The Complete ISO/IES 27001 Information Security Management
Petar Dimov
5:27:53
Description
Master ISO 27001: Secure, Comply, Protect
What You'll Learn?
- Master ISO 27001 Significance: Understand ISO 27001's role in information security, its growth, and its importance in ISMS.
- Implement Security Practices: Learn a systematic approach for securing enterprise data, preserving confidentiality, integrity, and availability.
- Ensure Regulatory Compliance: Discover how ISO 27001 aids in meeting GDPR and NIS regulations, aligning with legal requirements.
- Boost Cybersecurity Resilience: Learn to enhance resilience against cyber threats, safeguarding data integrity, availability, and confidentiality.
Who is this for?
What You Need to Know?
More details
DescriptionIn today's digitally driven world, information security is a paramount concern for organizations of all sizes. The ISO 27001 Information Security Management standard has emerged as a vital framework to protect valuable data and ensure compliance with regulatory requirements. If you're looking to become a proficient information security practitioner or advance your career in this field, this comprehensive course is your roadmap to success.
Master ISO 27001: Secure, Comply, Protect
With a focus on practicality and real-world application, "The Complete ISO / IES 27001 Information Security Management Course" equips you with the skills and knowledge needed to implement ISO 27001 effectively. Whether you're new to information security or an experienced professional, this course is designed to empower you to secure, comply, and protect.
Key Course Areas:
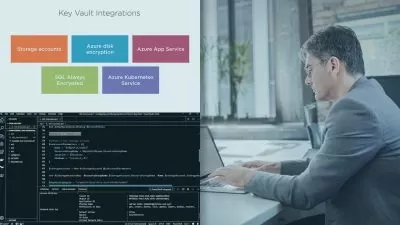
Security Framework Implementation: Explore a systematic approach that covers people, processes, and technology. Learn how to enhance and safeguard enterprise information, preserving confidentiality, integrity, and availability.
Regulatory Compliance and Legal Requirements: Understand how ISO 27001 can help your organization meet essential regulations like the GDPR and NIS regulations. Discover best practices to align your information security management with legal standards.
Risk Management and Resilience: Gain the knowledge and skills to enhance your company's resilience against cyber threats and attacks. Protect critical assets and ensure the ongoing availability, integrity, and confidentiality of data, whether stored digitally or in the cloud.
Data Confidentiality, Integrity, and Availability: Delve into the core principles of ISO 27001, ensuring that authorized restrictions on access and disclosure are maintained. Safeguard against improper information modification or destruction while ensuring timely and reliable data access.
What You'll Achieve:
By the end of this course, you'll not only master ISO 27001 but also be well-prepared to apply it in practice. You'll become a crucial asset to your organization, capable of securing sensitive information, achieving compliance, and enhancing cybersecurity resilience.
Join us today, and let's embark on this exciting journey to safeguarding information, securing data integrity, and ensuring the continuity of essential information assets. Enroll now and become a master in information security management with ISO 27001.
Who this course is for:
- Information Security Enthusiasts: If you're passionate about information security and eager to deepen your knowledge in ISO 27001, this course is for you. Whether you're just starting out or looking to enhance your expertise, you'll find valuable insights here.
- IT Professionals: IT managers, network administrators, and professionals involved in data security and risk management will benefit from this course. It's an excellent resource for those seeking to align their practices with international standards.
- Business Owners and Managers: For entrepreneurs, small business owners, or managers responsible for information security, this course offers essential guidance on implementing ISO 27001 to safeguard your organization's data and meet legal requirements.
- Compliance and Risk Management Specialists: If you're in a role that requires ensuring regulatory compliance and managing cybersecurity risks, this course will equip you with the tools and knowledge needed to excel in your responsibilities.
- Students and Graduates: Information security is a field with vast career opportunities. Students and recent graduates aspiring to enter this field or enhance their academic knowledge will find this course to be a valuable resource.
- Anyone Interested in Information Security: Whether you're a beginner exploring the world of information security or a professional looking to refresh your skills and knowledge, this course provides comprehensive insights and practical guidance for all curious minds.
In today's digitally driven world, information security is a paramount concern for organizations of all sizes. The ISO 27001 Information Security Management standard has emerged as a vital framework to protect valuable data and ensure compliance with regulatory requirements. If you're looking to become a proficient information security practitioner or advance your career in this field, this comprehensive course is your roadmap to success.
Master ISO 27001: Secure, Comply, Protect
With a focus on practicality and real-world application, "The Complete ISO / IES 27001 Information Security Management Course" equips you with the skills and knowledge needed to implement ISO 27001 effectively. Whether you're new to information security or an experienced professional, this course is designed to empower you to secure, comply, and protect.
Key Course Areas:
Security Framework Implementation: Explore a systematic approach that covers people, processes, and technology. Learn how to enhance and safeguard enterprise information, preserving confidentiality, integrity, and availability.
Regulatory Compliance and Legal Requirements: Understand how ISO 27001 can help your organization meet essential regulations like the GDPR and NIS regulations. Discover best practices to align your information security management with legal standards.
Risk Management and Resilience: Gain the knowledge and skills to enhance your company's resilience against cyber threats and attacks. Protect critical assets and ensure the ongoing availability, integrity, and confidentiality of data, whether stored digitally or in the cloud.
Data Confidentiality, Integrity, and Availability: Delve into the core principles of ISO 27001, ensuring that authorized restrictions on access and disclosure are maintained. Safeguard against improper information modification or destruction while ensuring timely and reliable data access.
What You'll Achieve:
By the end of this course, you'll not only master ISO 27001 but also be well-prepared to apply it in practice. You'll become a crucial asset to your organization, capable of securing sensitive information, achieving compliance, and enhancing cybersecurity resilience.
Join us today, and let's embark on this exciting journey to safeguarding information, securing data integrity, and ensuring the continuity of essential information assets. Enroll now and become a master in information security management with ISO 27001.
Who this course is for:
- Information Security Enthusiasts: If you're passionate about information security and eager to deepen your knowledge in ISO 27001, this course is for you. Whether you're just starting out or looking to enhance your expertise, you'll find valuable insights here.
- IT Professionals: IT managers, network administrators, and professionals involved in data security and risk management will benefit from this course. It's an excellent resource for those seeking to align their practices with international standards.
- Business Owners and Managers: For entrepreneurs, small business owners, or managers responsible for information security, this course offers essential guidance on implementing ISO 27001 to safeguard your organization's data and meet legal requirements.
- Compliance and Risk Management Specialists: If you're in a role that requires ensuring regulatory compliance and managing cybersecurity risks, this course will equip you with the tools and knowledge needed to excel in your responsibilities.
- Students and Graduates: Information security is a field with vast career opportunities. Students and recent graduates aspiring to enter this field or enhance their academic knowledge will find this course to be a valuable resource.
- Anyone Interested in Information Security: Whether you're a beginner exploring the world of information security or a professional looking to refresh your skills and knowledge, this course provides comprehensive insights and practical guidance for all curious minds.
User Reviews
Rating
Petar Dimov
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 41
- duration 5:27:53
- Release Date 2023/12/16