Red and Blue Team Foundations Course - VAPT & Infosec Basics
GRC Gate Training
6:59:46
Description
VAPT & Information Security for Absolute Beginners, Build the basics of Ethical Hacking
What You'll Learn?
- Fundamentals of Information Security
- Cybersecurity Concepts
- Malware and Defense
- Network Security
- Web Application Security
- Social Engineering and Human Behavior
- Legal, Regulatory, and Security Standards
- Full-Scale Attack Simulation
Who is this for?
What You Need to Know?
More details
DescriptionWelcome to the Comprehensive Cybersecurity and Information Security Course!
Information Security and Cybersecurity Complete Prep course training will help you prep. for GIAC GSEC, Security+, Cysa+Â , and more!!
This beginner-friendly course is your gateway to the exciting world of information security.
Are you an absolute beginner looking to enter the exciting world of information security? Or do you already have a basic understanding of cybersecurity and want to enhance your skills and knowledge? Look no further! This comprehensive program empowers you to master the fundamentals and build a strong foundation in protecting digital assets.
Throughout the course, we will guide you step-by-step through the essential concepts, tools, and practices that form the backbone of information security. You will gain a solid grasp of the core principles that underpin effective cybersecurity strategies, including the CIA (Confidentiality, Integrity, Availability) triad and the differentiation between threats, vulnerabilities, and risks.
But we won't stop there. This program goes beyond basic information security and delves into the captivating world of cybersecurity. Our CyberShield module is designed to equip you with the skills and knowledge to become a formidable defender against the ever-evolving threats in our digital landscape.
You'll uncover the secrets behind encryption and its practical benefits, gaining insights into the intricate workings of the cyber kill chain. Dive deep into the OSI model to understand the fundamental layers of secure networks and gain hands-on experience with industry-standard tools like Wireshark, allowing you to examine network traffic and detect potential security breaches.
Our comprehensive approach includes exploring web application penetration testing, where you'll learn how to identify and exploit vulnerabilities such as XSS (Cross-Site Scripting) and SQLi (SQL Injection). You'll also uncover the dark arts of Google Hacking, enabling you to uncover hidden vulnerabilities lurking in plain sight.
students will learn a wide range of essential information security and cybersecurity topics. Here is an overview of what they can expect to learn:
Fundamentals of Information Security:
Understanding the CIA (Confidentiality, Integrity, Availability) triad.
Differentiating between threats, vulnerabilities, and risks.
Exploring security and privacy interplay.
Cybersecurity Concepts:
Exploring the cyber kill chain and understanding the lifecycle of an attack.
Identifying and responding to potential threats proactively.
Understanding different types of threat actors and their motivations.
Malware and Defense:
Investigating the world of malware and its impact.
Implementing strategies to defend against malicious programs.
Network Security:
Understanding the OSI model and its significance in secure network communication.
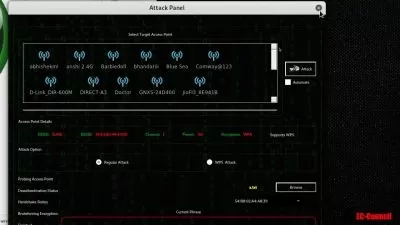
Protecting against common network attacks like IP spoofing and man-in-the-middle (MiTM) attacks.
Utilizing tools like Wireshark to examine network traffic and detect security breaches.
Web Application Security:
Conducting web application penetration testing.
Identifying and exploiting vulnerabilities like XSS (Cross-Site Scripting) and SQLi (SQL Injection).
Discovering hidden vulnerabilities through Google Hacking.
Social Engineering and Human Behavior:
Recognizing common manipulation tactics used by attackers.
Understanding the art of social engineering and its impact on security.
Developing strategies to defend against social engineering attacks.
Legal, Regulatory, and Security Standards:
Navigating the complex landscape of legal and regulatory requirements.
Understanding the importance of compliance and best practices.
Fortifying defenses while meeting industry standards.
Full-Scale Attack Simulation:
Applying knowledge and skills in a realistic, high-stakes environment.
Mitigating IP spoofing and safeguarding against man-in-the-middle (MiTM) attacks.
Gaining hands-on experience in a comprehensive attack scenario.
But cybersecurity isn't just about technology—it's about understanding human behavior too. We'll delve into the art of social engineering, teaching you how to recognize and defend against common manipulation tactics attackers use. And we won't forget about the complex legal, regulatory, and security standards landscape. We'll guide you through the intricacies of compliance, ensuring you understand the importance of following best practices while fortifying your defenses.
To put your newfound expertise to the test, we'll provide a full-scale attack simulation. This realistic, high-stakes environment will challenge you to apply your skills in mitigating IP spoofing, safeguarding against man-in-the-middle (MiTM) attacks, and becoming a true cybersecurity champion.
Join us today on this exciting journey to safeguard the digital world. Enroll in our "Mastering Information Security for Absolute Beginners" course and our cutting-edge CyberShield module. Build a secure foundation and gain the confidence to navigate the ever-evolving landscape of information security and cybersecurity.
Arm yourself with the knowledge and skills to protect against cyber threats and become the guardian of the digital realm. Secure the future of information and embark on a path to becoming a confident information security practitioner. Enroll now and unlock your potential in cybersecurity and information security.
Who this course is for:
- Absolute Beginners: This course is designed for individuals who have little to no previous experience in information security or cybersecurity. It provides a solid foundation for beginners to understand the fundamentals and build their knowledge from scratch.
- Professionals Transitioning to Cybersecurity: If you are an IT professional or working in a related field and want to transition into the cybersecurity domain, this course will help you acquire the necessary knowledge and skills to make that transition smoothly.
