Reverse Engineering Win32 Applications
Focused View
18:37:29
132 View
1. Reverse Engineering Win32 Applications - Course Introduction[HD,1280x720, Mp4].mp4
09:30
2. Getting Started Reverse Engineering Win32 Applications.mp4
34:12
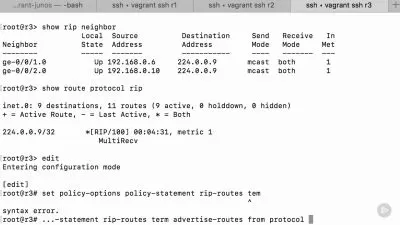
3. Olly Debugger Reverse Engineering Win32 Applications.mp4
13:32
4. Immunity Debugger Reverse Engineering Win32 Applications.mp4
10:39
5. IDA Pro Reverse Engineering Win32 Applications.mp4
22:58
6. A Little Bit of Assembly Part 1 Reverse Engineering Win32.mp4
09:28
7. A Little Bit of Assembly Part 2 Reverse Engineering Win32.mp4
07:15
8. A Little Bit of Assembly Part 3 Reverse Engineering Win32.mp4
07:20
9. A Little Bit of Assembly Part 4 Reverse Engineering Win32.mp4
12:05
10. Stack Buffer Overflows Part 1 The Basics Reverse Engineering.mp4
11:10
11. Stack Buffer Overflows Part 2 Overwriting Return Addresses Reverse.mp4
18:17
12. Stack Buffer Overflows Part 3 Calculating Offsets Reverse Engineering.mp4
16:48
13. Stack Buffer Overflows Part 4 Injecting Code on the Stack Reverse.mp4
10:47
14. Stack Buffer Overflows Part 5 JMP ESP Reverse Engineering Win32.mp4
14:18
15. Stack Buffer Overflows Part 6 Stack Protection Reverse Engineering Win32 Applications.mp4
13:02
16. Stack Buffer Overflows Part 7 Return to Libc Reverse Engineering Win32 Applications.mp4
39:20
17. Stack Buffer Overflows Part 8 Return to Libc Chaining Reverse Engineering Win32 Applications.mp4
54:56
18. Stack Buffer Overflows Part 9 ASLR Mitigation Reverse Engineering Win32 Applications.mp4
24:40
19. Stack Buffer Overflows Part 10 Return Oriented Programming Reverse Engineering Win32 Applications.mp4
41:45
20. Stack Buffer Overflows Part 11 Stack Canaries and Summary Reverse Engineering Win32 Applications.mp4
21:34
21. Heap Overflows Part 1 Heap Basics Reverse Engineering Win32 Applications.mp4
15:31
22. Heap Overflows Part 2 Simple Examples Reverse Engineering Win32 Applications.mp4
18:18
23. Heap Overflows Part 3 Simple Examples Continued Reverse Engineering Win32 Applications.mp4
36:00
24. Heap Overflows Part 4 More Examples Reverse Engineering Win32 Applications.mp4
34:14
25. Heap Overflows Part 5 Still More Examples Reverse Engineering Win32 Applications.mp4
29:18
26. win32-rev026-formatStringsP1.mp4
21:06
27. win32-rev027-formatStringsP2.mp4
20:47
28. win32-rev028-formatStringsP3.mp4
40:29
29. win32-rev029-formatStringsP4A.mp4
33:15
30. win32-rev030-formatStringsP4B.mp4
28:32
31. win32-rev031-formatStringsP5.mp4
34:04
32. win32-rev032-sectionOverflows.mp4
29:41
33. win32-rev033-kernelFlaws.mp4
12:12
34. win32-rev034-toolsP1.mp4
41:13
35. win32-rev035-toolsP2.mp4
10:45
36. win32-rev036-toolsP3.mp4
16:55
win32-rev037-toolsP4.mp4
32:49
win32-rev038-toolsP5.mp4
24:08
win32-rev039-vulnserverP1.mp4
14:15
win32-rev040-vulnserverP2.mp4
12:42
win32-rev041-vulnserverP3.mp4
13:13
win32-rev042-vulnserverP4.mp4
20:05
win32-rev043-vulnserverP5.mp4
22:28
win32-rev044-vulnserverP6.mp4
22:15
win32-rev045-vulnserverP7.mp4
44:53
win32-rev046-malwareP1.mp4
07:12
win32-rev047-malwareP2.mp4
12:37
win32-rev048-malwareP3.mp4
14:38
win32-rev049-malwareP4.mp4
18:31
win32-rev050-malwareP5.mp4
11:35
win32-rev051-malwareP6.mp4
06:48
win32-rev052-malwareP7.mp4
16:32
win32-rev053-wrapup.mp4
06:52
More details
User Reviews
Rating
average 0
Focused display

Pentester Academy
View courses Pentester AcademyFounded in 2011 by world-renowned security researcher and trainer, Vivek Ramachandran, Pentester Academy is the world's leading cybersecurity skills ...
- language english
- Training sessions 53
- duration 18:37:29
- Release Date 2023/06/15