Static Application Security Testing
Jerod Brennen
3:40:42
Description
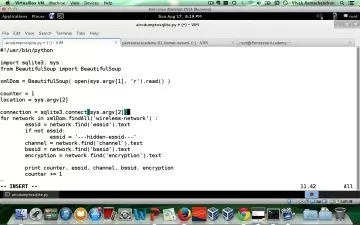
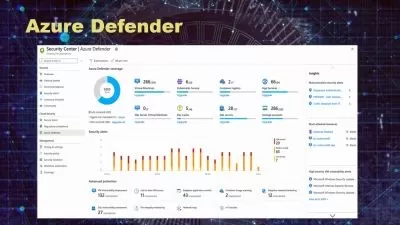
Building security testing into the software development life cycle is the best way to protect your app and your end users. This course identifies tools and techniques that developers can use to minimize the cost and impact of security testing—while maximizing its impact and effectiveness. In this course, instructor Jerod Brennen focuses on offline testing activities: preparing test plans, policies, and other documentation and conducting offline source code reviews. He also explains how to conduct offline testing for the OWASP Top Ten vulnerabilities. Along the way, you can become familiar with best practices around security in the SDLC. The hands-on sections—with demos of popular tools such as Codacy and SonarQube—prepare you to apply the lessons in the real world.
More details
User Reviews
Rating
Jerod Brennen
Instructor's Courses
Linkedin Learning
View courses Linkedin Learning- language english
- Training sessions 40
- duration 3:40:42
- English subtitles has
- Release Date 2023/07/02