs and Business Owners: Entrepreneurs and business owners who want to understand cybersecurity threats and how to protect their business assets online will find this course beneficial.
- Students Studying Computer Science or Related Fields: This course is also suitable for students in computer science or related fields who wish to broaden their understanding of cybersecurity.
User Reviews
Rating
Daniel Isbell
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 50
- duration 2:40:54
- Release Date 2023/08/01