Scenario Based Docker Security
Chris Behrens
5:14:24
Description
This is your second step in the path to learning all about securing containers.
What You'll Learn?
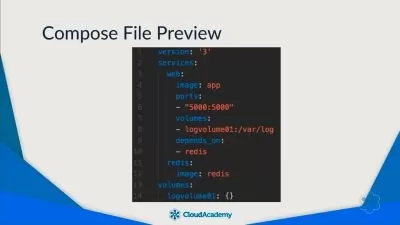
Welcome to this Scenario Based Docker Security course. This is the second course of a four-course learning path related to securing containers. The lessons that are presented here focus on the security aspect of Docker through which you will learn how to perform various configurations and navigate through different situations within the context of security. Having a proper configuration without security loopholes and having your software sources, such as container images, as secure as possible is very important. In the first part of this course, we will begin with a guide on how to install and configure Docker properly. We will talk about resource restrictions where you will learn about Linux cgroups and how they can be used to pose limits on different aspects of your system, as well as learn how to monitor resources and process usage. After that, we will move on to Seccomp - Secure Computing Mode and learn how to configure seccomp profiles. Seccomp is a security tool mechanism that Docker can use to achieve additional security. Securing software sources is extremely important, which is why we will go over the whole process of creating a repository, creating an image, pushing it to the repository, pulling it, doing some changes, pushing it back and so forth, while keeping in mind how to achieve optimal security. This is why we will talk about topics such as creating SSL certificates so that the traffic between us and the software source is encrypted. This will be achieved using Certbot and Let’s Encrypt. We will talk about the security advantages of private repositories and custom images. You will learn how to create custom images from scratch, specifically two images, where one will be a web server image and the other a MySql Database image. After that, we will take a closer look at Docker Bench. It is a security tool that is also used for optimization. When it runs, it performs a series of scans that give you suggestions on what should or shouldn't be fixed. When all of this is done, the last part of this course is dedicated to deploying and securing an application's backend. These videos can be viewed as a sort of mini-project and review of what has been learned so far. We will be configuring a Docker container to run an Apache web server as an application backend. We will configure a Docker container for which we need to create a custom image to run a Python application (more specifically a Flask application). This application will have an active API that is fully functional and it will achieve a connection to a database for which we will also need to construct a container. So, we will have two Docker containers communicating with each other. We will also set up an Apache web server that will be a gateway to the outer world, so to speak. It will be used as a reverse proxy to allow connections from the outer world to reach our containers. Certbot will be utilized for creating an SSL certificate for our domain.
More details
User Reviews
Rating
Chris Behrens
Instructor's Courses
Acloud Guru
View courses Acloud Guru- language english
- Training sessions 33
- duration 5:14:24
- Release Date 2024/04/26