The Complete Mobile Ethical Hacking Course
Codestars • over 2 million students worldwide!,Atil Samancioglu
26:45:39
Description
Learn how hackers attack phones, mobile applications and mobile devices with latest technology and protect yourself!
What You'll Learn?
- Mobile Cyber Security for Mobile Applications & Devices
- Mobile Applications and Games Penetration Tests
- Mobile Device Penetration Tests
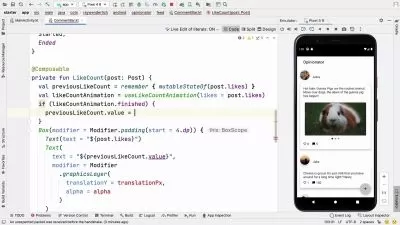
- Android & iOS Fundamentals
- Java & Swift Fundamentals
- Ethical Hacking Fundamentals
- Reverse Engineering
- Mobile Application Development Fundamentals
Who is this for?
What You Need to Know?
More details
DescriptionWelcome to Mobile Ethical Hacking From Scratch online training!
We are going to start from scratch in this course and aim to learn all the details related to Ethical Hacking for Mobile Applications & Mobile Devices. Without any need of prior knowledge you will understand how hackers attack mobile applications & devices and protect yourself against these attacks. You will build your own hacking lab on your computer so that you can practice all the things that we are going to learn in this course.
Every student who wants to build their own server for APIÂ Pentesting section will be given free 25$Â - 100$Â credits from Digital Ocean.
This course is given by Atil Samancioglu who has more than 250.000 students on Udemy. Atil teaches Cyber Security &Â Mobile Application Development and he is also Mobile Application Development Instructor in one of the most prestigious universities in Europe.
You can see some of the topics that we are going to cover through the course:
Backdoor for Mobile Devices
Reverse Engineering
Game Hacking
App Manipulation
Network Monitoring
Linux Fundamentals
Firebase Hacking &Â Firebase Security
Root &Â JailBreak Operations
Dalvik Bytecode
Cycript
Jadx
Apktool
CTFÂ Practices
Android Mobile Application Fundamentals
iOSÂ Mobile Application Fundamentals
Java Fundamentals
Swift Fundamentals
APIÂ Pentesting
Content
This course is ideal for students who are willing to learn mobile device and mobile application penetration testing and ethical hacking. Whether you are a professional developer or just a beginner it does not matter. We are going to start from scratch and aim to learn all the details. At the end of the course you will be able to understand the vulnerabilities in real world and learn how to fix them.
Throughout the course we are not going to focus on pure theory. We are going to practice everything we learn with special apps and challenges specifically created for this course only! We are going to have real time hacking exercise.
Important Notice:Â You should use all the information in this course in legal boundaries. Please refer to your local cyber security laws and make sure you are on the Ethical Hacking side. All students taking this course must commit to this rule.
Who this course is for:
- Students who want to learn about mobile ethical hacking
- Students who want to learn about mobile application penetration testing
- Mobile developers who want to learn about safe development
- Cyber security specialists looking forward to expand their horizon into mobile world
Welcome to Mobile Ethical Hacking From Scratch online training!
We are going to start from scratch in this course and aim to learn all the details related to Ethical Hacking for Mobile Applications & Mobile Devices. Without any need of prior knowledge you will understand how hackers attack mobile applications & devices and protect yourself against these attacks. You will build your own hacking lab on your computer so that you can practice all the things that we are going to learn in this course.
Every student who wants to build their own server for APIÂ Pentesting section will be given free 25$Â - 100$Â credits from Digital Ocean.
This course is given by Atil Samancioglu who has more than 250.000 students on Udemy. Atil teaches Cyber Security &Â Mobile Application Development and he is also Mobile Application Development Instructor in one of the most prestigious universities in Europe.
You can see some of the topics that we are going to cover through the course:
Backdoor for Mobile Devices
Reverse Engineering
Game Hacking
App Manipulation
Network Monitoring
Linux Fundamentals
Firebase Hacking &Â Firebase Security
Root &Â JailBreak Operations
Dalvik Bytecode
Cycript
Jadx
Apktool
CTFÂ Practices
Android Mobile Application Fundamentals
iOSÂ Mobile Application Fundamentals
Java Fundamentals
Swift Fundamentals
APIÂ Pentesting
Content
This course is ideal for students who are willing to learn mobile device and mobile application penetration testing and ethical hacking. Whether you are a professional developer or just a beginner it does not matter. We are going to start from scratch and aim to learn all the details. At the end of the course you will be able to understand the vulnerabilities in real world and learn how to fix them.
Throughout the course we are not going to focus on pure theory. We are going to practice everything we learn with special apps and challenges specifically created for this course only! We are going to have real time hacking exercise.
Important Notice:Â You should use all the information in this course in legal boundaries. Please refer to your local cyber security laws and make sure you are on the Ethical Hacking side. All students taking this course must commit to this rule.
Who this course is for:
- Students who want to learn about mobile ethical hacking
- Students who want to learn about mobile application penetration testing
- Mobile developers who want to learn about safe development
- Cyber security specialists looking forward to expand their horizon into mobile world
User Reviews
Rating
Codestars • over 2 million students worldwide!
Instructor's CoursesAtil Samancioglu
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 188
- duration 26:45:39
- English subtitles has
- Release Date 2023/06/24