Security in Spring Boot REST Web Service Applications
Howard Hyde
7:56:58
Description
With Spring Security, authentication, filters, JWT, TLS/HTTPS, Digital Certificates, PKI and Role-based Authorization
What You'll Learn?
- Comprehensive Security for Spring Boot REST web service applications: HTTPS, User management, Authentication, Role-based Authorization
- General principles of cyber security: Threats and defenses, Cryptography (encryption/decryption/hashing; symmetric/asymmetric), TLS, cypher suites
- Implementing user/security and business databases, JSON Web Tokens (JWTs) and SSL/TLS over HTTP (HTTPS) communication with web services
- Spring Security Framework: Architecture, Theory, practical examples: Configuration, filters, authentication and authorization
Who is this for?
What You Need to Know?
More details
DescriptionA complete practical case study and tutorial featuring the Spring Security framework.
Filters and configuration
Authentication
JSON Web Tokens (JWT)
Role-based Authorization
In-depth theory
Also:
General Cybersecurity principles and concepts
Cryptography: Encryption, encoding and hashing
Symmetric and Asymmetric (public/private key) encryption
HTTP over SSL/TLS (HTTPS)
Digital Certificates & Public Key Infrastructure (PKI)
TLSÂ Cipher Suites and handshakes
Case study of a Demo App with 2 Spring Boot REST web services, an Angular/Typescript UI client app and PostGreSQL database(s), which
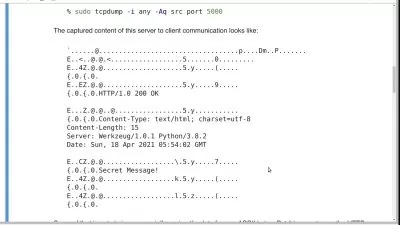
Encrypts all communication between browser and server via HTTP over SSL/TLS (HTTPS)
Establishes trust via signed digital certificates (Public Key Infrastructure -- PKI)
Requires valid credentials to log in.
Custom example user/role/resource/action/authority database.
Limits access to resources in web service and client app according to roles / authorities of user account; detailed development of Authorization
Employs JSON Web Tokens (JWTs) as its authorization mechanism.
NOT WebMvc: Does NOT track sessions or JSESSONID cookies; does not output HMTL, login forms etc. (not JSP or Thymeleaf)
Rather, REpresentational State Transfer (REST): Exchanges JSON data payloads with clients
Assumes clients take care of all UI elements, HTML code, css, Javascript etc.
Course Structure
Part 0: Is this Course Right for Me?
Part 1: General Cyber Security Principles
Part 2: Introducing the Demo App and its Components
Part 3: Application Security elements BEFORE adding the Spring Security Framework
Part 4: The Spring Security Framework in our Demo App
Part 5: A Deeper Dive into Spring Security Architecture and Theory
Who this course is for:
- Web service developers/software engineers, architects, cyber security professionals
A complete practical case study and tutorial featuring the Spring Security framework.
Filters and configuration
Authentication
JSON Web Tokens (JWT)
Role-based Authorization
In-depth theory
Also:
General Cybersecurity principles and concepts
Cryptography: Encryption, encoding and hashing
Symmetric and Asymmetric (public/private key) encryption
HTTP over SSL/TLS (HTTPS)
Digital Certificates & Public Key Infrastructure (PKI)
TLSÂ Cipher Suites and handshakes
Case study of a Demo App with 2 Spring Boot REST web services, an Angular/Typescript UI client app and PostGreSQL database(s), which
Encrypts all communication between browser and server via HTTP over SSL/TLS (HTTPS)
Establishes trust via signed digital certificates (Public Key Infrastructure -- PKI)
Requires valid credentials to log in.
Custom example user/role/resource/action/authority database.
Limits access to resources in web service and client app according to roles / authorities of user account; detailed development of Authorization
Employs JSON Web Tokens (JWTs) as its authorization mechanism.
NOT WebMvc: Does NOT track sessions or JSESSONID cookies; does not output HMTL, login forms etc. (not JSP or Thymeleaf)
Rather, REpresentational State Transfer (REST): Exchanges JSON data payloads with clients
Assumes clients take care of all UI elements, HTML code, css, Javascript etc.
Course Structure
Part 0: Is this Course Right for Me?
Part 1: General Cyber Security Principles
Part 2: Introducing the Demo App and its Components
Part 3: Application Security elements BEFORE adding the Spring Security Framework
Part 4: The Spring Security Framework in our Demo App
Part 5: A Deeper Dive into Spring Security Architecture and Theory
Who this course is for:
- Web service developers/software engineers, architects, cyber security professionals
User Reviews
Rating
Howard Hyde
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 63
- duration 7:56:58
- Release Date 2024/10/05