Practical and Hands-On Malware Analysis (With Live Demos)
Cyberworkforce365.com Llc
2:18:59
Description
Beginner and Intermediate Course on Malware Analysis
What You'll Learn?
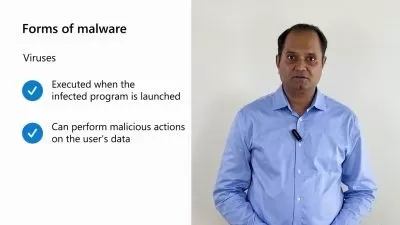
- Fundamentals of malware concepts and malware analysis
- Set up malware analysis lab to study the malware.
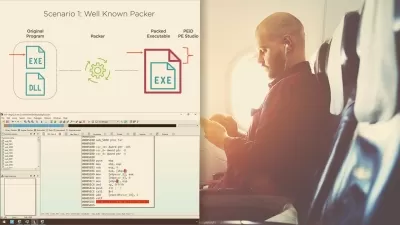
- Practice how to conduct static analysis of malware
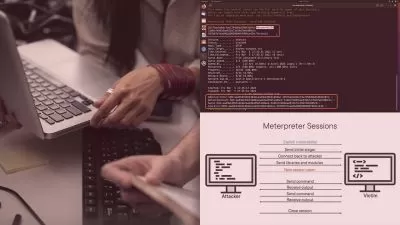
- Practice how to conduct dynamic analysis of malware
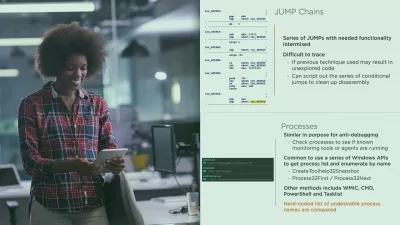
- Master different techniques that the malware uses to evade detection
- Gain experience in working with cutting edge technologies used to analyze malware
- Gain mastery in detection of malware agaianst organizations
Who is this for?
What You Need to Know?
More details
DescriptionAttackers use malware as the primary weapon to exploit systems. Organizations across the globe lose millions of dollars through data breaches caused by malware creators. Hiring managers find it challenging to fill in malware positions because most security analysts have not developed malware analysis skills. This course can train you for a career in any anti-virus company worldwide or give you skills to analyze and stop breaches to organizations you work with.
This course is intended for anyone who wants to know how malware analysis and reverse engineering of software is performed.
This course introduces the basic concepts of malware, different types of malware, and the malware analysis process. Before moving on with practical and hands-on malware analysis, students will set up their secured lab for malware analysis. Students will get familiar with the basic techniques of static and dynamic malware analysis and will be allowed to practice all the labs.
Students will learn to analyze malware and understand malware anatomy using various tools and techniques. The course has some hands-on sections that enable students to practice malware analysis in a virtual environment. The system helps set up their virtual lab using VirtualBox. The instructor and lab manual help students complete demos in the last area.
By the end of the course, you'll have solid knowledge that will enable you to analyze most malware programs.
I am looking forward to walking this journey with you and ensuring you gain mastery and expertise in malware analysis.
Who this course is for:
- People considering a career (or training) in cyber security
- Computer Repairers who clean up infected machines
- Anyone interested in learning malware analysis
- Security Operations center (SOC) analysts interested in learning malware analysis
- Incident responders seeking to learn about malware
Attackers use malware as the primary weapon to exploit systems. Organizations across the globe lose millions of dollars through data breaches caused by malware creators. Hiring managers find it challenging to fill in malware positions because most security analysts have not developed malware analysis skills. This course can train you for a career in any anti-virus company worldwide or give you skills to analyze and stop breaches to organizations you work with.
This course is intended for anyone who wants to know how malware analysis and reverse engineering of software is performed.
This course introduces the basic concepts of malware, different types of malware, and the malware analysis process. Before moving on with practical and hands-on malware analysis, students will set up their secured lab for malware analysis. Students will get familiar with the basic techniques of static and dynamic malware analysis and will be allowed to practice all the labs.
Students will learn to analyze malware and understand malware anatomy using various tools and techniques. The course has some hands-on sections that enable students to practice malware analysis in a virtual environment. The system helps set up their virtual lab using VirtualBox. The instructor and lab manual help students complete demos in the last area.
By the end of the course, you'll have solid knowledge that will enable you to analyze most malware programs.
I am looking forward to walking this journey with you and ensuring you gain mastery and expertise in malware analysis.
Who this course is for:
- People considering a career (or training) in cyber security
- Computer Repairers who clean up infected machines
- Anyone interested in learning malware analysis
- Security Operations center (SOC) analysts interested in learning malware analysis
- Incident responders seeking to learn about malware
User Reviews
Rating
Cyberworkforce365.com Llc
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 20
- duration 2:18:59
- Release Date 2024/02/14