Phishing Mastery: Social-Engineering Hacking Masterclass
Rencora Security
2:06:44
Description
Master Phishing Attacks - Learn real hacking and how to bypass all MFA security
What You'll Learn?
- In-depth knowledge of phishing fundamentals, MFA vulnerabilities, and modern enterprise 2FA bypass techniques using Evilginx.
- This course was designed by hackers to help students land jobs in penetration testing
- How to deploy & understand MITM phishing attacks
- Building comprehensive defense strategies against MITM attacks, focusing on the utilization of Evilginx and its add-ons.
- Insights into the evolution of phishing and cyber attacks, showcasing the shift from simple scams to advanced, targeted tactics.
- Comprehensive setup of a pentesting environment, including VPS, domain registration, Git, Golang, and crucial software updates.
- Techniques for executing sophisticated phishing attacks, mastering session token decoding, and effective cookie management.
- In-depth knowledge of phishing fundamentals, MFA vulnerabilities, and modern enterprise 2FA bypass techniques using Evilginx.
Who is this for?
What You Need to Know?
More details
DescriptionModern Phishing Mastery: Social Engineering Masterclass takes you on an explorative journey through the ever-evolving landscape of cybersecurity, emphasizing the critical role of enterprise phishing awareness and defense. This course, extensive in content and rich in practical knowledge, is designed to transform beginners into adept cybersecurity practitioners capable of understanding and mitigating sophisticated cyber threats.
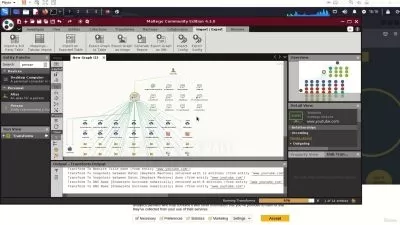
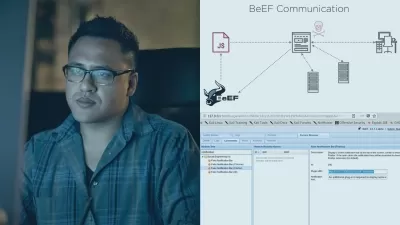
At the core of this training is the advanced study of Evilginx – a potent, open-source tool that signifies a paradigm shift in phishing attacks. By circumventing multi-factor authentication, Evilginx enables an attacker to capture sensitive credentials with a finesse that traditional security measures often fail to detect. You'll delve deep into the architecture of Evilginx, learning how it operates as a man-in-the-middle proxy, intercepting communications to seamlessly harvest credentials and session cookies, and thereby bypassing MFA protocols.
The course meticulously unpacks the vulnerabilities of modern MFA systems, challenging the over-reliance on usernames and passwords as defense mechanisms. Through live demonstrations and hands-on workshops, you will master the nuances of Evilgin, and other sophisticated phishing tools, empowering you to craft and execute compelling phishing campaigns that mimic real-world attack scenarios.
You'll learn to apply your skills within authorized environments, ensuring that your expertise contributes constructively to the cybersecurity community. Post-engagement strategies form a crucial part of the course content. You will engage with best practices for the responsible dismantling of phishing setups and thorough reporting of engagement outcomes. By the end of the course, you'll be adept at erasing digital footprints, minimizing attribution risks, and aiding organizations in remediation and fortification against future attacks.
Furthermore, the course anticipates the future of cybersecurity threats and prepares you to stay ahead. By emphasizing the importance of continuous learning and adaptation, it equips you with the mindset and skills to navigate the rapidly changing cyber threat landscape.
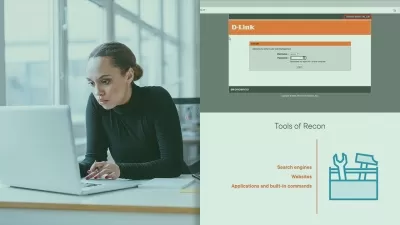
Evolution of Phishing: Explore the history and evolution of phishing attacks from basic techniques in the 90s to today's advanced strategies, understanding how they adapt and evolve with modern technology.
In-Depth Study of Evilginx: Gain insights into Evilginx3, a professional open-source tool that effectively bypasses multi-factor authentication (MFA) and captures sensitive data, enhancing your skills in recognizing and countering sophisticated phishing threats.
Vulnerabilities in MFA Systems: Understand the limitations of relying solely on usernames and passwords in current MFA-protected environments, and learn the importance of identifying MFA system vulnerabilities.
Hands-On Phishing Simulations: Participate in practical workshops using tools like Evilginx3 to create and execute convincing phishing campaigns, from email crafting to credential harvesting.
Phishlets and Ethical Hacking: Delve into Phishlets for creating realistic phishing simulations and focus on ethical hacking principles, ensuring the responsible use of acquired skills for defensive purposes for enterprise security.
Post-Engagement Strategies and Future Trends: Learn best practices for concluding phishing operations responsibly and prepare for future cybersecurity challenges with a focus on continuous adaptation and learning.
Post-engagement strategies, including documentation and remediation measures, are covered, equipping you with best practices to responsibly conclude phishing operations. The course prepares you for the future of cybersecurity, focusing on continuous learning to stay ahead of evolving threats.
