Network Defense Fundamentals: Training for IT Beginners
Meta Brains
3:41:04
Description
Building Strong Foundations in Cybersecurity and Information Protection
What You'll Learn?
- Understanding Network Defense Goals: Learn the purposes and approaches of network defense.
- Basics of Network Security Protocols: Gain knowledge of various network security protocols.
- Linux Fundamentals for Network Security: Acquire basic Linux concepts relevant to network security.
- Types of Network Security Controls: Understand different physical and technical security controls.
- Identification and Authentication Methods: Learn about various identification and authentication techniques.
- Implementing Physical Security Measures: Understand the importance and methods of physical security in network defense.
- Technical Controls like Firewalls and IDS/IPS: Gain insights into firewalls, Intrusion Detection Systems (IDS), and Intrusion Prevention Systems (IPS).
- Virtualization and Cloud Computing Security: Explore security aspects of virtualization and cloud computing.
- Wireless Network Security: Learn about encryption and authentication methods in wireless networks.
- IoT Device Security: Understand security best practices for Internet of Things (IoT) devices.
- Cryptography and Public Key Infrastructure (PKI): Delve into various cryptography techniques and PKI infrastructure.
- Data Security Techniques: Learn about data encryption, backup retention, and data loss prevention solutions.
- Practical Implementation of Security Solutions: Implement and test security solutions like IDS/IPS and VPNs through mini-projects.
Who is this for?
What You Need to Know?
More details
DescriptionIntroducing the "Network Security Mastery" course, a comprehensive training program designed for IT beginners and network students eager to delve into the fundamentals of network security. In today's digital age, safeguarding information and data is of paramount importance, and this course equips participants with the essential knowledge and skills to excel in the field of cybersecurity.
This course is ideal for individuals who may have a basic understanding of Linux programming, as it provides a solid foundation in network defense and information security. Our primary goal is to enable trainees to recognize their competency and expertise in network defense and information security skills, ensuring they are well-prepared to navigate the complexities of the digital landscape.
The curriculum is thoughtfully structured and covers a wide range of topics, making it accessible and engaging for learners at various levels. Here's a glimpse of what you can expect:
Introduction: Explore the objectives of network defense, gain insights into various defense approaches, understand network security controls, and delve into essential Linux concepts.
Identification, Authentication, and Authorization: Learn about different types of identifications, authentications, and authorizations in the context of network security.
Network Security Controls: Understand the importance of physical security, explore physical security attack vectors, and grasp various security controls, including environmental controls.
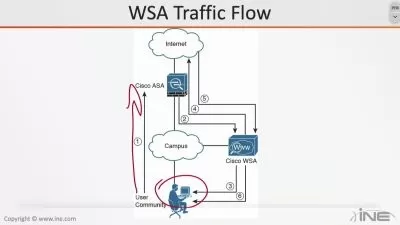
Technical Controls: Dive into network segmentation, firewalls, IDS/IPS, proxy servers, VPNs, and antivirus/anti-malware software.
Virtualization and Cloud Computing: Explore virtualization components, OS virtualization security, cloud computing, and its benefits.
Wireless Network Security: Learn about wireless network encryption, authentication methods, and security measures.
IoT Device Security: Understand IoT architecture and security best practices.
Cryptography and Public Key Infrastructure: Explore cryptography techniques, encryption algorithms, hashing algorithms, and PKI infrastructure.
Data Security: Discover data security controls, including data encryption, file encryption, and data backup retention.
Mini Projects: Gain hands-on experience with the implementation of IDS/IPS, VPN setup, and firewall configuration on Linux-based systems.
By the end of this course, you'll possess a comprehensive understanding of network security and defense, preparing you to tackle real-world challenges in the field. Join us on this journey to become a proficient network security expert. Your cybersecurity career starts here.
Who this course is for:
- IT Beginners: Individuals starting their journey in the information technology field will find this course valuable for building a strong foundation in network defense and security.
- Network Students: Students currently studying in networking or related fields will benefit from the practical, real-world applications of network security concepts covered in this course.
- Aspiring Network Security Professionals: Those aiming to pursue a career in network security will find this course particularly beneficial, as it covers essential skills and knowledge required in the industry.
- IT Professionals Seeking Specialization: IT professionals looking to specialize or enhance their expertise in network defense and security will find this course to be a comprehensive resource.
- System Administrators: System admins who wish to strengthen their network security skills and better protect their infrastructure will gain practical insights and techniques from this course.
- Security Enthusiasts: Individuals with a keen interest in network security and a desire to understand the complexities of protecting networks against threats will find the course engaging and informative.
Introducing the "Network Security Mastery" course, a comprehensive training program designed for IT beginners and network students eager to delve into the fundamentals of network security. In today's digital age, safeguarding information and data is of paramount importance, and this course equips participants with the essential knowledge and skills to excel in the field of cybersecurity.
This course is ideal for individuals who may have a basic understanding of Linux programming, as it provides a solid foundation in network defense and information security. Our primary goal is to enable trainees to recognize their competency and expertise in network defense and information security skills, ensuring they are well-prepared to navigate the complexities of the digital landscape.
The curriculum is thoughtfully structured and covers a wide range of topics, making it accessible and engaging for learners at various levels. Here's a glimpse of what you can expect:
Introduction: Explore the objectives of network defense, gain insights into various defense approaches, understand network security controls, and delve into essential Linux concepts.
Identification, Authentication, and Authorization: Learn about different types of identifications, authentications, and authorizations in the context of network security.
Network Security Controls: Understand the importance of physical security, explore physical security attack vectors, and grasp various security controls, including environmental controls.
Technical Controls: Dive into network segmentation, firewalls, IDS/IPS, proxy servers, VPNs, and antivirus/anti-malware software.
Virtualization and Cloud Computing: Explore virtualization components, OS virtualization security, cloud computing, and its benefits.
Wireless Network Security: Learn about wireless network encryption, authentication methods, and security measures.
IoT Device Security: Understand IoT architecture and security best practices.
Cryptography and Public Key Infrastructure: Explore cryptography techniques, encryption algorithms, hashing algorithms, and PKI infrastructure.
Data Security: Discover data security controls, including data encryption, file encryption, and data backup retention.
Mini Projects: Gain hands-on experience with the implementation of IDS/IPS, VPN setup, and firewall configuration on Linux-based systems.
By the end of this course, you'll possess a comprehensive understanding of network security and defense, preparing you to tackle real-world challenges in the field. Join us on this journey to become a proficient network security expert. Your cybersecurity career starts here.
Who this course is for:
- IT Beginners: Individuals starting their journey in the information technology field will find this course valuable for building a strong foundation in network defense and security.
- Network Students: Students currently studying in networking or related fields will benefit from the practical, real-world applications of network security concepts covered in this course.
- Aspiring Network Security Professionals: Those aiming to pursue a career in network security will find this course particularly beneficial, as it covers essential skills and knowledge required in the industry.
- IT Professionals Seeking Specialization: IT professionals looking to specialize or enhance their expertise in network defense and security will find this course to be a comprehensive resource.
- System Administrators: System admins who wish to strengthen their network security skills and better protect their infrastructure will gain practical insights and techniques from this course.
- Security Enthusiasts: Individuals with a keen interest in network security and a desire to understand the complexities of protecting networks against threats will find the course engaging and informative.
User Reviews
Rating
Meta Brains
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 41
- duration 3:41:04
- Release Date 2024/03/13