Security Event Triage: Analyzing Live System Process and Files
Cristian Pascariu
1:34:13
Description
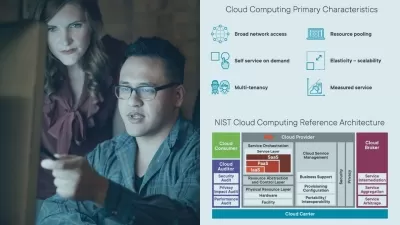
Traditional forensic analysis on endpoints is outpaced by modern attack techniques. This course will teach you how to efficiently identify and investigate malicious activity by performing live system analysis on processes and files.
What You'll Learn?
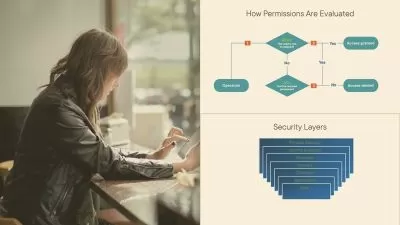
Covert attack techniques coupled with the use of legitimate processes and utilities require more advanced detection and analysis techniques. In this course, Security Event Triage: Analyzing Live System Process and Files, you’ll learn how to leverage endpoint detection tools and techniques to detect attacks that bypass traditional signature and rule-based capabilities. First, you’ll explore how malware establishes persistence on disk or via the registry. Next, you’ll discover how to detect malware that injects itself into legitimate processes. Finally, you’ll learn how to correlate running processes with network connections to identify malicious processes but also C2 communication channels. When you’re finished with this course, you’ll have the skills and knowledge of live system analysis needed for Continuous monitoring and detection.
More details
User Reviews
Rating
Cristian Pascariu
Instructor's Courses
Pluralsight
View courses Pluralsight- language english
- Training sessions 32
- duration 1:34:13
- level advanced
- English subtitles has
- Release Date 2023/02/28