This course ideal for everyone of all skill levels from complete beginners, interns, students, cybersecurity enthusiasts to IT professionals.
Join us on this transformative educational path and arm yourself with the acumen to tackle sophisticated phishing techniques head-on. Together, we can forge a more secure future in the digital landscape.
Who this course is for:
- Students and interns looking for jobs in Cybersecurity
- Individuals interested in the technical and ethical aspects of hacking, wishing to contribute positively to cybersecurity.
- Working professionals wanting to learn more about cyber attacks
- Ideal for cybersecurity enthusiasts and professionals seeking advanced skills in bypassing MFA and understanding MITM attacks.
- Ethical hackers, penetration testers, and security consultants looking to expand their expertise in sophisticated phishing methods.
- IT security personnel tasked with safeguarding enterprise systems against phishing attacks and understanding attacker psychology.
- Business owners & entrepreneurs who want to learn how to protect against modern Phishing & Malware attacks
Modern Phishing Mastery: Social Engineering Masterclass takes you on an explorative journey through the ever-evolving landscape of cybersecurity, emphasizing the critical role of enterprise phishing awareness and defense. This course, extensive in content and rich in practical knowledge, is designed to transform beginners into adept cybersecurity practitioners capable of understanding and mitigating sophisticated cyber threats.
At the core of this training is the advanced study of Evilginx – a potent, open-source tool that signifies a paradigm shift in phishing attacks. By circumventing multi-factor authentication, Evilginx enables an attacker to capture sensitive credentials with a finesse that traditional security measures often fail to detect. You'll delve deep into the architecture of Evilginx, learning how it operates as a man-in-the-middle proxy, intercepting communications to seamlessly harvest credentials and session cookies, and thereby bypassing MFA protocols.
The course meticulously unpacks the vulnerabilities of modern MFA systems, challenging the over-reliance on usernames and passwords as defense mechanisms. Through live demonstrations and hands-on workshops, you will master the nuances of Evilgin, and other sophisticated phishing tools, empowering you to craft and execute compelling phishing campaigns that mimic real-world attack scenarios.
You'll learn to apply your skills within authorized environments, ensuring that your expertise contributes constructively to the cybersecurity community. Post-engagement strategies form a crucial part of the course content. You will engage with best practices for the responsible dismantling of phishing setups and thorough reporting of engagement outcomes. By the end of the course, you'll be adept at erasing digital footprints, minimizing attribution risks, and aiding organizations in remediation and fortification against future attacks.
Furthermore, the course anticipates the future of cybersecurity threats and prepares you to stay ahead. By emphasizing the importance of continuous learning and adaptation, it equips you with the mindset and skills to navigate the rapidly changing cyber threat landscape.
Evolution of Phishing: Explore the history and evolution of phishing attacks from basic techniques in the 90s to today's advanced strategies, understanding how they adapt and evolve with modern technology.
In-Depth Study of Evilginx: Gain insights into Evilginx3, a professional open-source tool that effectively bypasses multi-factor authentication (MFA) and captures sensitive data, enhancing your skills in recognizing and countering sophisticated phishing threats.
Vulnerabilities in MFA Systems: Understand the limitations of relying solely on usernames and passwords in current MFA-protected environments, and learn the importance of identifying MFA system vulnerabilities.
Hands-On Phishing Simulations: Participate in practical workshops using tools like Evilginx3 to create and execute convincing phishing campaigns, from email crafting to credential harvesting.
Phishlets and Ethical Hacking: Delve into Phishlets for creating realistic phishing simulations and focus on ethical hacking principles, ensuring the responsible use of acquired skills for defensive purposes for enterprise security.
Post-Engagement Strategies and Future Trends: Learn best practices for concluding phishing operations responsibly and prepare for future cybersecurity challenges with a focus on continuous adaptation and learning.
Post-engagement strategies, including documentation and remediation measures, are covered, equipping you with best practices to responsibly conclude phishing operations. The course prepares you for the future of cybersecurity, focusing on continuous learning to stay ahead of evolving threats.
This course ideal for everyone of all skill levels from complete beginners, interns, students, cybersecurity enthusiasts to IT professionals.
Join us on this transformative educational path and arm yourself with the acumen to tackle sophisticated phishing techniques head-on. Together, we can forge a more secure future in the digital landscape.
Who this course is for:
- Students and interns looking for jobs in Cybersecurity
- Individuals interested in the technical and ethical aspects of hacking, wishing to contribute positively to cybersecurity.
- Working professionals wanting to learn more about cyber attacks
- Ideal for cybersecurity enthusiasts and professionals seeking advanced skills in bypassing MFA and understanding MITM attacks.
- Ethical hackers, penetration testers, and security consultants looking to expand their expertise in sophisticated phishing methods.
- IT security personnel tasked with safeguarding enterprise systems against phishing attacks and understanding attacker psychology.
- Business owners & entrepreneurs who want to learn how to protect against modern Phishing & Malware attacks
User Reviews
Rating
Rencora Security
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 28
- duration 2:06:44
- Release Date 2024/05/18