Secure your IT Systems & Network: For Sys Admins + Engineers
Emilio Aguero
6:16:33
Description
Learn all about Cybersecurity...and how to improve security across your systems and network
What You'll Learn?
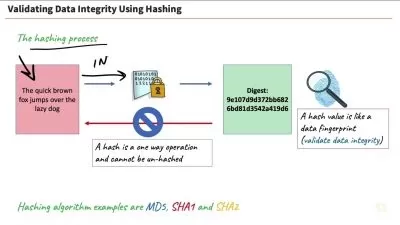
- All about Cybersecurity - Common terminologies, concepts, and the threat landscape
- Identity and Access Management
- How to secure your company's servers and network, including firewalls, IDS, and VPNs
- Operating system security and best practices for hardening
- How to identify vulnerabilities, vulnerability scanning, patch management
- Mobile device security
- Learn about the importance of Backups
Who is this for?
What You Need to Know?
More details
DescriptionAs technology continues to advance, so do the cyber threats that target our systems and networks. System administrators play a critical role in securing their organizations' digital assets, and it's essential for them to have a solid understanding of cybersecurity principles and best practices.
This course is designed specifically for system administrators who want to enhance their cybersecurity knowledge and skills. In this course, you will learn the essential principles and techniques to secure your organization's systems and networks against cyber threats.
We will cover a broad range of topics, including network security, operating system security, authentication and access control, vulnerability management, incident response, encryption and cryptography, web application security, mobile device security, and compliance and regulations. You will learn about the latest threats and attacks, including how to detect, prevent, and respond to them effectively.
What we'll cover:
Introduction to Cybersecurity: You will learn the basics of cybersecurity, including common terminology, concepts, and the threat landscape.
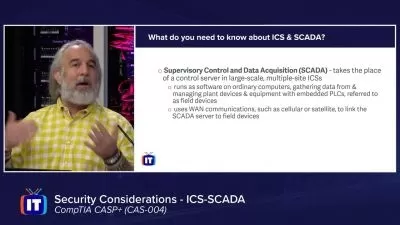
Network Security: You will learn how to secure your organization's network, including firewalls, intrusion detection and prevention systems, and virtual private networks (VPNs).
Operating System Security: You will learn how to secure operating systems, including Windows and Linux, and best practices for hardening them against cyber threats.
Authentication and Access Control: You will learn about the importance of strong authentication and access control, including password policies, multi-factor authentication, and role-based access control.
Vulnerability Management: You will learn how to identify and remediate vulnerabilities in your systems, including vulnerability scanning, patch management, and vulnerability assessment.
Incident Response: You will learn about incident response, including how to detect, respond to, and recover from cybersecurity incidents.
Best practices around backups and data recovery: How to structure and setup a robust backup system with cybersecurity in mind.
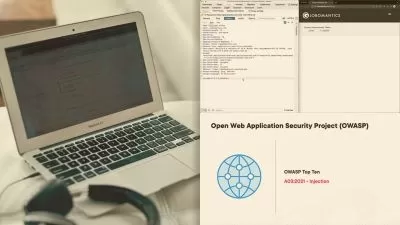
Web Application Security: You will learn how to secure web applications, including common vulnerabilities and best practices.
Mobile Device Security: You will learn about mobile device security, including how to secure mobile applications and mobile device management.
and much more...
By the end of this course, you will have a solid understanding of cybersecurity essentials and be able to apply them to secure your organization's systems and networks. You will also be well-prepared to pursue further training in the cybersecurity field.
Who this course is for:
- System Administrators and Engineers
- Network Engineers
- Helpdesk and Support Analysts
- IT Management
- Cybersecurity Administrators
As technology continues to advance, so do the cyber threats that target our systems and networks. System administrators play a critical role in securing their organizations' digital assets, and it's essential for them to have a solid understanding of cybersecurity principles and best practices.
This course is designed specifically for system administrators who want to enhance their cybersecurity knowledge and skills. In this course, you will learn the essential principles and techniques to secure your organization's systems and networks against cyber threats.
We will cover a broad range of topics, including network security, operating system security, authentication and access control, vulnerability management, incident response, encryption and cryptography, web application security, mobile device security, and compliance and regulations. You will learn about the latest threats and attacks, including how to detect, prevent, and respond to them effectively.
What we'll cover:
Introduction to Cybersecurity: You will learn the basics of cybersecurity, including common terminology, concepts, and the threat landscape.
Network Security: You will learn how to secure your organization's network, including firewalls, intrusion detection and prevention systems, and virtual private networks (VPNs).
Operating System Security: You will learn how to secure operating systems, including Windows and Linux, and best practices for hardening them against cyber threats.
Authentication and Access Control: You will learn about the importance of strong authentication and access control, including password policies, multi-factor authentication, and role-based access control.
Vulnerability Management: You will learn how to identify and remediate vulnerabilities in your systems, including vulnerability scanning, patch management, and vulnerability assessment.
Incident Response: You will learn about incident response, including how to detect, respond to, and recover from cybersecurity incidents.
Best practices around backups and data recovery: How to structure and setup a robust backup system with cybersecurity in mind.
Web Application Security: You will learn how to secure web applications, including common vulnerabilities and best practices.
Mobile Device Security: You will learn about mobile device security, including how to secure mobile applications and mobile device management.
and much more...
By the end of this course, you will have a solid understanding of cybersecurity essentials and be able to apply them to secure your organization's systems and networks. You will also be well-prepared to pursue further training in the cybersecurity field.
Who this course is for:
- System Administrators and Engineers
- Network Engineers
- Helpdesk and Support Analysts
- IT Management
- Cybersecurity Administrators
User Reviews
Rating
Emilio Aguero
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 46
- duration 6:16:33
- Release Date 2023/09/12