Operations and Incident Response for CompTIA Security+
Christopher Rees
3:55:10
Description
Experiencing a cyber event is not a question of if, but of when. This course will teach you the skills necessary to assess organizational security and respond to various cyber-related incidents.
What You'll Learn?
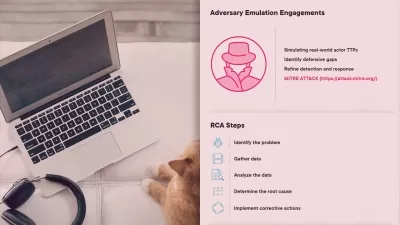
Proper and timely incident response including gathering data and preservation of evidence is critical to a successful response and investigation. In this course, Operations and Incident Response for CompTIA Security+, you’ll learn to how to assess your organizational security and respond to cyber-related incidents. First, you’ll explore the tools and techniques associated with network reconnaissance and discovery. Next, you’ll learn the steps in the incident response process along with the various attack frameworks and testing methodologies. From there, you’ll learn the components of a proper communication plan, business continuity and disaster recovery plan to help prepare for, and respond to, a cyber event. Finally, you’ll learn key aspects of digital forensics. When you’re finished with this course, you’ll have the skills and knowledge necessary to not only plan and prepare for cyber events, but to respond and investigate when they do.
More details
User Reviews
Rating
Christopher Rees
Instructor's Courses
Pluralsight
View courses Pluralsight- language english
- Training sessions 108
- duration 3:55:10
- level preliminary
- English subtitles has
- Release Date 2023/02/07