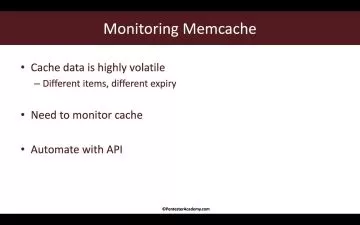
Mobile Security
Focused View
3:21:16
18 View
1. Exposure from Unmanaged Mobile Device.mp4
29:27
2. Exposure from Unmanaged Mobile Device Part 2.mp4
30:04
3. Securing Devices with MDM.mp4
25:24
4. Man in the Middle Attacks.mp4
26:33
5. Performing an Impersonation Attack.mp4
34:47
6. Executing a Remote Exploit.mp4
28:30
7. Trojan Horse Exploit.mp4
26:31
More details
User Reviews
Rating
average 0
Focused display

ITProTV
View courses ITProTVWe created ITProTV [ITPro] because it is the IT training we wanted to have ourselves — engaging, conversational, affordable, and convenient.
- language english
- Training sessions 7
- duration 3:21:16
- Release Date 2024/04/26