Real NMAP : Elite Network Scanning & Recon in 10 Hours|CNMP+
OCSALY Academy | 160.000+ Students
9:57:49
Description
Real Power of Nmap: Master Network Scanning, Reconnaissance and Exploit Discovery for Effective Penetration Testing|2023
What You'll Learn?
- Nmap's network scanning capabilities and how to use them effectively.
- Utilizing NSE scripts to enhance scanning and exploit discovery.
- Port scanning techniques and methodologies for servers.
- Selecting the appropriate network interface for scanning tasks.
- Targeting specific hosts or ranges using target and exclude lists with CIDR notation.
- Operating system detection using Nmap.
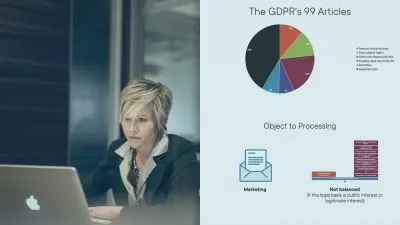
- Legal considerations and compliance when conducting random port scanning.
- Unique techniques specific to Nmap for gaining an edge in scanning and reconnaissance.
- Advanced TCP ACK and SYN scan techniques and their applications.
- Leveraging ICMP for advanced scanning purposes.
- The importance and fundamentals of reconnaissance in information gathering.
- IP geolocation and WhoIS queries using Nmap.
- Conducting graphical traceroutes for visualizing network communication paths.
- Understanding the potential risks associated with different HTTP methods and scanning for them.
- Searching for valuable information and potential vulnerabilities in web servers, aka "Digital Gold."
- Understanding the basics of network protocols and their functions.
- Exploring the layers of the TCP/IP model and their roles in network communication.
- Learning the process of sending and receiving emails over the internet.
- Understanding the concept of Protocol Data Units (PDU) and how they are used in networking.
- Exploring the basic use of switches and data transmission in a network.
- Learning how two networks communicate with each other using a router.
- Getting an introduction to networking and its fundamental concepts.
- Understanding the concept of internetworking and its importance in connecting networks.
- Exploring different types of area networks (ANs) and their characteristics.
- Learning about Local Area Networks (LANs) and their use in connecting devices within a limited area.
- Understanding the concept of Metropolitan Area Networks (MANs) and their role in connecting cities or large areas.
- Exploring Wide Area Networks (WANs) and their use in connecting geographically dispersed networks.
- Introduction to sections and fundamentals of media control filtering in networking.
- Exploring Linux Wireless Access Points (WAP) and bypassing MAC filtering techniques.
- Creating a personal Nmap/Ethical Hacking laboratory for practical learning.
- Getting started with networking concepts and tools.
- Installing and setting up virtual machines for networking experiments.
- Installing and configuring Kali Linux, a popular penetration testing distribution.
- Installing Metasploitable, a vulnerable virtual machine for practicing security testing.
- Understanding and using various Linux commands and pipes for efficient system management.
- Exploring the concept of commands in Linux and how they are used to perform specific tasks.
- Demonstrating examples of using pipelines in Linux for processing and manipulating data.
- Exploring unusual LS (list) command options and their functionalities.
- Learning and using different Linux commands in conjunction with pipes for advanced data processing.
- Understanding key concepts related to Linux operating systems and their functionalities.
- Finding and utilizing helpful manuals and documentation in the Linux environment.
- Exploring Linux directories and their structure for effective file system navigation.
- Continuing the exploration of Linux directories and their significance in organizing files and programs.
- Understanding the shell and its role as an intermediary between the user and the Linux system.
- Gaining knowledge about the fundamentals of processes in a Linux system and how they interact with the operating system.
- and other awesome topics ---->>
Who is this for?
What You Need to Know?
More details
DescriptionUnlock the full potential of Nmap and become a master in network scanning, reconnaissance, and exploit discovery with our comprehensive course!
In today's interconnected world, the ability to understand and secure computer networks is paramount. Nmap, the industry-standard network scanning tool, is a crucial skill for professionals in cybersecurity, network administration, and ethical hacking. Whether you are a beginner looking to learn the basics or an experienced practitioner seeking to refine your skills, this course is designed to take you on an exciting journey through the world of Nmap.
Our course is thoughtfully crafted to provide you with the knowledge and practical skills needed to leverage Nmap effectively. You will start with the fundamentals, learning about Nmap's network scanning capabilities and how to conduct targeted scans to discover open ports, services, and potential vulnerabilities. You will explore the power of Nmap Scripting Engine (NSE) scripts, enabling you to automate and customize your scanning process for more efficient and accurate results.
