The Secrets of Nmap: Master Network Scanning and Hacking
Mark de Moras
1:57:49
Description
Become an expert at Nmap to discovery network vulnerabilities using Kali Linux and Wireshark!
What You'll Learn?
- Gain essential knowledge to become an ethical hacker, SOC analyst, penetration tester, and cybersecurity expert
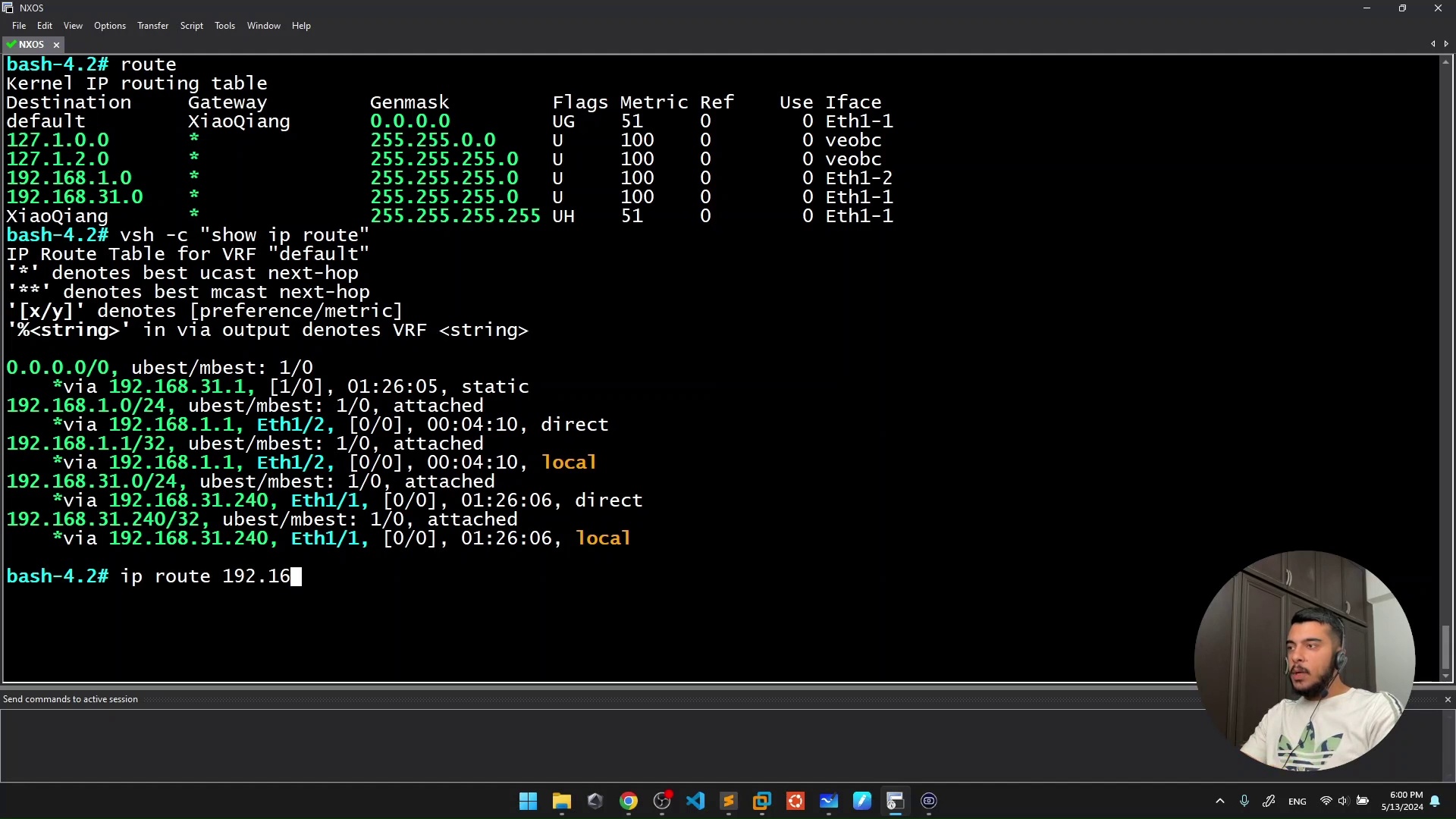
- Enumerate and scan networks to discovery security vulnerabilities on open services using Wireshark, Kali Linux, and Nmap
- Learn to identify vulnerable service and operating system versions
- Learn various TCP flags and scans and how they work with Wireshark
- Learn the fundamentals of the Nmap Scripting Engine, Zenmap, and WebMap
- Understand and utilize Nmap's firewall/IDS evasion techniques
- Learn to interpret Nmap output for effective vulnerability analysis
- Integrate Nmap with other security tools like Metasploit for exploitation
Who is this for?
What You Need to Know?
More details
DescriptionUnlock the full potential of Nmap with this comprehensive course! Learn port scanning, detecting vulnerable services, fingerprinting operating systems, bypass security systems and utilizing Nmap Timing Templates to master every aspect of Nmap.
Dive deep into Nmap's extensive flag options and scanning capabilities. We will start by building a hacking lab and understanding Nmap syntax, then progress to advanced techniques using various Nmap flags.
But that's not all! You will learn to analyze scan types at the packet level using Wireshark, identifying TCP headers and flags set by Nmap in real time.
In addition to mastering Nmap, you will gain valuable insights into network security practices and principles. Understanding Nmap means knowing the tool and understanding the underlying concepts of network scanning and reconnaissance.
This course offers hands-on, practical examples to ensure you're learning theory and applying it in real-world scenarios. Immediately implement your newfound Nmap skills in professional or personal projects.
Join this exciting journey to become an Nmap expert and elevate your cybersecurity skills! Nmap is essential for aspiring ethical hackers or network professionals. Enroll now to unleash the full power of Nmap! Plus, all videos are byte-sized for the best learning experience, making complex information easier to digest.
Who this course is for:
- This course is for anyone interested in learning how to scan networks using Nmap and perform ethical hacking.
Unlock the full potential of Nmap with this comprehensive course! Learn port scanning, detecting vulnerable services, fingerprinting operating systems, bypass security systems and utilizing Nmap Timing Templates to master every aspect of Nmap.
Dive deep into Nmap's extensive flag options and scanning capabilities. We will start by building a hacking lab and understanding Nmap syntax, then progress to advanced techniques using various Nmap flags.
But that's not all! You will learn to analyze scan types at the packet level using Wireshark, identifying TCP headers and flags set by Nmap in real time.
In addition to mastering Nmap, you will gain valuable insights into network security practices and principles. Understanding Nmap means knowing the tool and understanding the underlying concepts of network scanning and reconnaissance.
This course offers hands-on, practical examples to ensure you're learning theory and applying it in real-world scenarios. Immediately implement your newfound Nmap skills in professional or personal projects.
Join this exciting journey to become an Nmap expert and elevate your cybersecurity skills! Nmap is essential for aspiring ethical hackers or network professionals. Enroll now to unleash the full power of Nmap! Plus, all videos are byte-sized for the best learning experience, making complex information easier to digest.
Who this course is for:
- This course is for anyone interested in learning how to scan networks using Nmap and perform ethical hacking.
User Reviews
Rating
Mark de Moras
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 31
- duration 1:57:49
- Release Date 2024/07/26