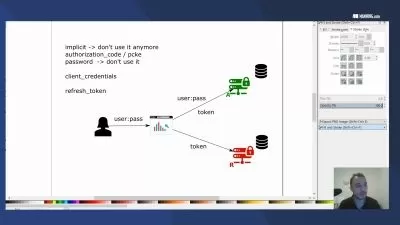
NIST Cybersecurity A-Z NIST Cybersecurity Framework (CSF)
Focused View
4:15:17
28 View
1. Introduction.mp4
06:08
2. Course Notes and Navigation.mp4
03:22
1. The NIST Framework.mp4
03:07
2. NIST Framework Core.mp4
02:55
3. Framework Implementation and Profile.mp4
07:43
4. Recent NIST Developments.mp4
04:42
1. Cybersecurity Risk Planning.mp4
03:45
2. What is a Cyber Security Risk.mp4
04:13
3. Asset Management.mp4
03:55
4. Keeping Hardware Inventory Updated.mp4
08:24
5. Keeping Software Platform Inventory.mp4
04:03
6. Prioritizing Devices, Software and Apps.mp4
03:25
7. Personnel Security Requirements.mp4
05:30
8. Governance.mp4
04:00
9. Risk Assessment and Management.mp4
04:02
10. Identifying Internal and External Threats.mp4
02:42
11. Focus on Highlighted Risk.mp4
03:53
12. Plans for Dealing with the Highest Risk.mp4
03:45
13. Cybersecurity Risk Planning and Management Test.html
1. User and Network Infrastructure.mp4
07:26
2. Authentication and Access Control.mp4
05:28
3. Control List and Remote Access.mp4
04:15
4. Network Security Controls.mp4
09:37
5. Association and Authentication.mp4
05:09
6. Awareness and Training.mp4
02:37
7. Data Security.mp4
05:44
8. Hardware Integrity.mp4
05:51
9. Information Protection.mp4
06:12
10. Patch Management.mp4
05:20
11. Maintenance.mp4
03:30
12. Protective Technology.mp4
04:52
13. Cybersecurity Risk Planning and Management.html
1. Tools and Techniques.mp4
05:49
2. Detecting Incidents.mp4
02:36
3. Anomalies and Events.mp4
05:57
4. Monitor Systems.mp4
07:15
5. Logging Devices and Log Files.mp4
04:05
6. Continuous Monitoring.mp4
10:43
7. Detection Process.mp4
09:49
8. Tools and Techniques for Detecting Cyber Incidents Test.html
1. Developing a Continuity of Operations Plan.mp4
05:28
2. Incident response.mp4
05:21
3. Executable Response Plan.mp4
05:51
4. Importance of Communications.mp4
03:04
5. Incident Analysis.mp4
08:07
6. Mitigation.mp4
05:41
7. Recover.mp4
10:39
8. Developing a Continuity of Operations Plan Test.html
1. Supply Chain Risk Management.mp4
04:42
2. Supply Chain Management Practices.mp4
03:18
3. Incorporating the Supply Chain Category.mp4
04:25
4. Develop, Assess and Test Supply Chain Risks.mp4
06:52
5. Supply Chain Risk Management Test.html
More details
User Reviews
Rating
average 0
Focused display
Category

Udemy
View courses UdemyStudents take courses primarily to improve job-related skills.Some courses generate credit toward technical certification. Udemy has made a special effort to attract corporate trainers seeking to create coursework for employees of their company.
- language english
- Training sessions 48
- duration 4:15:17
- Release Date 2024/04/22










![Data Protection Officer - Foundation Course [CT-DPO]](https://traininghub.ir/image/course_pic/16228-x225.webp)