Penetration Testing Tools Online Training
Bob Salmans
19:08:43
Description
This intermediate Penetration Testing Tools training prepares learners to recognize when to use different tools and software to round out their penetration testing repertoire and provide an understanding of a target's vulnerabilities. This training is also associated with the CompTIA PenTest+ certification.
In the world of network and system security, few subjects carry as much excitement or mystery as penetration testing. But penetration testing has a dirty little secret: a lot of the work is done with industry tools. Sure they're not fire-and-forget or mindless seek-and-destroy missiles, but a lot of the mystique that surrounds penetration tests can, in fact, be duplicated.
More details
This Penetration Testing Tools training familiarizes security technicians with many of the tools that can be used to carry out penetration tests and secure networks against real threats.
For anyone who leads a technology team, this CompTIA training can be used to onboard new security technicians, curated into individual or team training plans, or as a CompTIA reference resource.
Penetration Testing Tools: What You Need to Know
This Penetration Testing Tools training has videos that cover topics such as:
- Identifying vulnerabilities and building a plan of attack
- Exploiting targets revealed in scans and attacking devices
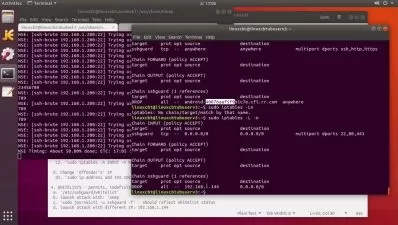
- Deploying industry pentest tools like Kali, network mappers, password crackers, and more
Who Should Take Penetration Testing Tools Training?
This Penetration Testing Tools training is considered foundational-level CompTIA training, which means it was designed for security technicians. This pentration testing skills course is valuable for new IT professionals with at least a year of experience with penetration testing tools and experienced security technicians looking to validate their CompTIA skills.
New or aspiring security technicians. For brand new security technicians, this Penetration Testing Tools training might be slightly specialized -- there are fundamentals about network security that will provide a better foundation for a career at the very outset. However, learning how to use the tools used in penetration tests can make you a better network security operator and can eventually lead to getting placed on pentest teams -- prepare for that eventuality with this training.
Experienced security technicians. If you've been working as a security technician for several years and you've been itching to advance in your career into doing penetration tests, this training will familiarize you with the tools that make them happen. Some are open source, others are paid products, but knowing the tools that support penetration testing can prepare you for the more advanced work of pentests and secure your place on those teams.
User Reviews
Rating
Bob Salmans
Instructor's CoursesI love seeing and helping people advance through life. It's my small part in contributing to the advancement of the security community.
Bob got his start in IT after enlisting in the United States Navy and being assigned to a network engineer role. He brings seven years of IT training experience to CBT Nuggets along with over 20 years of IT experience. Bob was a security team lead for a managed services provider before joining CBTN. In his spare time, he enjoys spending time with his family, cooking, and metal and woodworking.
Certifications: Microsoft MCSE, Cisco CCNP, Cisco CCDP, Cisco CCNA Security, CISSP, CCSP, GPEN, CISA, CISM, CompTIA Security+, CompTIA CySA+, CompTIA Pentest+
Areas of expertise: Information security, networking, active directory, Linux

CBT Nuggets
View courses CBT Nuggets- language english
- Training sessions 146
- duration 19:08:43
- Release Date 2023/07/16