Snort Intrusion Detection System: the Essential
Osman BALD
3:21:27
Description
Start managing Snort easily
What You'll Learn?
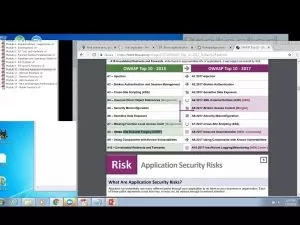
- Snort Components
- Snort Installation and Configuration
- Rule Management
- Configuring Network Interfaces
- Preprocessors and Detection Filters
- Logging and Output Plugins
- Barnyard2 and Database Integration
Who is this for?
What You Need to Know?
More details
Description"Snort Intrusion Detection System: The Essential" is an immersive and comprehensive course designed to empower participants with the knowledge and skills needed to navigate the dynamic landscape of network security. This course is tailored for both beginners seeking a foundational understanding and seasoned professionals looking to enhance their expertise in leveraging Snort, a powerful open-source Intrusion Detection System (IDS).
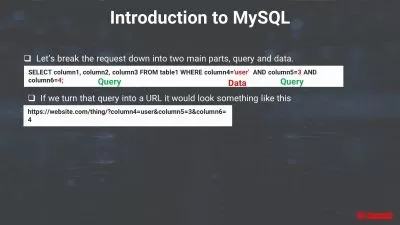
The course begins by providing a solid foundation, guiding participants through the installation and configuration of Snort, ensuring a seamless integration into their network environments. Participants will gain hands-on experience in customizing and writing rules, enabling them to precisely detect and respond to a wide array of security threats. Module 4 delves deep into rule writing and customization, honing participants' abilities to tailor Snort to their organization's specific security requirements.
Moving forward, Module 5 focuses on Snort's operation and management, teaching participants the day-to-day administration tasks, log analysis, and incident response strategies. With an emphasis on practical application, Module 6 explores advanced features of Snort, including dynamic preprocessors, protocol-specific rule options, and anomaly detection mechanisms, ensuring participants are equipped to handle sophisticated cyber threats.
Security best practices take center stage in Module 7, guiding participants in implementing optimal configurations and effective rule management strategies. In Module 8, participants will delve into Snort troubleshooting and debugging, mastering techniques to identify and resolve issues promptly, ensuring the system's reliability and performance.
Module 9 brings the course full circle with case studies and practical applications, immersing participants in real-world scenarios. Through these case studies, participants will synthesize their knowledge, applying it to solve complex problems, and making informed decisions in diverse network security contexts.
Whether you're a security professional, IT administrator, or a network enthusiast, 'Snort Intrusion Detection System: The Essential' equips you with a holistic understanding of Snort, enabling you to fortify your organization's defenses and stay ahead in the ever-evolving landscape of cybersecurity.
Who this course is for:
- Cybersecurity Professionals
- Information Security Analysts
- Network Security Analysts
- SOC Analysts
- Cybersecurity Students
"Snort Intrusion Detection System: The Essential" is an immersive and comprehensive course designed to empower participants with the knowledge and skills needed to navigate the dynamic landscape of network security. This course is tailored for both beginners seeking a foundational understanding and seasoned professionals looking to enhance their expertise in leveraging Snort, a powerful open-source Intrusion Detection System (IDS).
The course begins by providing a solid foundation, guiding participants through the installation and configuration of Snort, ensuring a seamless integration into their network environments. Participants will gain hands-on experience in customizing and writing rules, enabling them to precisely detect and respond to a wide array of security threats. Module 4 delves deep into rule writing and customization, honing participants' abilities to tailor Snort to their organization's specific security requirements.
Moving forward, Module 5 focuses on Snort's operation and management, teaching participants the day-to-day administration tasks, log analysis, and incident response strategies. With an emphasis on practical application, Module 6 explores advanced features of Snort, including dynamic preprocessors, protocol-specific rule options, and anomaly detection mechanisms, ensuring participants are equipped to handle sophisticated cyber threats.
Security best practices take center stage in Module 7, guiding participants in implementing optimal configurations and effective rule management strategies. In Module 8, participants will delve into Snort troubleshooting and debugging, mastering techniques to identify and resolve issues promptly, ensuring the system's reliability and performance.
Module 9 brings the course full circle with case studies and practical applications, immersing participants in real-world scenarios. Through these case studies, participants will synthesize their knowledge, applying it to solve complex problems, and making informed decisions in diverse network security contexts.
Whether you're a security professional, IT administrator, or a network enthusiast, 'Snort Intrusion Detection System: The Essential' equips you with a holistic understanding of Snort, enabling you to fortify your organization's defenses and stay ahead in the ever-evolving landscape of cybersecurity.
Who this course is for:
- Cybersecurity Professionals
- Information Security Analysts
- Network Security Analysts
- SOC Analysts
- Cybersecurity Students
User Reviews
Rating
Osman BALD
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 34
- duration 3:21:27
- Release Date 2024/04/14