Pentesting 101: The Ultimate Hacking Guide Start To Finish
Experts with David Bombal,Wesley Thijs
5:17:32
Description
Pentest like a Pro. Hack like a Pro. This hacking course is created by an experienced hacker and business leader.
What You'll Learn?
- Report, document and properly index pentests
- Handle clients and unexpected situations during/after testing
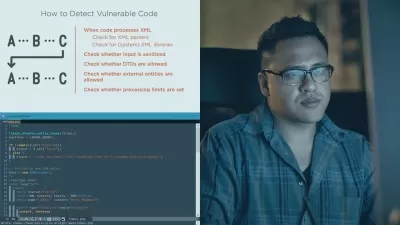
- Web application pentesting
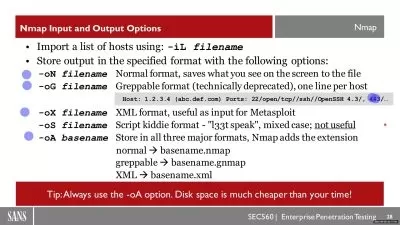
- Network petesting
- API pentesting
Who is this for?
More details
DescriptionWhy you want to take this course
IÂ am not one to keep my company secrets a secret, which kind of defeats the point of the word, but IÂ strongly believe in sharing knowledge. That's why IÂ have created a guide that IÂ think comprehensively covers this whole process. Pentesting is an art form and I'd like to teach how to do it.
What is this course?
This course takes you through 10 modules, each having it's own objective with a capstone assignment that will guide you through network pen-testing, web, and even APIÂ pen-testing. I've created practical labs to guide you through the process so you are not just theoretically richer after completing this course.
Who am I?Â
Let's start with the obligated section about who I am first. My name is Wesley Thijs and i have been an instructor and public figure for about 4 years, garnering 100 000+ students in my time doing it. Recently, however, I wanted to expand my business and I included pen testing as a service we offer. This means we also sometimes get requests for hundreds of hours of testing and this is impossible to do alone. I manage a team of several highly skilled cybersecurity professionals I have been able to pick out over the years I have been training.
My team needed a standard way of testing and a standard education however so IÂ created this plan to teach them how to pentest, how to handle clients, and everything involved in successfully completing an assignment from start to finish.
Who this course is for:
- Hackers wanting to get into pentesting
- Pentesters wanting to start a company
Why you want to take this course
IÂ am not one to keep my company secrets a secret, which kind of defeats the point of the word, but IÂ strongly believe in sharing knowledge. That's why IÂ have created a guide that IÂ think comprehensively covers this whole process. Pentesting is an art form and I'd like to teach how to do it.
What is this course?
This course takes you through 10 modules, each having it's own objective with a capstone assignment that will guide you through network pen-testing, web, and even APIÂ pen-testing. I've created practical labs to guide you through the process so you are not just theoretically richer after completing this course.
Who am I?Â
Let's start with the obligated section about who I am first. My name is Wesley Thijs and i have been an instructor and public figure for about 4 years, garnering 100 000+ students in my time doing it. Recently, however, I wanted to expand my business and I included pen testing as a service we offer. This means we also sometimes get requests for hundreds of hours of testing and this is impossible to do alone. I manage a team of several highly skilled cybersecurity professionals I have been able to pick out over the years I have been training.
My team needed a standard way of testing and a standard education however so IÂ created this plan to teach them how to pentest, how to handle clients, and everything involved in successfully completing an assignment from start to finish.
Who this course is for:
- Hackers wanting to get into pentesting
- Pentesters wanting to start a company
User Reviews
Rating
Experts with David Bombal
Instructor's CoursesWesley Thijs
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 84
- duration 5:17:32
- Release Date 2023/05/06