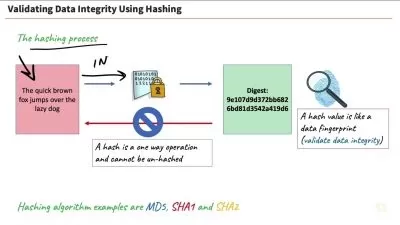
Security Threats, Attacks, and Vulnerabilities Online Training
Keith Barker
6:29:31
Description
This foundational security training prepares security technicians to recognize, compare, and contrast different types of cybersecurity vulnerabilities and threats and indicators associated with network attacks.
Whether you're on your way to earning your CompTIA Security+ certification, working toward a different cybersecurity cert, or just trying to expand your knowledge of digital network security, this training represents a crucial first step in your journey.
More details
You can't keep a computer network or system safe if you don't know what a threat to the system looks like, how different attacks work, or what your network's unique vulnerabilities are. Now you can: learn social engineering techniques, different types of attacks, and network vulnerabilities.
This Security Threats, Attacks and Vulnerabilities training is derived from the first of CompTIA Security+ certification exam's five exam objectives and will prepare you in the broadest way possible.
After finishing the videos in this Security Threats, Attacks, and Vulnerabilities training, you'll know how to recognize, compare, and contrast different types of cybersecurity vulnerabilities and threats and indicators associated with network attacks.
For anyone with security technicians on their team, this CompTIA training can be used to onboard new security technicians, curated into individual or team training plans, or as a CompTIA reference resource.
Security Threats, Attacks, and Vulnerabilities: What You Need to Know
For any security technician looking to improve their proficiency with basic security concepts, this CompTIA course covers topics such as:
- Comparing and contrasting different types of social engineering techniques
- Determining the type of attack, given certain indicators
- Recognizing application attacks like injections, cross-site scripting, and more
- Understanding the range of options network attackers have for infiltration and penetration
Who Should Take Security Threats, Attacks, and Vulnerabilities Training?
This Security Threats, Attacks, and Vulnerabilities training is considered associate-level CompTIA training, which means it was designed for security technicians with 1 to 3 years of experience -- or no experience at all. This security course is valuable for new or aspiring IT professionals, experienced security technicians looking to validate foundational skills, and non-technical professionals.
Basic security concepts user training. Don't make the mistake of assuming this Security Threats, Attacks and Vulnerabilities training is best for IT professionals. Network and system security professionals are constantly immersed in threats and solutions — it's the people who don't normally work with cybersecurity who need to recognize hacking attempts or spot wireless vulnerabilities. That's how an organization and its networks are kept safe.
New or aspiring IT professionals. If you're a brand new security technician, or you're looking for a chance to break into that career field, consider starting your career off on the right foot with this Security Threats, Attacks and Vulnerabilities training. It's a perfect primer for the many different approaches a hostile actor might take to try and break into your networks. Learning this material early will set you up for long-term success in your cybersecurity career.
User Reviews
Rating
Keith Barker
Instructor's CoursesThe best part of being a trainer is making a difference in the life of a student. When a motivated learner and the correct training meet at the right time, the results are amazing.
Keith Barker discovered a love for computers and networking in 1984 and began his IT career in 1985 at Electronic Data Systems (EDS). He has worked with companies including Paramount Pictures, Blue Cross, and several government agencies. Keith loves to teach and spends most of his time creating fun and useful videos for CBT Nuggets.
Certifications: Cisco CCIE (2x), CISSP, Network+, Security+, VMware, Palo Alto, Check Point
Areas of expertise: Networking and Security

CBT Nuggets
View courses CBT Nuggets- language english
- Training sessions 70
- duration 6:29:31
- Release Date 2023/07/17