Secure Computer User
Yash Pandit
4:51:41
Description
DON’T GET HOOKED — THINK BEFORE YOU CLICK!
What You'll Learn?
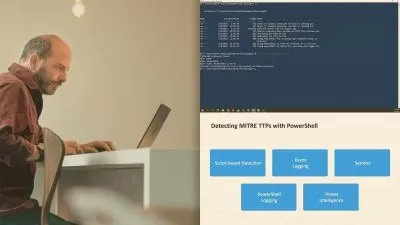
- INTRODUCTION TO DATA SECURITY
- SECURING OPERATING SYSTEMS
- MALWARE AND ANTIVIRUS
- INTERNET SECURITY
- SECURITY ON SOCIAL NETWORKING SITES
- SECURING EMAIL COMMUNICATIONS
- SECURING MOBILE DEVICES
- SECURING THE CLOUD
- SECURING NETWORK CONNECTIONS
- DATA BACKUP AND DISASTER RECOVERY
- SECURING IOT DEVICES AND GAMING CONSOLES
- SECURE REMOTE WORK
Who is this for?
What You Need to Know?
More details
DescriptionThe CSCU program is designed to educate students on the safe operation of computers, devices, and networks by focusing on the more practical aspects of networking and security, allowing them to expand their skills. Students will develop a fundamental understanding of computer, device, and network security issues, including identity theft, credit card fraud, online banking phishing scams, malware, loss of sensitive information, and social engineering. This certification is an excellent complement to educational offerings for knowledge workers and end-users interested in becoming secure power users.
DON’T GET HOOKED — THINK BEFORE YOU CLICK!
Course Description: The threat of cybercrime to both individuals and businesses is rising fast. Defensive Secure User is a global awareness certification program curated to create, enhance and sustain awareness about the rising threats in the information or cyber world. The purpose of this certification is to orient the learner to the correct use of the cyber world, explains data security and associated threats, and suggests relevant solutions to combat the same.
Advantage of course: The program helps learners acquire a fundamental understanding of various computer and network security threats such as malware, virus and backdoors, identity theft, phishing scams, hacking attacks, credit card fraud, and social engineering, and protect their information assets in the constantly changing security landscape.
Who can enroll: This course can be taken by anyone who wants to learn effective usage of Operating System Security. Also this course will be helpful for those who are looking for the career of Combination IT Field or Cyber Security.
Prerequisites: There are no pre-requisites for this course however familiarity to IT world is beneficial.
Course Content:
MODULE 1: INTRODUCTION TO DATA SECURITY
MODULE 2: SECURING OPERATING SYSTEMS
MODULE 3: MALWARE AND ANTIVIRUS
MODULE 4: INTERNET SECURITY
MODULE 5: SECURITY ON SOCIAL NETWORKING SITES
MODULE 6: SECURING EMAIL COMMUNICATIONS
MODULE 7: SECURING MOBILE DEVICES
MODULE 8: SECURING THE CLOUD
MODULE 9: SECURING NETWORK CONNECTIONS
MODULE 10: DATA BACKUP AND DISASTER RECOVERY
MODULE 11: SECURING IOT DEVICES AND GAMING CONSOLES
MODULE 12: SECURE REMOTE WORK
Who this course is for:
- C|SCU goes well beyond traditional security awareness courses providing the training to become an individual power user. Securing your own computer, mobile device, gaming system, home network, Smart Home devices is critical to avoiding low level scams and attacks that many consumers fall victim to every day. This program was designed for any individual who uses computers and/or devices with internet services, including the web, social media, email, messaging apps, etc. that is interested in securing their devices and communication channels.
The CSCU program is designed to educate students on the safe operation of computers, devices, and networks by focusing on the more practical aspects of networking and security, allowing them to expand their skills. Students will develop a fundamental understanding of computer, device, and network security issues, including identity theft, credit card fraud, online banking phishing scams, malware, loss of sensitive information, and social engineering. This certification is an excellent complement to educational offerings for knowledge workers and end-users interested in becoming secure power users.
DON’T GET HOOKED — THINK BEFORE YOU CLICK!
Course Description: The threat of cybercrime to both individuals and businesses is rising fast. Defensive Secure User is a global awareness certification program curated to create, enhance and sustain awareness about the rising threats in the information or cyber world. The purpose of this certification is to orient the learner to the correct use of the cyber world, explains data security and associated threats, and suggests relevant solutions to combat the same.
Advantage of course: The program helps learners acquire a fundamental understanding of various computer and network security threats such as malware, virus and backdoors, identity theft, phishing scams, hacking attacks, credit card fraud, and social engineering, and protect their information assets in the constantly changing security landscape.
Who can enroll: This course can be taken by anyone who wants to learn effective usage of Operating System Security. Also this course will be helpful for those who are looking for the career of Combination IT Field or Cyber Security.
Prerequisites: There are no pre-requisites for this course however familiarity to IT world is beneficial.
Course Content:
MODULE 1: INTRODUCTION TO DATA SECURITY
MODULE 2: SECURING OPERATING SYSTEMS
MODULE 3: MALWARE AND ANTIVIRUS
MODULE 4: INTERNET SECURITY
MODULE 5: SECURITY ON SOCIAL NETWORKING SITES
MODULE 6: SECURING EMAIL COMMUNICATIONS
MODULE 7: SECURING MOBILE DEVICES
MODULE 8: SECURING THE CLOUD
MODULE 9: SECURING NETWORK CONNECTIONS
MODULE 10: DATA BACKUP AND DISASTER RECOVERY
MODULE 11: SECURING IOT DEVICES AND GAMING CONSOLES
MODULE 12: SECURE REMOTE WORK
Who this course is for:
- C|SCU goes well beyond traditional security awareness courses providing the training to become an individual power user. Securing your own computer, mobile device, gaming system, home network, Smart Home devices is critical to avoiding low level scams and attacks that many consumers fall victim to every day. This program was designed for any individual who uses computers and/or devices with internet services, including the web, social media, email, messaging apps, etc. that is interested in securing their devices and communication channels.
User Reviews
Rating
Yash Pandit
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 16
- duration 4:51:41
- Release Date 2023/11/22