Pearson IT - CISSP 3rd Edition
Focused View
10:02:52
50 View
1 - 1.1 Organizational and Professional Ethics.mp4
10:45
2 - 2.1 Information Security Fundamentals.mp4
10:24
3 - 3.1 Strategic Alignment.mp4
10:08
4 - 3.2 Organizational Roles and Responsibilties.mp4
13:27
5 - 3.3 Security Control Frameworks.mp4
11:31
6 - 4.1 Regulatory and Contractual Obligations.mp4
10:35
7 - 4.2 Privacy and Data Protection.mp4
11:48
8 - 5.1 Cybercrime and Data Breaches.mp4
10:04
9 - 5.2 Data Flow.mp4
11:24
10 - 6.1 Investigation Obectives and Requirements.mp4
10:17
11 - 7.1 Governance Documents.mp4
10:10
12 - 8.1 Business Continuity Planning.mp4
09:02
13 - 8.2 Business Impact Analysis.mp4
10:27
14 - 9.1 Personnel Policies and Agreements.mp4
09:27
15 - 9.2 Personnel Security Practices.mp4
11:16
16 - 10.1 Risk Management Concepts.mp4
11:01
17 - 10.2 Risk Management Frameworks.mp4
10:53
18 - 10.3 Risk Assessment.mp4
13:16
19 - 10.4 Controls and Countermeasures.mp4
10:33
20 - 11.1 Threat Actors and Attributes.mp4
13:03
21 - 11.2 Threat Modeling.mp4
09:21
22 - 11.3 Attack Vectors.mp4
11:09
23 - 11.4 Threat Intelligence.mp4
10:41
24 - 12.1 Supply Chain Risk Management.mp4
09:19
25 - 13.1 SETA Principles and Practices.mp4
13:11
26 - 13.2 Social Enginnering.mp4
09:50
27 - 14.1 Asset Classification.mp4
10:42
28 - 15.1 Data and Asset Handling.mp4
08:29
29 - 16.1 Asset Management.mp4
10:52
30 - 17.1 Data Collection and Retention.mp4
11:49
31 - 17.2 Deletion and Destruction.mp4
10:55
32 - 18.1 Asset Lifecycle - EOL.mp4
09:29
33 - 19.1 Control Baselines, Tailoring, and Scoping.mp4
07:21
34 - 19.2 Data Protection Methods.mp4
09:21
35 - 20.1 Secure Design Principles.mp4
10:48
36 - 21.1 Information Security Models.mp4
11:30
37 - 22.1 Security Evaluation Criteria.mp4
08:06
38 - 23.1 Information Systems Security Capabilities.mp4
12:33
39 - 24.1 Traditional Systems Architectures.mp4
08:56
40 - 24.2 Database Systems.mp4
09:12
41 - 24.3 Cloud-based Systems.mp4
13:27
42 - 24.4 Embedded Systems.mp4
09:24
43 - 24.5 IoT and IIoT.mp4
09:01
44 - 24.6 Virtualized Systems.mp4
10:05
45 - 24.7 Automation and Solution Elements.mp4
10:28
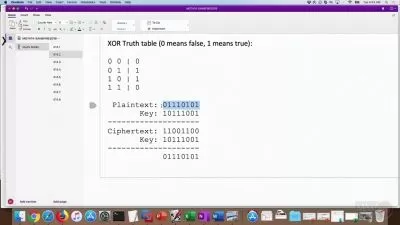
46 - 25.1 Ciphers and Keys.mp4
11:07
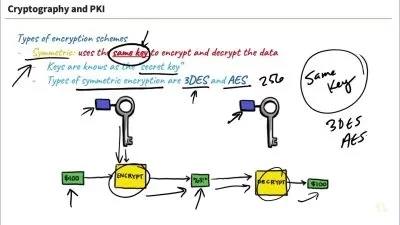
47 - 25.2 Symmetric Encryption.mp4
11:30
48 - 25.3 Asymmetric Encryption.mp4
12:35
49 - 25.4 Hashing and Digital Signatures.mp4
12:36
50 - 25.5 PKI and Digital Certificates.mp4
11:45
51 - 25.6 Emerging Cryptography.mp4
07:46
52 - 26.1 Cryptographic Attacks.mp4
10:45
53 - 26.2 Hash and Kerberos Post-Exploitation Attacks.mp4
09:56
54 - 26.3 Ransomware.mp4
09:16
55 - 27.1 Physical Security Principles.mp4
08:12
56 - 28.1 Site and Building Security.mp4
11:04
57 - 28.2 Environmental Impact.mp4
10:50
More details
User Reviews
Rating
average 0
Focused display

LiveLessons
View courses LiveLessonsPearson's video training library is an indispensable learning tool for today's competitive job market. Having essential technology training and certifications can open doors for career advancement and life enrichment. We take learning personally. We've published hundreds of up-to-date videos on wide variety of key topics for Professionals and IT Certification candidates. Now you can learn from renowned industry experts from anywhere in the world, without leaving home.
- language english
- Training sessions 57
- duration 10:02:52
- Release Date 2023/11/03