Prepare for the (ISC)2 CCSP exam! - All six domains!
Gwen Bettwy
18:39:02
Description
Covering all six domains of the August 2022 exam update!
What You'll Learn?
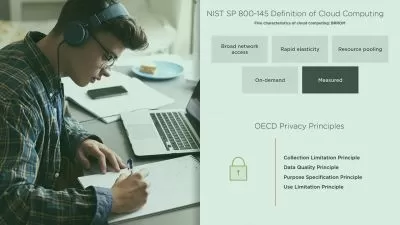
- Understand the architecture of the cloud, from the customer and provider perspectives.
- Understand security within the cloud. e.g., encryption, firewalls, network security groups, etc.
- Understand Identity and Access Management within the cloud.
- Be able to discuss the shared responsibility model for cloud structures.
- Be able to describe the relationship between laws, international and country standards, contracts and the cloud.
- Have a clear understanding of the o
Who is this for?
More details
DescriptionIn this course we walk through all of the critical concepts within the Certified Cloud Security Professional exam outline. I will guide you through all of the concepts that you need to know and advise you on the level of knowledge that you need to get comfortable with.
There are over 18 hours of video content. There are a variety of reference documents throughout the course. Do watch for them. They include my cloud guardians book, my slides, as well as other useful documents such as the CSA guidance 4.0.
We will explore information security in the cloud. A lot of information security remains the same when you transition to the cloud, but a lot changes. Everything is in here from Governance, Risk management, and Compliance (GRC) to encryption and building data centers.
Most of this exam you should think from a customer perspective looking toward the cloud provider. However, there are points, especially in domains three and five, that the perspective of the exam question can and will change to that of a cloud provider.
A solid understanding of networking involved in data centers is explored including firewalls, network security groups, intrusion detection systems, intrusion prevention systems and more. Fundamentally this is a datacenter course. If networking is a new topic to watch and learn about networking.
There is plenty of information in here about the cloud and how it works. What I do say though, is the more you know the easier this test gets. 20 years of teaching CISSP and a deep dive into OpenStack made this exam easy for this instructor. Be careful, this is not an easy test, but the more you know the easier it gets.
Who this course is for:
- Anyone wishing to pursue their CCSP credential.
In this course we walk through all of the critical concepts within the Certified Cloud Security Professional exam outline. I will guide you through all of the concepts that you need to know and advise you on the level of knowledge that you need to get comfortable with.
There are over 18 hours of video content. There are a variety of reference documents throughout the course. Do watch for them. They include my cloud guardians book, my slides, as well as other useful documents such as the CSA guidance 4.0.
We will explore information security in the cloud. A lot of information security remains the same when you transition to the cloud, but a lot changes. Everything is in here from Governance, Risk management, and Compliance (GRC) to encryption and building data centers.
Most of this exam you should think from a customer perspective looking toward the cloud provider. However, there are points, especially in domains three and five, that the perspective of the exam question can and will change to that of a cloud provider.
A solid understanding of networking involved in data centers is explored including firewalls, network security groups, intrusion detection systems, intrusion prevention systems and more. Fundamentally this is a datacenter course. If networking is a new topic to watch and learn about networking.
There is plenty of information in here about the cloud and how it works. What I do say though, is the more you know the easier this test gets. 20 years of teaching CISSP and a deep dive into OpenStack made this exam easy for this instructor. Be careful, this is not an easy test, but the more you know the easier it gets.
Who this course is for:
- Anyone wishing to pursue their CCSP credential.
User Reviews
Rating
Gwen Bettwy
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 161
- duration 18:39:02
- Release Date 2023/04/11