Perform Attacks with Metasploit
Kevin Cardwell
2:09:32
Description
This course will teach you how to leverage Metasploit, attack targets and gain privileged access using multiple techniques.
What You'll Learn?
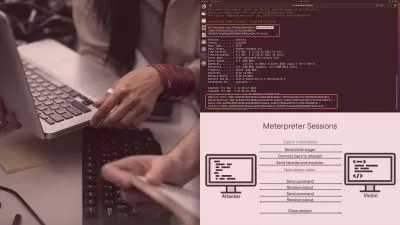
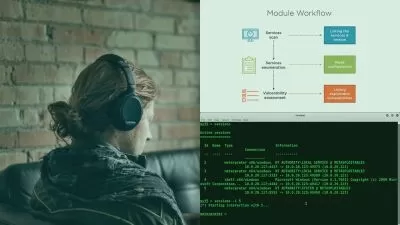
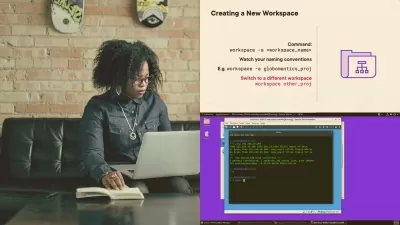
Do you want to work as a penetration tester and to gain more experience in using the more advanced features of Metasploit? In this course, Perform Attacks with Metasploit, you’ll learn to follow a systematic approach and leverage weaknesses at the client side and how to apply methods of post exploitation once access has been gained. First, you’ll explore the process of attacking using implanted executable files for access. Next, you’ll discover how to effectively perform post exploitation with the Meterpreter shell payload. Finally, you’ll learn how to interpret the results from the output of the Metasploit toolkit and create the components of a deliverable report. When you’re finished with this course, you’ll have the skills and knowledge of using attacks against a client and methods to extract the information required for a report by performing post exploitation methods and techniques
More details
User Reviews
Rating
Kevin Cardwell
Instructor's Courses
Pluralsight
View courses Pluralsight- language english
- Training sessions 22
- duration 2:09:32
- level average
- English subtitles has
- Release Date 2023/02/21