Penetration Testing for LLMs
Christopher Nett
3:11:00
Description
Learn Penetration Testing for LLMs and Generative AI
What You'll Learn?
- Gain foundational knowledge about Generative AI technologies and their applications.
- Understand the core concepts and methodologies involved in penetration testing for Large Language Models (LLMs).
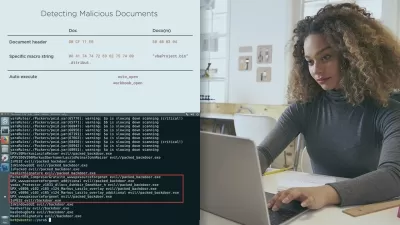
- Learn the step-by-step process of conducting penetration tests specifically tailored for Generative AI systems.
- Study the MITRE ATT&CK framework and its application in Red Teaming.
- Explore the MITRE ATLAS framework for assessing AI and ML security.
- Review the top 10 vulnerabilities for Large Language Models identified by OWASP.
- Learn about common attacks on Generative AI systems and how to defend against them.
- Dive into a practical case study on exploiting vulnerabilities in a Large Language Model.
Who is this for?
What You Need to Know?
More details
DescriptionPenetration Testing for LLMs is a meticulously structured Udemy course aimed at IT professionals seeking to master Penetration Testing for LLMs for Cyber Security purposes. This course systematically walks you through the initial basics to advanced concepts with applied case studies.
You will gain a deep understanding of the principles and practices necessary for effective Penetration Testing for LLMs. The course combines theoretical knowledge with practical insights to ensure comprehensive learning. By the end of the course, you'll be equipped with the skills to implement and conduct Penetration Testing for LLMs in your enterprise.
Key Benefits for you:
GenAI Basics: Gain foundational knowledge about Generative AI technologies and their applications.
Penetration Testing: Understand the core concepts and methodologies involved in penetration testing for Large Language Models (LLMs).
The Penetration Testing Process for GenAI: Learn the step-by-step process of conducting penetration tests specifically tailored for Generative AI systems.
MITRE ATT&CK: Study the MITRE ATT&CK framework and its application in Red Teaming.
MITRE ATLAS: Explore the MITRE ATLAS framework for assessing AI and ML security.
OWASP Top 10 LLMs: Review the top 10 vulnerabilities for Large Language Models identified by OWASP.
Attacks and Countermeasures for GenAI: Learn about common attacks on Generative AI systems and how to defend against them.
Case Study I: Exploit a LLM: Dive into a practical case study on exploiting vulnerabilities in a Large Language Model.
Who this course is for:
- SOC Analyst
- Security Engineer
- Security Consultant
- Security Architect
- Security Architect
- CISO
- Red Team
- Blue Team
- Cybersecurity Professional
- Ethical Hacker
- Penetration Tester
- Incident Handler
- IT Architect
- Cloud Architect
Penetration Testing for LLMs is a meticulously structured Udemy course aimed at IT professionals seeking to master Penetration Testing for LLMs for Cyber Security purposes. This course systematically walks you through the initial basics to advanced concepts with applied case studies.
You will gain a deep understanding of the principles and practices necessary for effective Penetration Testing for LLMs. The course combines theoretical knowledge with practical insights to ensure comprehensive learning. By the end of the course, you'll be equipped with the skills to implement and conduct Penetration Testing for LLMs in your enterprise.
Key Benefits for you:
GenAI Basics: Gain foundational knowledge about Generative AI technologies and their applications.
Penetration Testing: Understand the core concepts and methodologies involved in penetration testing for Large Language Models (LLMs).
The Penetration Testing Process for GenAI: Learn the step-by-step process of conducting penetration tests specifically tailored for Generative AI systems.
MITRE ATT&CK: Study the MITRE ATT&CK framework and its application in Red Teaming.
MITRE ATLAS: Explore the MITRE ATLAS framework for assessing AI and ML security.
OWASP Top 10 LLMs: Review the top 10 vulnerabilities for Large Language Models identified by OWASP.
Attacks and Countermeasures for GenAI: Learn about common attacks on Generative AI systems and how to defend against them.
Case Study I: Exploit a LLM: Dive into a practical case study on exploiting vulnerabilities in a Large Language Model.
Who this course is for:
- SOC Analyst
- Security Engineer
- Security Consultant
- Security Architect
- Security Architect
- CISO
- Red Team
- Blue Team
- Cybersecurity Professional
- Ethical Hacker
- Penetration Tester
- Incident Handler
- IT Architect
- Cloud Architect
User Reviews
Rating
Christopher Nett
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 67
- duration 3:11:00
- Release Date 2024/10/31