Practical Industrial Control System Penetration Testing
Marcel Rick-Cen
2:12:00
Description
PICSPT - Your practical and offensive workshop for newcomers to ICS/OT Security 2023
What You'll Learn?
- Show your pentest skills on 6 interactive industrial controller simulations
- Build your own ICS pentest platform with open source tools
- NO exploits, privilege escalation nor root shells
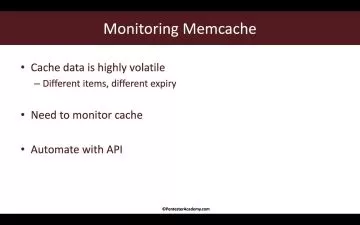
- Learn the typical attack surfaces of an ICS
- Workshop with high practical part with more than 30 tasks
Who is this for?
More details
DescriptionHacking ICS/OT on shodan or in your own company? Better not!
I believe that the best way to learn is with practical experience. OT Security is a new and important skill for all technicians and engineers working on industrial control systems. There are quite a few open source tools that can be used to investigate the cyber security of industrial control systems, but unfortunately there is no suitable training opportunity.
For learners of IT pentesting, there are plenty of opportunities like HackTheBox or VulnHub, where pentest tools and hacking skills can be tried out. Training platforms with ICS focus either don't exist or come in the form of a boring seminar with over 1000€ participation fee.
In this workshop you will learn important pentest tools from Kali and open source tools and you can try them out in 6 interactive simulations of industrial controllers. Of course the simulations are not perfect, so I will show you the tools and techniques on two real PLCs.
The workshop has a high practical part and encourages you to participate! There are more than 30 exciting tasks waiting for you, with which you can deepen your skills bit by bit!
Important: The pentesting of ICS cannot be compared to the typical pentesting of the IT world. Industrial plants need to be continuously available and hardly any plant operator wants to risk a production stop. Typically, security testing is performed at the lowest or second lowest aggressiveness level. So if you are hoping to pwn your device with buffer overflows, kernel exploits, privilege escalation and root shells, you are in the wrong place.
Are you interested in security analysis of ICS and do you already have basic knowledge of industrial cyber security? Then this is the right place for you!
Are you currently studying for the (CEH) Certified Ethical Hacker? From v12 on knowledge in OT is required! This course offers you a hands-on introduction to understand the typical vulnerabilities of OT hardware!
Please note that the software used is not mine. I can only offer limited assistance in case of problems. Please contact the publisher of the software for help. The installation instructions were created to the best of my knowledge, but the responsibility for the installation lies with the participants.
Who this course is for:
- Curious people who want to look at an industrial control system from the attacker's perspective
- Beginners with basic knowledge of industrial cyber security
- CEHv12 Participants
Hacking ICS/OT on shodan or in your own company? Better not!
I believe that the best way to learn is with practical experience. OT Security is a new and important skill for all technicians and engineers working on industrial control systems. There are quite a few open source tools that can be used to investigate the cyber security of industrial control systems, but unfortunately there is no suitable training opportunity.
For learners of IT pentesting, there are plenty of opportunities like HackTheBox or VulnHub, where pentest tools and hacking skills can be tried out. Training platforms with ICS focus either don't exist or come in the form of a boring seminar with over 1000€ participation fee.
In this workshop you will learn important pentest tools from Kali and open source tools and you can try them out in 6 interactive simulations of industrial controllers. Of course the simulations are not perfect, so I will show you the tools and techniques on two real PLCs.
The workshop has a high practical part and encourages you to participate! There are more than 30 exciting tasks waiting for you, with which you can deepen your skills bit by bit!
Important: The pentesting of ICS cannot be compared to the typical pentesting of the IT world. Industrial plants need to be continuously available and hardly any plant operator wants to risk a production stop. Typically, security testing is performed at the lowest or second lowest aggressiveness level. So if you are hoping to pwn your device with buffer overflows, kernel exploits, privilege escalation and root shells, you are in the wrong place.
Are you interested in security analysis of ICS and do you already have basic knowledge of industrial cyber security? Then this is the right place for you!
Are you currently studying for the (CEH) Certified Ethical Hacker? From v12 on knowledge in OT is required! This course offers you a hands-on introduction to understand the typical vulnerabilities of OT hardware!
Please note that the software used is not mine. I can only offer limited assistance in case of problems. Please contact the publisher of the software for help. The installation instructions were created to the best of my knowledge, but the responsibility for the installation lies with the participants.
Who this course is for:
- Curious people who want to look at an industrial control system from the attacker's perspective
- Beginners with basic knowledge of industrial cyber security
- CEHv12 Participants
User Reviews
Rating
Marcel Rick-Cen
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 107
- duration 2:12:00
- Release Date 2023/05/06