The complete iOS Pentesting & Bug Bounty Course
Vaibhav Lakhani
6:50:58
Description
Complete A-Z course on iOS Penetration Testing & iOS Bug Bounty Hunting with practical explanations
What You'll Learn?
- OWASP Mobile Top 10
- Jailbreaking an iOS device
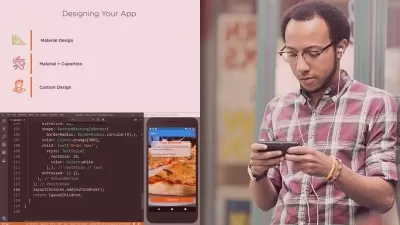
- iOS Basics & how applications work on iOS devices
- iOS Security
- Cybersecurity
- iOS Penetration Testing
Who is this for?
What You Need to Know?
More details
DescriptionWelcome to The complete iOS Pentesting & Bug Bounty Course. This course covers about how security works in iOS devices and how vulnerabilities can be found in iOS applications.
The course starts with the basics of how you can set up your hacking environment and then gradually moves on to how security works in iOS Applications.
The course also shows you the different types of Jailbreak and how you can Jailbreak your iOSÂ Device.
The course also covers OWASPÂ Mobile Top 10 and would cover all the categories of OWASPÂ Mobile Top 10 with practical examples.
The course also includes a detailed overview of iOS Security such as Keychain, Device Management, Data Protection etc.
The major section of iOSÂ Pentesting is the Static and the Dynamic Analysis where most of the vulnerabilities would be covered with practical approaches. These approaches can also be used to find vulnerabilities in bug bounty programs.
At the end of the course, you would be exposed to certain Tips and Tricks that will make your upgrade iOS Pentesting skills. These tips will help you to differentiate yourself from others.
This course also includes the Breakdown of some Hackerone Reports which are found and submitted by other hackers for better understanding.
Who this course is for:
- Beginners who want to learn about iOS Penetration Testing
- Mobile Application Developers
- Security Researchers
- Beginners who want to hunt vulnerabilities & security bugs in iOS Applications
Welcome to The complete iOS Pentesting & Bug Bounty Course. This course covers about how security works in iOS devices and how vulnerabilities can be found in iOS applications.
The course starts with the basics of how you can set up your hacking environment and then gradually moves on to how security works in iOS Applications.
The course also shows you the different types of Jailbreak and how you can Jailbreak your iOSÂ Device.
The course also covers OWASPÂ Mobile Top 10 and would cover all the categories of OWASPÂ Mobile Top 10 with practical examples.
The course also includes a detailed overview of iOS Security such as Keychain, Device Management, Data Protection etc.
The major section of iOSÂ Pentesting is the Static and the Dynamic Analysis where most of the vulnerabilities would be covered with practical approaches. These approaches can also be used to find vulnerabilities in bug bounty programs.
At the end of the course, you would be exposed to certain Tips and Tricks that will make your upgrade iOS Pentesting skills. These tips will help you to differentiate yourself from others.
This course also includes the Breakdown of some Hackerone Reports which are found and submitted by other hackers for better understanding.
Who this course is for:
- Beginners who want to learn about iOS Penetration Testing
- Mobile Application Developers
- Security Researchers
- Beginners who want to hunt vulnerabilities & security bugs in iOS Applications
User Reviews
Rating
Vaibhav Lakhani
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 64
- duration 6:50:58
- Release Date 2023/06/24