PCI DSS: Restricting Access to Cardholder Data
Jacob Ansari
2:06:24
Description
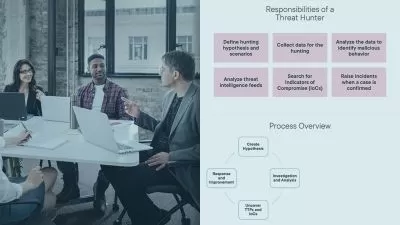
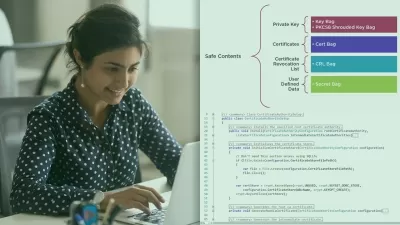
Requirements 7, 8 & 9 of PCI DSS version 3.2.1 are to Implement Strong Access Control Measures for logical and physical cardholder data. You'll understand what each requirement asks for and discover practical guidance from experienced PCI assessors.
What You'll Learn?
The key to achieving PCI DSS compliance is a thorough knowledge of each of the sub-requirements and how they will be assessed. In this course, PCI DSS: Restricting Access to Cardholder Data, you’ll learn how to interpret PCI DSS requirements 7, 8 & 9, and apply them to your organization. First, you’ll learn how PCI DSS wants role-based access and based on least privilege and need to know. Next, you’ll explore the long and prescriptive requirements about username, passwords and multi-factor authentication. Then you’ll take a look at the requirements related to the protection of cardholder data in physical format – written in paper and saved to electronic media. Finally, you’ll discover practical insights about both requirements from experienced PCI assessors. When you’ve finished with this course you will have the skills and knowledge to apply PCI DSS requirements 7, 8 and 9 to any organization’s environment and to determine whether it is compliant with the demands of the standard.
More details
User Reviews
Rating
Jacob Ansari
Instructor's Courses
Pluralsight
View courses Pluralsight- language english
- Training sessions 41
- duration 2:06:24
- level average
- English subtitles has
- Release Date 2023/02/27