Stealthy Domain Enumeration
Naga Sai Nikhil
1:26:13
Description
Learn how to enumerate active directory domain stealthily
What You'll Learn?
- Active Directory Enumeration
- Creating a powershell script loader
- Automating the finding of misconfigurations
- Leveraging .NET for stealthy enumeration
Who is this for?
What You Need to Know?
More details
DescriptionIn this course, you will learn how to enumerate domain information using c# stealthily.
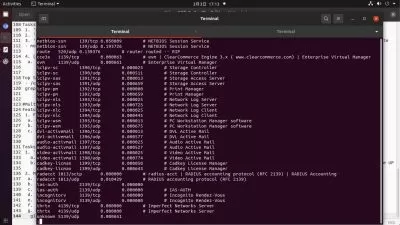
Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks. It is a centralized repository that stores information and settings about a network's resources, such as users, groups, computers, printers, and more. Active Directory provides a single sign-on and centralized authentication and authorization mechanism, making it easier to manage and secure resources within a network.
Enumerating the AD is the most important part in any ad pentesting.
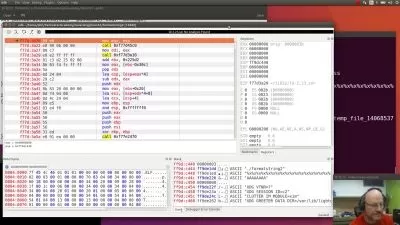
First we kickstart with writing a powershell loader that bypasses amsi, constrained languagemode and can even retrieve the ps scripts from url and execute them.
Then we do enumeration of some juicy domain info using c# like finding kerberoastable accounts, delegated accounts, dcsync accounts and much more.
we also see how to find juicy ACLs to find RBCD capable users etc
Finally we write our own psremoting checking script which checks for local admin access on any of the computers in the specified domain.
there are so many powershell shenanigans like iex execution, obfuscation to bypass defender etc.
but we will focus mainly with c#.
i used ps1loader and these binaries in one of my recent certifications without having to do some modifications to registry etc which course taught.
this course is for pentesters, redteamers and anyone who want to tackle with active directory domain enumeration.
all of the code is given at the end of the course.
Who this course is for:
- Penetration Testers
- Red Teamers
- Blue Teamers
- Administrators
In this course, you will learn how to enumerate domain information using c# stealthily.
Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks. It is a centralized repository that stores information and settings about a network's resources, such as users, groups, computers, printers, and more. Active Directory provides a single sign-on and centralized authentication and authorization mechanism, making it easier to manage and secure resources within a network.
Enumerating the AD is the most important part in any ad pentesting.
First we kickstart with writing a powershell loader that bypasses amsi, constrained languagemode and can even retrieve the ps scripts from url and execute them.
Then we do enumeration of some juicy domain info using c# like finding kerberoastable accounts, delegated accounts, dcsync accounts and much more.
we also see how to find juicy ACLs to find RBCD capable users etc
Finally we write our own psremoting checking script which checks for local admin access on any of the computers in the specified domain.
there are so many powershell shenanigans like iex execution, obfuscation to bypass defender etc.
but we will focus mainly with c#.
i used ps1loader and these binaries in one of my recent certifications without having to do some modifications to registry etc which course taught.
this course is for pentesters, redteamers and anyone who want to tackle with active directory domain enumeration.
all of the code is given at the end of the course.
Who this course is for:
- Penetration Testers
- Red Teamers
- Blue Teamers
- Administrators
User Reviews
Rating
Naga Sai Nikhil
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 8
- duration 1:26:13
- Release Date 2024/03/19