SC-200: Microsoft Security Operations Analyst
Anand Rao Nednur
12:43:04
Description
Become a Microsoft SOC engineer Today!! Learn through lab excercises and practical demonstrations
What You'll Learn?
- Define the capabilities of Microsoft Defender for Endpoint.
- Understand how to hunt threats within your network.
- Explain how Microsoft Defender for Endpoint can remediate risks in your environment.
- Create a Microsoft Defender for Endpoint environment
- Onboard devices to be monitored by Microsoft Defender for Endpoint
- Configure Microsoft Defender for Endpoint environment settings
- Investigate incidents in Microsoft Defender for Endpoint
- Investigate alerts in Microsoft Defender for Endpoint
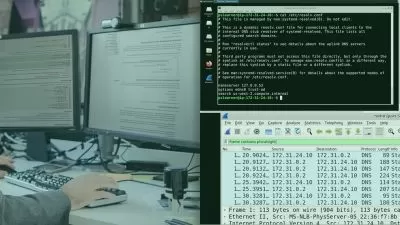
- Perform advanced hunting in Microsoft Defender for Endpoint
- Configure alert settings in Microsoft Defender for Endpoint
- Construct KQL statements
- Manage indicators in Microsoft Defender for Endpoint
- Describe Threat and Vulnerability Management in Microsoft Defender for Endpoint
- Identify vulnerabilities on your devices with Microsoft Defender for Endpoint
- Track emerging threats in Microsoft Defender for Endpoint
Who is this for?
More details
Description
There is no short cut to learning Azure security. This course teaches you how to learn it the right way with tons of labs excercises and the right volume of labs .
The Microsoft Security Operations Analyst works with organizational stakeholders to secure the organization's information technology systems. Their mission is to reduce corporate risk by quickly resolving active attacks in the environment, advising on threat protection practices, and reporting policy violations to the proper stakeholders.
Threat management, monitoring, and response using a variety of security technologies across their environment are among their responsibilities. Using Microsoft Azure Sentinel, Azure Defender, Microsoft 365 Defender, and third-party security tools, the position primarily investigates, responds to, and hunts for threats. The security operations analyst is a key stakeholder in the configuration and implementation of these technologies since they consume the operational output of these solutions.
The following topics needs to be completed in order to achieve SC - 200 Certification.
Module 1 Mitigate threats using Microsoft 365 Defender
Module 2 Mitigate threats using Microsoft Defender for Endpoint
Module 3 Mitigate threats using Azure Defender
Module 4 Create queries for Azure Sentinel using Kusto Query Language
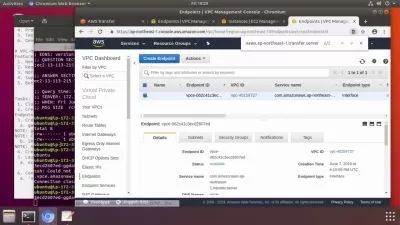
Module 5 Microsoft Sentinel Environment - Configuration
Module 6 Microsoft Sentinel Environment - Connecting Logs
Module 7 Microsoft Sentinel Environment - Incidents,Threat Response , UEBA and Monitoring
Module 8 Module 8 Perform Threat Hunting with Microsoft Sentinel
You will learn to Implement the Microsoft Defender for Endpoint platform to detect, investigate, and respond to advanced threats.
This learning path aligns with exam SC-200: Microsoft Security Operations Analyst Exam.
Reviews from Participants -
In the beginning I was a little intimidated by the immensity of Microsoft security environment, but getting along with the course it all clicked in my head. The concepts are presented at a very good pace and I like that the information is on point. Segmenting the videos in small chunks is also beneficial for time management. I really appreciate and recommend this course! - Adrian Carbune
Great course. I learned a lot about Defender and Sentinel. I especially liked the module on KQL. IMO, it's the best tutorial on Kusto that I've found on the web. If Anand were to create a course that went in-depth on KQL I would certainly purchase it.
