OWASP Mobile Top 10 - Vulnerabilities to Avoid
Pack Of Coders - POC
2:17:58
Description
Skills Necessary to Understand the Most Critical Mobile Application Security Risks
What You'll Learn?
- Mobile OWASP Top 10 2023 Coverage
- Details on Each Vulnerability and Strategies for Prevention
- Learn to Threat Mode Each of the Mobile Applications Vulnerabilities
- Identify Best Practices for Secure Mobile Application Design and Coding
- Learn to Integrate Security into the Mobile Development Life Cycle
- Concepts to Support Building Secure iOS and Android Applications
- Find Out How to Apply Best Practices to Detect Vulnerabilities
Who is this for?
What You Need to Know?
More details
DescriptionStay ahead of the curve in the ever-evolving world of mobile application security with our OWASP Mobile Top Ten training. Designed for security professionals, developers, and mobile app testers, this comprehensive course will equip you with the knowledge and skills necessary to understand and mitigate the most critical security risks facing mobile applications today.
Course Highlights:
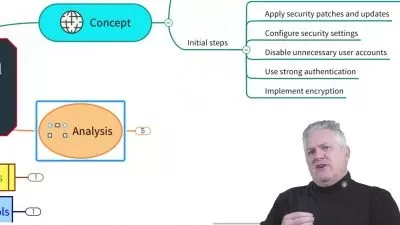
OWASP Mobile Top Ten: Dive deep into the OWASP Mobile Top Ten, a list of the most critical security risks for mobile apps. Learn about vulnerabilities such as insecure authentication, code tampering, flawed encryption, and more!
Understanding Mobile Application Security: Explore the unique challenges and risks associated with mobile app development, including data leakage, insecure data storage, and more.
Risk Assessment and Mitigation: Discover how to assess the risks associated with mobile app development and implement effective mitigation strategies to safeguard your applications and users.
Secure Coding Practices: Gain practical insights into secure coding practices for mobile app development, covering topics like input validation, authentication, authorization, and encryption.
Best Practices for Secure Development: Acquire a set of best practices for integrating security into the mobile app development lifecycle, from design and coding to testing and deployment.
In today's digital world, mobile app security is more critical than ever. Enhance your skills and help protect mobile applications from vulnerabilities that could compromise user data and your organization's reputation. Be prepared to tackle the ever-present challenges in mobile app security with confidence.
Enroll in this course and make a significant impact on your organization's security posture. Join us in the journey towards secure and reliable mobile applications!
Who this course is for:
- Mobile App Developers
- Software Developers
- Architects
- Security Professionals
- IT Professionals
- Anyone Interested in Secure Mobile Development
Stay ahead of the curve in the ever-evolving world of mobile application security with our OWASP Mobile Top Ten training. Designed for security professionals, developers, and mobile app testers, this comprehensive course will equip you with the knowledge and skills necessary to understand and mitigate the most critical security risks facing mobile applications today.
Course Highlights:
OWASP Mobile Top Ten: Dive deep into the OWASP Mobile Top Ten, a list of the most critical security risks for mobile apps. Learn about vulnerabilities such as insecure authentication, code tampering, flawed encryption, and more!
Understanding Mobile Application Security: Explore the unique challenges and risks associated with mobile app development, including data leakage, insecure data storage, and more.
Risk Assessment and Mitigation: Discover how to assess the risks associated with mobile app development and implement effective mitigation strategies to safeguard your applications and users.
Secure Coding Practices: Gain practical insights into secure coding practices for mobile app development, covering topics like input validation, authentication, authorization, and encryption.
Best Practices for Secure Development: Acquire a set of best practices for integrating security into the mobile app development lifecycle, from design and coding to testing and deployment.
In today's digital world, mobile app security is more critical than ever. Enhance your skills and help protect mobile applications from vulnerabilities that could compromise user data and your organization's reputation. Be prepared to tackle the ever-present challenges in mobile app security with confidence.
Enroll in this course and make a significant impact on your organization's security posture. Join us in the journey towards secure and reliable mobile applications!
Who this course is for:
- Mobile App Developers
- Software Developers
- Architects
- Security Professionals
- IT Professionals
- Anyone Interested in Secure Mobile Development
User Reviews
Rating
Pack Of Coders - POC
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 50
- duration 2:17:58
- Release Date 2024/01/13