Delving deeper, you will gain insights into advanced techniques such as TCP ACK and SYN scans, ICMP scanning, and operating system detection. You will discover how to optimize your scanning methodology, select the appropriate network interfaces, and utilize target and exclude lists with CIDR notation for precise targeting. Moreover, you will delve into the legal aspects surrounding scanning, ensuring you are aware of the ethical considerations and compliant with relevant regulations.
Reconnaissance, an essential aspect of penetration testing, will be a focal point of this course. You will learn how to perform IP geolocation, utilize WhoIS queries, and conduct graphical traceroutes to gain valuable insights into the target network's topology and potential attack vectors. Additionally, you will explore scanning HTTP methods, searching for potential risks, and uncovering hidden treasures within web servers.
This course combines theoretical knowledge with hands-on exercises, allowing you to reinforce your understanding and apply your skills in real-world scenarios. With our interactive labs and practical demonstrations, you will gain the confidence to tackle network scanning challenges head-on.
Whether you are an IT professional, aspiring ethical hacker, or cybersecurity enthusiast, this course is your gateway to mastering Nmap and becoming a skilled network scanning expert. Join us today and unlock the secrets of Nmap to fortify your network defenses and excel in your professional endeavors.
Who this course is for:
- Individuals new to network scanning and penetration testing who want to learn the basics of using Nmap.
- IT professionals or system administrators who want to enhance their network scanning skills and gain a deeper understanding of Nmap's capabilities.
- Cybersecurity enthusiasts or hobbyists who are interested in exploring the world of ethical hacking and want to start with a solid foundation in Nmap.
- Students or learners in the field of cybersecurity or information technology who want to expand their knowledge and skills in network scanning and reconnaissance techniques.
Unlock the full potential of Nmap and become a master in network scanning, reconnaissance, and exploit discovery with our comprehensive course!
In today's interconnected world, the ability to understand and secure computer networks is paramount. Nmap, the industry-standard network scanning tool, is a crucial skill for professionals in cybersecurity, network administration, and ethical hacking. Whether you are a beginner looking to learn the basics or an experienced practitioner seeking to refine your skills, this course is designed to take you on an exciting journey through the world of Nmap.
Our course is thoughtfully crafted to provide you with the knowledge and practical skills needed to leverage Nmap effectively. You will start with the fundamentals, learning about Nmap's network scanning capabilities and how to conduct targeted scans to discover open ports, services, and potential vulnerabilities. You will explore the power of Nmap Scripting Engine (NSE) scripts, enabling you to automate and customize your scanning process for more efficient and accurate results.
Delving deeper, you will gain insights into advanced techniques such as TCP ACK and SYN scans, ICMP scanning, and operating system detection. You will discover how to optimize your scanning methodology, select the appropriate network interfaces, and utilize target and exclude lists with CIDR notation for precise targeting. Moreover, you will delve into the legal aspects surrounding scanning, ensuring you are aware of the ethical considerations and compliant with relevant regulations.
Reconnaissance, an essential aspect of penetration testing, will be a focal point of this course. You will learn how to perform IP geolocation, utilize WhoIS queries, and conduct graphical traceroutes to gain valuable insights into the target network's topology and potential attack vectors. Additionally, you will explore scanning HTTP methods, searching for potential risks, and uncovering hidden treasures within web servers.
This course combines theoretical knowledge with hands-on exercises, allowing you to reinforce your understanding and apply your skills in real-world scenarios. With our interactive labs and practical demonstrations, you will gain the confidence to tackle network scanning challenges head-on.
Whether you are an IT professional, aspiring ethical hacker, or cybersecurity enthusiast, this course is your gateway to mastering Nmap and becoming a skilled network scanning expert. Join us today and unlock the secrets of Nmap to fortify your network defenses and excel in your professional endeavors.
Who this course is for:
- Individuals new to network scanning and penetration testing who want to learn the basics of using Nmap.
- IT professionals or system administrators who want to enhance their network scanning skills and gain a deeper understanding of Nmap's capabilities.
- Cybersecurity enthusiasts or hobbyists who are interested in exploring the world of ethical hacking and want to start with a solid foundation in Nmap.
- Students or learners in the field of cybersecurity or information technology who want to expand their knowledge and skills in network scanning and reconnaissance techniques.
User Reviews
Rating
OCSALY Academy | 160.000+ Students
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 84
- duration 9:57:49
- English subtitles has
- Release Date 2023/07/31