Securing Data with Asymmetric Cryptography
Edward Curren
1:40:01
Description
Asymmetric cryptography is used in everything ranging from SSL and TLS certificates to credit card chips to digital document signatures. Security is more critical than ever and is one of the most important skills to have in the industry today.
What You'll Learn?
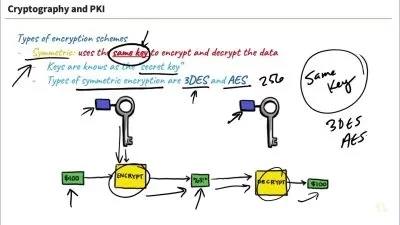
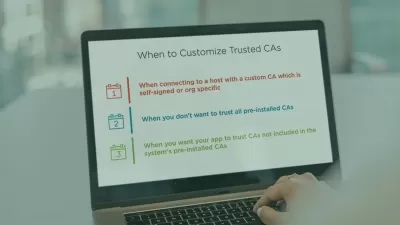
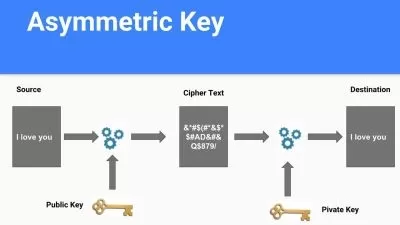
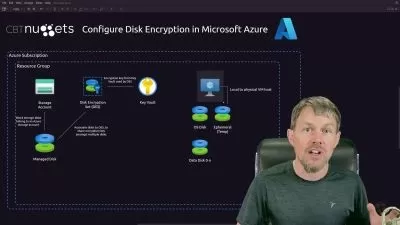
Data and communication security are critical issues across all industries. In this course, Securing Data with Asymmetric Cryptography, you will learn foundational knowledge of public private key pair cryptography and gain the ability to practically employ it in your projects. First, you will learn what key pairs are, how to generate them and how to store them. Next, you will discover X.509 certificates in detail. Finally, you will explore how to implement a fully functional PKI including a certificate authority. When you’re finished with this course, you will have the skills and knowledge of asymmetric cryptography needed to employ security in your projects.
More details
User Reviews
Rating
Edward Curren
Instructor's Courses
Pluralsight
View courses Pluralsight- language english
- Training sessions 46
- duration 1:40:01
- level preliminary
- Release Date 2023/12/08