Misconfigurations Defense for Red and Blue Teams
Richea Perry
4:19:31
Description
Misconfigurations Defense for Red and Blue Teams as well as GRC Professionals
What You'll Learn?
- An awareness of the Top common cybersecurity misconfigurations found in large organizations that leads to cyber attacks.
- How to establish security baselines in Windows Cloud Environments (Azure) to mitigate misconfigurations leading to cyber attacks.
- An in-dept understanding of cyber risks associated with these misconfigurations and how they are exploited by attackers.
- Application of AI(ChatGPT, Gimini) to execute various lab activities involving misconfiguration mitigation
- Best Practice recommendations for mitigating these cyber risks associated with these misconfigurations
- How to use MITRE ATT&CK for Technical Mitigation of attacks as a result of these misconfiguartions
- How to secure your cloud (Azure) environment from misconfigurations via Red Team-Azure Penetration Testing
- An Introduction to root cause analsysis and its benefits to a cybersecurity mindset
- Open-Source Tools for Configurations Management to mitigate cyber attacks
- How develop a Root cause analysis for selected security misconfigurations
- How to address various scenarios involving the skills of Red or Blue Teamer as it relates to protecting systems from these top 10 misconfiguartions.
- A better understanding of cyber risks in order to develop appropriate policies & conduct effective risks assessments policies as a GRC Professional
Who is this for?
What You Need to Know?
More details
DescriptionThis course is designed for aspiring Red & Blue Teamers, Security leaders, Network defenders and those thinking of transitioning into cybersecurity, or even those already into cybersecurity that needs that holistic view of how both red and blue teams can work together efficiently in keeping people, processes and technology infrastructures secure by understanding the most common misconfigurations that leads to cyber attacks and most importantly how to prevent these attacks from occurring. The learner will gain knowledge and practical skills where applicable in regards to the following:
The Top 10 most common cybersecurity misconfigurations found in both mid to large size organizations that leads to cyber attacks.
Establishing security baselines in Windows Cloud Environments (Azure) to mitigate misconfigurations leading to cyber attacks.
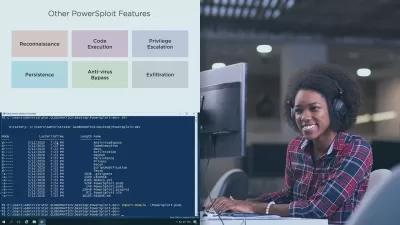
How to practically address the following top 10 misconfigurations that leads to network\cyber attacks:
  1-Default configurations of software and applications
  2-Improper separation of user/administrator privilege
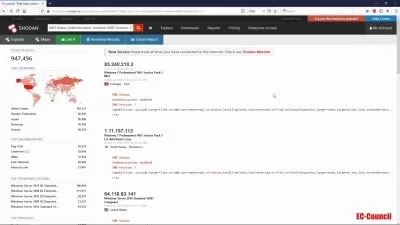
  3-Insufficient internal network monitoring
  4-Lack of network segmentation
  5-Poor patch management
  6-Bypass of system access controls
  7-Weak or misconfigured multi-factor authentication (MFA) methods
  8-Insufficient access control lists (ACLs) on network shares and services
  9-Poor credential hygiene
  10-Unrestricted code execution
Cyber risks associated with these misconfiguration and how they are exploited by attackers.
Best Practice recommendations for mitigating these cyber risks associated with these misconfigurations
Use of MITRE ATT&CK Technical recommendations for Mitigating these attacks resulting from these misconfiguration
Introduction to root cause analysis and its benefits to a cybersecurity mindset
Intro to Open-Source Tools for Configurations Management to mitigate cyber attacks
Ways to Improve Monitoring and Hardening of Networks for Blue & Network Admin Teams against cyber attacks
Use of AI to generate defense checklist that can be used as guides by network defenders to prevent these misconfigurations.
