Practical Cybersecurity for IT Professionals
Malcolm Shore
2:26:08
Description
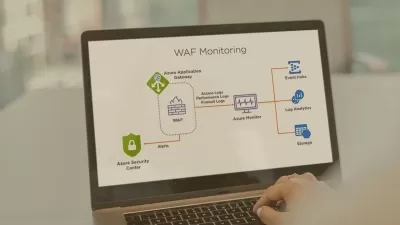
Learn how to protect your network from cyberattacks through practical, hands-on demonstrations. In this course, Malcolm Shore shows how to use the latest tools to discourage and combat hackers, phishers, and snoops attempting to infiltrate your Windows and Linux systems. Learn what forms cyberattacks can take, as well as the two most common types of protection you can build into your system: Antivirus protection and firewalls. Then, learn how to scan your network for suspicious files, check what services are exposed on your systems, and identify vulnerabilities at the host level with Nessus scans. Malcolm also shows how to combat application-level threats, identify weak points in your web applications, and monitor packet-level activity on your network.
More details
User Reviews
Rating
Malcolm Shore
Instructor's Courses
Linkedin Learning
View courses Linkedin Learning- language english
- Training sessions 39
- duration 2:26:08
- Release Date 2023/01/19