Networking for Ethical Hacking
Toronto Tech
5:01:33
Description
Neworking for Begginers in Cybersecurity
What You'll Learn?
- Master Networking Fundmentals
- Master Aplication Layer Protcols (Http, smtp,ftp and DNS)
- Master Transport Layer Protocol (TCP and UDP)
- Master Routing techniques and IP addressing
- Master switching ARP and mac address
Who is this for?
More details
DescriptionThis course is designed to provide students with a comprehensive understanding of the networking fundamentals necessary for ethical hacking. Students will gain an in-depth knowledge of networking protocols, application layer protocols, transport layer protocols, networking layer data link layer, Windows networking commands, Linux networking commands, and networking protocols in Wireshark.
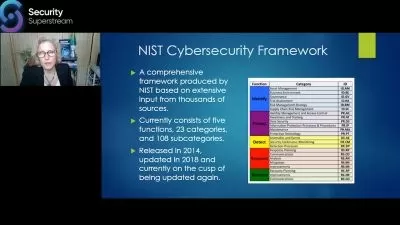
Module 1: Networking Fundamentals In this module, students will learn the basics of networking. They will study concepts such as IP addressing, subnetting, network topologies, OSI model, TCP/IP model, and more. Students will also learn about networking hardware such as routers, switches, and firewalls.
Module 2: Application Layer Protocols This module focuses on application layer protocols, including HTTP, FTP, DNS, SMTP, and more. Students will learn how these protocols work and how to use them for ethical hacking purposes.
Module 3: Transport Layer Protocols In this module, students will learn about transport layer protocols, including TCP and UDP. Students will understand the differences between these protocols and learn how to use them for ethical hacking.
Module 4: Networking Layer Data Link Layer This module focuses on the networking layer and data link layer. Students will study networking devices such as hubs, bridges, and switches. They will also learn about MAC addresses, ARP, and VLANs.
Module 5: Windows Networking Commands This module is dedicated to Windows networking commands. Students will learn how to use command prompt commands such as ipconfig, netstat, ping, and more for ethical hacking purposes.
Module 6: Linux Networking Commands In this module, students will learn about Linux networking commands such as ifconfig, ping, netstat, and more. Students will learn how to use these commands for ethical hacking purposes.
Module 7: Networking Protocols in Wireshark In this final module, students will learn how to use Wireshark to analyze network traffic. Students will learn how to capture and filter traffic, read and interpret packets, and identify network vulnerabilities.
At the end of this course, students will be equipped with a strong understanding of networking fundamentals and how to apply them for ethical hacking purposes. They will have practical experience with Windows and Linux networking commands and be able to use Wireshark to identify vulnerabilities in a network.
Who this course is for:
- Anyone wants to start ethical hacking must know can take this course as first step
This course is designed to provide students with a comprehensive understanding of the networking fundamentals necessary for ethical hacking. Students will gain an in-depth knowledge of networking protocols, application layer protocols, transport layer protocols, networking layer data link layer, Windows networking commands, Linux networking commands, and networking protocols in Wireshark.
Module 1: Networking Fundamentals In this module, students will learn the basics of networking. They will study concepts such as IP addressing, subnetting, network topologies, OSI model, TCP/IP model, and more. Students will also learn about networking hardware such as routers, switches, and firewalls.
Module 2: Application Layer Protocols This module focuses on application layer protocols, including HTTP, FTP, DNS, SMTP, and more. Students will learn how these protocols work and how to use them for ethical hacking purposes.
Module 3: Transport Layer Protocols In this module, students will learn about transport layer protocols, including TCP and UDP. Students will understand the differences between these protocols and learn how to use them for ethical hacking.
Module 4: Networking Layer Data Link Layer This module focuses on the networking layer and data link layer. Students will study networking devices such as hubs, bridges, and switches. They will also learn about MAC addresses, ARP, and VLANs.
Module 5: Windows Networking Commands This module is dedicated to Windows networking commands. Students will learn how to use command prompt commands such as ipconfig, netstat, ping, and more for ethical hacking purposes.
Module 6: Linux Networking Commands In this module, students will learn about Linux networking commands such as ifconfig, ping, netstat, and more. Students will learn how to use these commands for ethical hacking purposes.
Module 7: Networking Protocols in Wireshark In this final module, students will learn how to use Wireshark to analyze network traffic. Students will learn how to capture and filter traffic, read and interpret packets, and identify network vulnerabilities.
At the end of this course, students will be equipped with a strong understanding of networking fundamentals and how to apply them for ethical hacking purposes. They will have practical experience with Windows and Linux networking commands and be able to use Wireshark to identify vulnerabilities in a network.
Who this course is for:
- Anyone wants to start ethical hacking must know can take this course as first step
User Reviews
Rating
Toronto Tech
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 67
- duration 5:01:33
- Release Date 2023/05/17