Penetration Testing: Malware backdoor for beginners
Bassam Darweesh
38:54
Description
Learn the different types of Malware & how to do ethical hacking, penetration testing and get access on a system
What You'll Learn?
- Step by step of how to build your own virtual hacking environment & penetration testing Lab
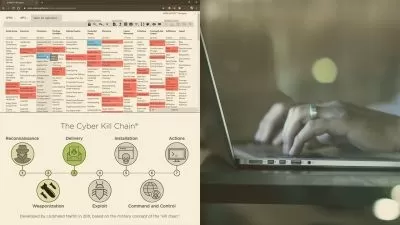
- Learn & Understand the different types of malware
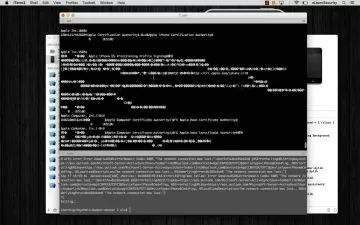
- Learn How to Use NCAT for getting access on a victim's Computer through internal network
- Learn How to Use reverse connection for getting access through external network (from the internet)
- Learn How to Create a persistent backdoor
- Learn How to Use the Metasploit & meterpreter shell for getting access & control on a system
- A detailed pdf documents are available for deep dive information
Who is this for?
What You Need to Know?
More details
DescriptionWelcome to our Course "Penetration Testing: Malware backdoor for beginners "
This course will take you on a journey of learning what malware is, how to create backdoor with NCAT and how you can get control over a system.
Once you are able to understand how hackers think, you will be able to use your new skills to continue your learning in ethical hacking and penetration testing.
We have designed this course to enable those aspiring to enter the information security field to learn concepts on malware/backdoor. By the end of this course, you will be familiar with the various types of malware attacks and able to create a backdoor & get access and control to a System
This course is perfect for anybody who is passionate about developing their skills in the field of Ethical Hacking, Penetration Testing, Cyber Security and Information Security. No prior training is required to take this course as we will start with the basics. We welcome anyone with a thirst for learning.
Together, we will walk you through the entire learning process step by step.
With this course you'll get 24/7 support, so if you have any questions you can post them in the Q&A section or send us a message and we'll respond to you
Who this course is for:
- Anyone Planning to be Ethical Hacker, Penetration Tester, Reverse Engineer, Malware Analyst, Security consultants, etc.
- Anyone preparing for CEH, LPT, OSCP, OSCE etc.
Welcome to our Course "Penetration Testing: Malware backdoor for beginners "
This course will take you on a journey of learning what malware is, how to create backdoor with NCAT and how you can get control over a system.
Once you are able to understand how hackers think, you will be able to use your new skills to continue your learning in ethical hacking and penetration testing.
We have designed this course to enable those aspiring to enter the information security field to learn concepts on malware/backdoor. By the end of this course, you will be familiar with the various types of malware attacks and able to create a backdoor & get access and control to a System
This course is perfect for anybody who is passionate about developing their skills in the field of Ethical Hacking, Penetration Testing, Cyber Security and Information Security. No prior training is required to take this course as we will start with the basics. We welcome anyone with a thirst for learning.
Together, we will walk you through the entire learning process step by step.
With this course you'll get 24/7 support, so if you have any questions you can post them in the Q&A section or send us a message and we'll respond to you
Who this course is for:
- Anyone Planning to be Ethical Hacker, Penetration Tester, Reverse Engineer, Malware Analyst, Security consultants, etc.
- Anyone preparing for CEH, LPT, OSCP, OSCE etc.
User Reviews
Rating
Bassam Darweesh
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 11
- duration 38:54
- English subtitles has
- Release Date 2023/09/04