Public Key Infrastructure (PKI) with OpenSSL (RSA and ECC)
Holczer Balazs
3:33:34
Description
Understand Public Key Infrastructure (PKI), OpenSSL, CSR, Certificates, Public Key Cryptosystems (RSA and ECC) in Java
What You'll Learn?
- Understand the basics of public key crypto-systems
- Understand the basics of public key infrastructure (PKI)
- Understand certificates (root and intermediate certificates)
- Understand certificate signing requests (CSRs)
- Understand RSA and ECC
- Understand TLS protocol
Who is this for?
What You Need to Know?
More details
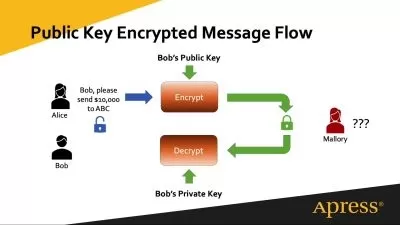
DescriptionIn this course you will learn about cryptography, certificates and certificate signing requests (CSRs) with OpenSSL. You will understand the most popular pubic key (asymmetric) cryptosystems on a step by step basis - such as RSA and Elliptic Curve cryptosystems. You can learn about the theory as well as the implementation for every approach.
Chapter 1 - Cryptography Fundamentals
what is the aim of cryptography?
private key and public key cryptosystems
Chapter 2 -Â Public and Private Keys in OpenSSL
generating RSA keys
encryption example with RSA
generating ECC keys
Chapter 3 - Certificates
root certificates (self-signed certificates) and intermediate certificates
certificate parameters and configuration files
Chapter 4 - Certificate Signing Request (CSR)
what are certificate signing requests?
signing intermediate certificates
verifying the chain of trust
Chapter 5 - Transport Layer Protocol (TLS)
what is the transport layer protocol?
how network communication works
certificate revocation list (CRL)
Chapter 6 - RSA Algorithm
RSA algorithm theory
the problem of factorization
is it possible to crack RSA algorithm?
Chapter 7 - Elliptic Curve Cryptography (ECC)
elliptic curve cryptography theory
double and add algorithm
point addition algorithm
digital signatures with elliptic curves
why does Bitcoin use elliptic curve cryptography?
is it possible to crack elliptic curves?
Thanks for joining my course, let's get started!
Who this course is for:
- Anyone curious about cryptography!
In this course you will learn about cryptography, certificates and certificate signing requests (CSRs) with OpenSSL. You will understand the most popular pubic key (asymmetric) cryptosystems on a step by step basis - such as RSA and Elliptic Curve cryptosystems. You can learn about the theory as well as the implementation for every approach.
Chapter 1 - Cryptography Fundamentals
what is the aim of cryptography?
private key and public key cryptosystems
Chapter 2 -Â Public and Private Keys in OpenSSL
generating RSA keys
encryption example with RSA
generating ECC keys
Chapter 3 - Certificates
root certificates (self-signed certificates) and intermediate certificates
certificate parameters and configuration files
Chapter 4 - Certificate Signing Request (CSR)
what are certificate signing requests?
signing intermediate certificates
verifying the chain of trust
Chapter 5 - Transport Layer Protocol (TLS)
what is the transport layer protocol?
how network communication works
certificate revocation list (CRL)
Chapter 6 - RSA Algorithm
RSA algorithm theory
the problem of factorization
is it possible to crack RSA algorithm?
Chapter 7 - Elliptic Curve Cryptography (ECC)
elliptic curve cryptography theory
double and add algorithm
point addition algorithm
digital signatures with elliptic curves
why does Bitcoin use elliptic curve cryptography?
is it possible to crack elliptic curves?
Thanks for joining my course, let's get started!
Who this course is for:
- Anyone curious about cryptography!
User Reviews
Rating
Holczer Balazs
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 35
- duration 3:33:34
- Release Date 2024/03/12