The Beginners 2023 Cyber Security Awareness Training Course
Reza Zaheri
3:22:05
Description
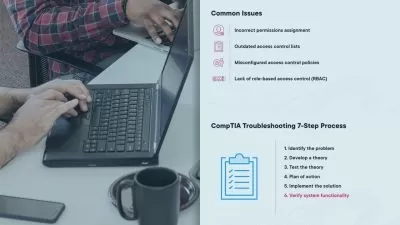
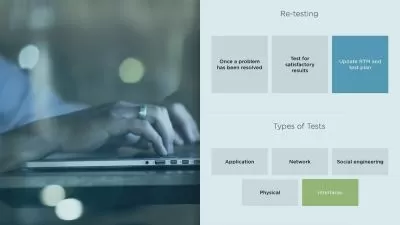
This comprehensive video course has been expertly designed to equip individuals of all levels of IT or cyber security experience with a deep understanding of how to detect and prevent cyber-attacks. You will start with visual examples of targeted phishing emails and learn how to recognize major red flags to detect these emails in the future. You will then gain insights into how businesses and corporations are hacked through malicious macros, BEC fraud scams, ransomware attacks, and other methods. The course will also cover social engineering attacks, using mobile phones to trick individuals into revealing sensitive information. You will become familiar with a range of social engineering attacks that prey on individuals using sneaky methods. In addition to these key areas, you will gain a deeper understanding of security features and differences between iPhones and Androids, including how to avoid downloading malicious apps. The course will also cover general security practices for Mac computers, as well as general tips for protecting yourself when using computers, smartphones, and the Internet. You will then move on to effective solutions for password management, two-factor authentication, and why encryption is essential for privacy and security. By the end of the course, you will be able to recognize and defend against various cyber-attacks, feel confident in securely managing emails, files, mobile phones, computers, and browsing the Internet, and apply best practices for maintaining personal and company security.
More details
User Reviews
Rating
Reza Zaheri
Instructor's Courses
PacktPub
View courses PacktPub- language english
- Training sessions 40
- duration 3:22:05
- Release Date 2024/03/15