Scaling Your Cybersecurity and Privacy Program
Nishant Bhajaria
1:23:12
Description
As cybersecurity becomes a key part of a company’s risk/trust strategy, it can become difficult to adapt and scale such a program. In this course, Nishant Bhajaria helps companies design an automation-powered and data-driven cybersecurity program.
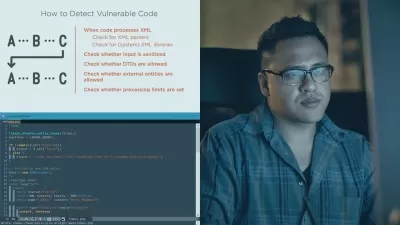
Join Nishant as he shows you how to: categorize cybersecurity into four key dimensions; identify, protect, detect, and recover when it comes to security risk; identify strengths and gaps for various cybersecurity initiatives; build a cybersecurity capability maturity model for your business; categorize your company’s capabilities along the spectrum of basic, advanced and leading; and more. If you’re trying to figure out where and how to invest your cybersecurity resources, this course can help you build better security capabilities and measure their effectiveness for audits and assessments—thereby building trust with customers while also improving your compliance posture.
More details
User Reviews
Rating
Nishant Bhajaria
Instructor's Courses
Linkedin Learning
View courses Linkedin Learning- language english
- Training sessions 25
- duration 1:23:12
- Release Date 2022/12/11