Mitigating Security Vulnerabilities on Google Cloud Platform
Google Cloud
1:32:39
Description
This course gives participants broad study of security controls and techniques on Google Cloud Platform.
What You'll Learn?
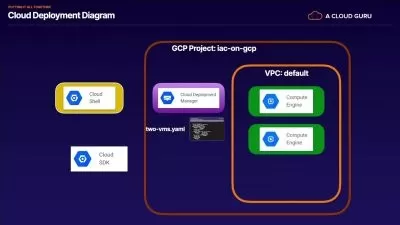
This course gives participants broad study of security controls and techniques on Google Cloud Platform. Through recorded lectures, demonstrations, and hands-on labs, participants explore and deploy the components of a secure GCP solution, including Cloud Identity, the GCP Resource Manager, Cloud IAM, Google Virtual Private Cloud firewalls, Google Cloud Load balancing, Cloud CDN, Cloud Storage access control technologies, Stackdriver, Security Keys, Customer-Supplied Encryption Keys, the Google Data Loss Prevention API, and Cloud Armor.
More details
User Reviews
Rating
Google Cloud
Instructor's Courses
Pluralsight
View courses Pluralsight- language english
- Training sessions 49
- duration 1:32:39
- level average
- Release Date 2023/10/12