- Individuals Interested in Cybersecurity: If you have a general interest in cybersecurity and want to explore the field, this course is an excellent starting point. It will provide you with a comprehensive overview of information security and cybersecurity principles.
- Students and Aspiring Professionals: This course is suitable for students studying computer science, information technology, or related fields who want to specialize in cybersecurity. It will serve as a solid foundation for their educational and professional journey.
Welcome to the Comprehensive Cybersecurity and Information Security Course!
Information Security and Cybersecurity Complete Prep course training will help you prep. for GIAC GSEC, Security+, Cysa+Â , and more!!
This beginner-friendly course is your gateway to the exciting world of information security.
Are you an absolute beginner looking to enter the exciting world of information security? Or do you already have a basic understanding of cybersecurity and want to enhance your skills and knowledge? Look no further! This comprehensive program empowers you to master the fundamentals and build a strong foundation in protecting digital assets.
Throughout the course, we will guide you step-by-step through the essential concepts, tools, and practices that form the backbone of information security. You will gain a solid grasp of the core principles that underpin effective cybersecurity strategies, including the CIA (Confidentiality, Integrity, Availability) triad and the differentiation between threats, vulnerabilities, and risks.
But we won't stop there. This program goes beyond basic information security and delves into the captivating world of cybersecurity. Our CyberShield module is designed to equip you with the skills and knowledge to become a formidable defender against the ever-evolving threats in our digital landscape.
You'll uncover the secrets behind encryption and its practical benefits, gaining insights into the intricate workings of the cyber kill chain. Dive deep into the OSI model to understand the fundamental layers of secure networks and gain hands-on experience with industry-standard tools like Wireshark, allowing you to examine network traffic and detect potential security breaches.
Our comprehensive approach includes exploring web application penetration testing, where you'll learn how to identify and exploit vulnerabilities such as XSS (Cross-Site Scripting) and SQLi (SQL Injection). You'll also uncover the dark arts of Google Hacking, enabling you to uncover hidden vulnerabilities lurking in plain sight.
students will learn a wide range of essential information security and cybersecurity topics. Here is an overview of what they can expect to learn:
Fundamentals of Information Security:
Understanding the CIA (Confidentiality, Integrity, Availability) triad.
Differentiating between threats, vulnerabilities, and risks.
Exploring security and privacy interplay.
Cybersecurity Concepts:
Exploring the cyber kill chain and understanding the lifecycle of an attack.
Identifying and responding to potential threats proactively.
Understanding different types of threat actors and their motivations.
Malware and Defense:
Investigating the world of malware and its impact.
Implementing strategies to defend against malicious programs.
Network Security:
Understanding the OSI model and its significance in secure network communication.
Protecting against common network attacks like IP spoofing and man-in-the-middle (MiTM) attacks.
Utilizing tools like Wireshark to examine network traffic and detect security breaches.
Web Application Security:
Conducting web application penetration testing.
Identifying and exploiting vulnerabilities like XSS (Cross-Site Scripting) and SQLi (SQL Injection).
Discovering hidden vulnerabilities through Google Hacking.
Social Engineering and Human Behavior:
Recognizing common manipulation tactics used by attackers.
Understanding the art of social engineering and its impact on security.
Developing strategies to defend against social engineering attacks.
Legal, Regulatory, and Security Standards:
Navigating the complex landscape of legal and regulatory requirements.
Understanding the importance of compliance and best practices.
Fortifying defenses while meeting industry standards.
Full-Scale Attack Simulation:
Applying knowledge and skills in a realistic, high-stakes environment.
Mitigating IP spoofing and safeguarding against man-in-the-middle (MiTM) attacks.
Gaining hands-on experience in a comprehensive attack scenario.
But cybersecurity isn't just about technology—it's about understanding human behavior too. We'll delve into the art of social engineering, teaching you how to recognize and defend against common manipulation tactics attackers use. And we won't forget about the complex legal, regulatory, and security standards landscape. We'll guide you through the intricacies of compliance, ensuring you understand the importance of following best practices while fortifying your defenses.
To put your newfound expertise to the test, we'll provide a full-scale attack simulation. This realistic, high-stakes environment will challenge you to apply your skills in mitigating IP spoofing, safeguarding against man-in-the-middle (MiTM) attacks, and becoming a true cybersecurity champion.
Join us today on this exciting journey to safeguard the digital world. Enroll in our "Mastering Information Security for Absolute Beginners" course and our cutting-edge CyberShield module. Build a secure foundation and gain the confidence to navigate the ever-evolving landscape of information security and cybersecurity.
Arm yourself with the knowledge and skills to protect against cyber threats and become the guardian of the digital realm. Secure the future of information and embark on a path to becoming a confident information security practitioner. Enroll now and unlock your potential in cybersecurity and information security.
Who this course is for:
- Absolute Beginners: This course is designed for individuals who have little to no previous experience in information security or cybersecurity. It provides a solid foundation for beginners to understand the fundamentals and build their knowledge from scratch.
- Professionals Transitioning to Cybersecurity: If you are an IT professional or working in a related field and want to transition into the cybersecurity domain, this course will help you acquire the necessary knowledge and skills to make that transition smoothly.
- Individuals Interested in Cybersecurity: If you have a general interest in cybersecurity and want to explore the field, this course is an excellent starting point. It will provide you with a comprehensive overview of information security and cybersecurity principles.
- Students and Aspiring Professionals: This course is suitable for students studying computer science, information technology, or related fields who want to specialize in cybersecurity. It will serve as a solid foundation for their educational and professional journey.
User Reviews
Rating
GRC Gate Training
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 28
- duration 6:59:46
- Release Date 2024/04/14