Network Fundamentals, Security Architecture and IDM-IAM-PAM
ExamIT -Sonia
5:16:11
Description
Network Fundamentals, Security Architecture and IDM-IAM-PAM for Cybersecurity professionals
What You'll Learn?
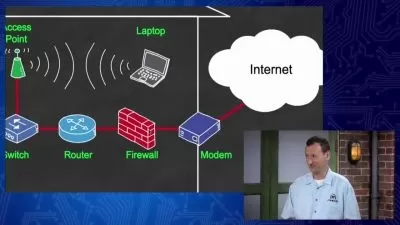
- Explore network topologies, architectures, and protocols commonly used in modern IT environments.
- Understand the principles of security architecture design, including defense-in-depth, least privilege, and separation of duties.
- Understand the role of Privileged Access Management (PAM) in securing privileged accounts and access to critical resources.
- Learn about IAM implementation best practices, including user provisioning, role-based access control (RBAC), and access governance.
Who is this for?
What You Need to Know?
More details
DescriptionThis course offers a comprehensive exploration of network fundamentals, security architecture principles, and Identity and Access Management (IAM) technologies essential for cybersecurity professionals. Participants will gain a solid understanding of networking concepts, security architecture design, and the implementation of IAM solutions to manage identities, access privileges, and privileged accounts effectively. Through a combination of theoretical lectures, practical demonstrations, and hands-on exercises, learners will acquire the knowledge and skills necessary to design, implement, and manage secure network infrastructures and IAM systems in enterprise environments.
Course Objectives:
Master the fundamentals of networking, including OSI model, TCP/IP protocol suite, and network devices.
Explore network topologies, architectures, and protocols commonly used in modern IT environments.
Understand the principles of security architecture design, including defense-in-depth, least privilege, and separation of duties.
Learn about security controls and mechanisms for protecting networks, systems, and data from cyber threats.
Gain insights into Identity and Access Management (IAM) concepts, including authentication, authorization, and accountability.
Explore IAM technologies, such as Single Sign-On (SSO), Multi-Factor Authentication (MFA), and Identity Federation.
Understand the role of Privileged Access Management (PAM) in securing privileged accounts and access to critical resources.
Learn about IAM implementation best practices, including user provisioning, role-based access control (RBAC), and access governance.
Upon completion of this course, participants will be equipped with the knowledge and skills to design, implement, and manage secure network infrastructures and IAM systems, ensuring the confidentiality, integrity, and availability of information assets in enterprise environments.
Who this course is for:
- Cybersecurity professionals seeking to strengthen their knowledge and skills in network fundamentals, security architecture, and IAM technologies.
- Security analysts, system administrators, and network engineers interested in advancing their careers in cybersecurity.
This course offers a comprehensive exploration of network fundamentals, security architecture principles, and Identity and Access Management (IAM) technologies essential for cybersecurity professionals. Participants will gain a solid understanding of networking concepts, security architecture design, and the implementation of IAM solutions to manage identities, access privileges, and privileged accounts effectively. Through a combination of theoretical lectures, practical demonstrations, and hands-on exercises, learners will acquire the knowledge and skills necessary to design, implement, and manage secure network infrastructures and IAM systems in enterprise environments.
Course Objectives:
Master the fundamentals of networking, including OSI model, TCP/IP protocol suite, and network devices.
Explore network topologies, architectures, and protocols commonly used in modern IT environments.
Understand the principles of security architecture design, including defense-in-depth, least privilege, and separation of duties.
Learn about security controls and mechanisms for protecting networks, systems, and data from cyber threats.
Gain insights into Identity and Access Management (IAM) concepts, including authentication, authorization, and accountability.
Explore IAM technologies, such as Single Sign-On (SSO), Multi-Factor Authentication (MFA), and Identity Federation.
Understand the role of Privileged Access Management (PAM) in securing privileged accounts and access to critical resources.
Learn about IAM implementation best practices, including user provisioning, role-based access control (RBAC), and access governance.
Upon completion of this course, participants will be equipped with the knowledge and skills to design, implement, and manage secure network infrastructures and IAM systems, ensuring the confidentiality, integrity, and availability of information assets in enterprise environments.
Who this course is for:
- Cybersecurity professionals seeking to strengthen their knowledge and skills in network fundamentals, security architecture, and IAM technologies.
- Security analysts, system administrators, and network engineers interested in advancing their careers in cybersecurity.
User Reviews
Rating
ExamIT -Sonia
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 9
- duration 5:16:11
- Release Date 2024/07/23