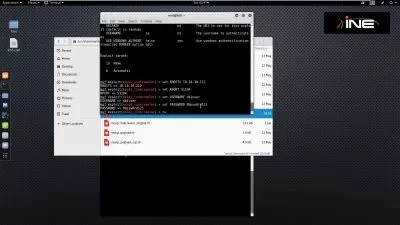
Securing your cloud (Azure) environment from misconfigurations via Red Team-Azure Penetration Testing
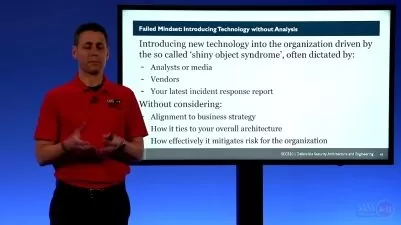
The misconfigurations to be explored in this course are based on NSA and CISA teams conducting comprehensive security assessments of numerous network enclaves within various organizations and during these assessments, they identified the 10 most common network misconfigurations, which are systemic weaknesses across many networks leading to system compromises.
Who this course is for:
- This course is designed for aspiring Red & Blue Teamers, Cyber Security Leaders, Network defenders and those thinking of transitioning into cybersecurity, or even those already into cybersecurity that needs that holistic view of how both red and blue teams can work together efficiently in keeping people, processes and technology infrastructures secure by understanding the most common misconfigurations that leads to cyber attacks and most importantly how to prevent these attacks from occurring.
This course is designed for aspiring Red & Blue Teamers, Security leaders, Network defenders and those thinking of transitioning into cybersecurity, or even those already into cybersecurity that needs that holistic view of how both red and blue teams can work together efficiently in keeping people, processes and technology infrastructures secure by understanding the most common misconfigurations that leads to cyber attacks and most importantly how to prevent these attacks from occurring. The learner will gain knowledge and practical skills where applicable in regards to the following:
The Top 10 most common cybersecurity misconfigurations found in both mid to large size organizations that leads to cyber attacks.
Establishing security baselines in Windows Cloud Environments (Azure) to mitigate misconfigurations leading to cyber attacks.
How to practically address the following top 10 misconfigurations that leads to network\cyber attacks:
  1-Default configurations of software and applications
  2-Improper separation of user/administrator privilege
  3-Insufficient internal network monitoring
  4-Lack of network segmentation
  5-Poor patch management
  6-Bypass of system access controls
  7-Weak or misconfigured multi-factor authentication (MFA) methods
  8-Insufficient access control lists (ACLs) on network shares and services
  9-Poor credential hygiene
  10-Unrestricted code execution
Cyber risks associated with these misconfiguration and how they are exploited by attackers.
Best Practice recommendations for mitigating these cyber risks associated with these misconfigurations
Use of MITRE ATT&CK Technical recommendations for Mitigating these attacks resulting from these misconfiguration
Introduction to root cause analysis and its benefits to a cybersecurity mindset
Intro to Open-Source Tools for Configurations Management to mitigate cyber attacks
Ways to Improve Monitoring and Hardening of Networks for Blue & Network Admin Teams against cyber attacks
Use of AI to generate defense checklist that can be used as guides by network defenders to prevent these misconfigurations.
Securing your cloud (Azure) environment from misconfigurations via Red Team-Azure Penetration Testing
The misconfigurations to be explored in this course are based on NSA and CISA teams conducting comprehensive security assessments of numerous network enclaves within various organizations and during these assessments, they identified the 10 most common network misconfigurations, which are systemic weaknesses across many networks leading to system compromises.
Who this course is for:
- This course is designed for aspiring Red & Blue Teamers, Cyber Security Leaders, Network defenders and those thinking of transitioning into cybersecurity, or even those already into cybersecurity that needs that holistic view of how both red and blue teams can work together efficiently in keeping people, processes and technology infrastructures secure by understanding the most common misconfigurations that leads to cyber attacks and most importantly how to prevent these attacks from occurring.
User Reviews
Rating
Richea Perry
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 50
- duration 4:19:31
- Release Date 2024/05/18