-Bill Jones
Anand has structured the course well, so that anyone, irrespective of their experience in Security, would be able to follow with ease. The course aligns very well with the Certification track. I strongly recommend this course to anyone who is interested in understanding Security.
-Moses M
am truley satisfied with this course. Anand nails the security features of M 365 defender suite. The graphics , narration and worlkflows are commendable. Just labs, labs and labs . Its all about getting straight to the point. Great Job!!!
-Gaurav
Great course, congratulations to teacher! Help me a lot to gain very knowledge about Defender and Sentinel. I appreciate it!!!
-Alexandre Gammaro
It was one of the The best course .Your are an amazing Instructor.
-Navid
This course is Awsome! One of the best I've ever made over here in Udemy platform.
-Mauricio Kobayashi
Who this course is for:
- Participants aspiring for SC 200 Certification
- Everyone who aspires to work in the modern age SOC environment
- Anyone wants to learn the M365 defender Suite of services
There is no short cut to learning Azure security. This course teaches you how to learn it the right way with tons of labs excercises and the right volume of labs .
The Microsoft Security Operations Analyst works with organizational stakeholders to secure the organization's information technology systems. Their mission is to reduce corporate risk by quickly resolving active attacks in the environment, advising on threat protection practices, and reporting policy violations to the proper stakeholders.
Threat management, monitoring, and response using a variety of security technologies across their environment are among their responsibilities. Using Microsoft Azure Sentinel, Azure Defender, Microsoft 365 Defender, and third-party security tools, the position primarily investigates, responds to, and hunts for threats. The security operations analyst is a key stakeholder in the configuration and implementation of these technologies since they consume the operational output of these solutions.
The following topics needs to be completed in order to achieve SC - 200 Certification.
Module 1 Mitigate threats using Microsoft 365 Defender
Module 2 Mitigate threats using Microsoft Defender for Endpoint
Module 3 Mitigate threats using Azure Defender
Module 4 Create queries for Azure Sentinel using Kusto Query Language
Module 5 Microsoft Sentinel Environment - Configuration
Module 6 Microsoft Sentinel Environment - Connecting Logs
Module 7 Microsoft Sentinel Environment - Incidents,Threat Response , UEBA and Monitoring
Module 8 Module 8 Perform Threat Hunting with Microsoft Sentinel
You will learn to Implement the Microsoft Defender for Endpoint platform to detect, investigate, and respond to advanced threats.
This learning path aligns with exam SC-200: Microsoft Security Operations Analyst Exam.
Reviews from Participants -
In the beginning I was a little intimidated by the immensity of Microsoft security environment, but getting along with the course it all clicked in my head. The concepts are presented at a very good pace and I like that the information is on point. Segmenting the videos in small chunks is also beneficial for time management. I really appreciate and recommend this course! - Adrian Carbune
Great course. I learned a lot about Defender and Sentinel. I especially liked the module on KQL. IMO, it's the best tutorial on Kusto that I've found on the web. If Anand were to create a course that went in-depth on KQL I would certainly purchase it.
-Bill Jones
Anand has structured the course well, so that anyone, irrespective of their experience in Security, would be able to follow with ease. The course aligns very well with the Certification track. I strongly recommend this course to anyone who is interested in understanding Security.
-Moses M
am truley satisfied with this course. Anand nails the security features of M 365 defender suite. The graphics , narration and worlkflows are commendable. Just labs, labs and labs . Its all about getting straight to the point. Great Job!!!
-Gaurav
Great course, congratulations to teacher! Help me a lot to gain very knowledge about Defender and Sentinel. I appreciate it!!!
-Alexandre Gammaro
It was one of the The best course .Your are an amazing Instructor.
-Navid
This course is Awsome! One of the best I've ever made over here in Udemy platform.
-Mauricio Kobayashi
Who this course is for:
- Participants aspiring for SC 200 Certification
- Everyone who aspires to work in the modern age SOC environment
- Anyone wants to learn the M365 defender Suite of services
User Reviews
Rating
Anand Rao Nednur
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 202
- duration 12:43:04
- English subtitles has
- Release Date 2023/04/19