Microsoft Sentinel course with hands on sims for beginners
John Christopher
6:24:03
Description
Learn how to expertly administer Microsoft Sentinel (including SOAR and SIEM) with hands on experience!
What You'll Learn?
- Learn the concepts and perform hands on activities needed to master Microsoft Sentinel (SOAR and SIEM)
- Gain a tremendous amount of knowledge involving Microsoft Sentinel (SOAR and SIEM)
- Learn using hands on simulations on how to manage Microsoft Sentinel (SOAR and SIEM)
- Learn how to set up your own test lab for practicing the concepts!
Who is this for?
What You Need to Know?
More details
DescriptionWe really hope you'll agree, this training is way more than the average course on Udemy!
Have access to the following:
Training from an instructor of over 20 years who has trained thousands of people and also a Microsoft Certified Trainer
Lecture that explains the concepts in an easy to learn method for someone that is just starting out with this material
Instructor led hands on and simulations to practice that can be followed even if you have little to no experience
TOPICS COVEREDÂ INCLUDINGÂ HANDSÂ ONÂ LECTUREÂ ANDÂ PRACTICEÂ TUTORIALS:
Introduction
Welcome to the course
Understanding the Microsoft Environment
Foundations of Active Directory Domains
Foundations of RAS, DMZ, and Virtualization
Foundations of the Microsoft Cloud Services
DONT SKIP: The first thing to know about Microsoft cloud services
DONT SKIP: Azure AD is now renamed to Entra ID
Questions for John Christopher
Performing hands on activities
DONT SKIP: Using Assignments in the course
Creating a free Microsoft 365 Account
Getting your free Azure credit
Understanding and setting up a Microsoft Sentinel Workspace
Overview of Microsoft Sentinel
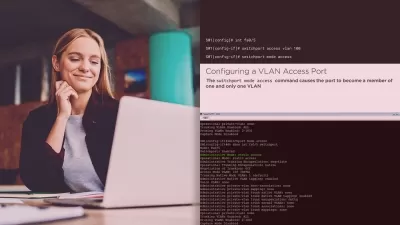
Configuring a Microsoft Sentinel workspace
Managing roles regarding Sentinel
Managing log types, log retention, and data storage in Sentinel
Working with data connectors and ingestion in Microsoft Sentinel
Microsoft Sentinel data source identification
Setting up connectors for ingesting data into Microsoft Sentinel
Connecting Sentinel with Microsoft 365 Defender and Defender for Cloud
Common Event Format (CEF) and Syslog event collections
Windows Security Event Collection setup in Microsoft Sentinel
Managing threat intelligence connectors in Microsoft Sentinel
Working with custom log tables
Using analytics rules in Microsoft Sentinel
Understanding analytics rules in Microsoft Sentinel
Fusion rule configuration
Security analytics rules
Working with scheduled query rules in Microsoft Sentinel
Custom scheduled query rules
Working with near-real-time (NRT) analytics rules
Content hub analytics rules
Watchlists in Microsoft Sentinel
Threat indicators in Microsoft Sentinel
Classification, normalization & security orchestration automated response (SOAR)
Working with using entities for classifying and analyzing data
Advanced Security Information Model(ASIM) queries with Microsoft Sentinel
ASIM parser management
Using automation rules
Using playbooks in Microsoft Sentinel
Automation rule triggering using analytic rules
Alert and incident playbook triggering
Dealing with Incidents and Workbooks for analyzes and interpretation of data
Incident generation in Microsoft Sentinel
Understanding the concepts of triaging incidents in Sentinel
Microsoft Sentinel incident investigation
How to respond to Microsoft Sentinel incidents
Multi-workspace incident investigation
Workbook template customization and management
Implementing custom workbooks in Microsoft Sentinel
Working with advanced visualizations
Threat hunting and entity behavior analytics in Microsoft Sentinel
MITRE ATT&CK attack vectors in Microsoft Sentinel
Using hunting queries from the content gallery
Hunting query customization
Data investigations with hunting bookmarks
Using Livestream to monitor hunting queries
How archived log data can be retrieved in Microsoft Sentinel
Search job management in Microsoft Sentinel
Entity Behavior Analytics settings
Entity page investigation of threats
Anomaly detection analytics rules in Microsoft Sentinel
Conclusion
Cleaning up your lab environment
Getting a Udemy certificate
BONUS Where do I go from here?
Who this course is for:
- IT people interested in learning a tremendous amount about Microsoft Sentinel (SOAR and SIEM)
We really hope you'll agree, this training is way more than the average course on Udemy!
Have access to the following:
Training from an instructor of over 20 years who has trained thousands of people and also a Microsoft Certified Trainer
Lecture that explains the concepts in an easy to learn method for someone that is just starting out with this material
Instructor led hands on and simulations to practice that can be followed even if you have little to no experience
TOPICS COVEREDÂ INCLUDINGÂ HANDSÂ ONÂ LECTUREÂ ANDÂ PRACTICEÂ TUTORIALS:
Introduction
Welcome to the course
Understanding the Microsoft Environment
Foundations of Active Directory Domains
Foundations of RAS, DMZ, and Virtualization
Foundations of the Microsoft Cloud Services
DONT SKIP: The first thing to know about Microsoft cloud services
DONT SKIP: Azure AD is now renamed to Entra ID
Questions for John Christopher
Performing hands on activities
DONT SKIP: Using Assignments in the course
Creating a free Microsoft 365 Account
Getting your free Azure credit
Understanding and setting up a Microsoft Sentinel Workspace
Overview of Microsoft Sentinel
Configuring a Microsoft Sentinel workspace
Managing roles regarding Sentinel
Managing log types, log retention, and data storage in Sentinel
Working with data connectors and ingestion in Microsoft Sentinel
Microsoft Sentinel data source identification
Setting up connectors for ingesting data into Microsoft Sentinel
Connecting Sentinel with Microsoft 365 Defender and Defender for Cloud
Common Event Format (CEF) and Syslog event collections
Windows Security Event Collection setup in Microsoft Sentinel
Managing threat intelligence connectors in Microsoft Sentinel
Working with custom log tables
Using analytics rules in Microsoft Sentinel
Understanding analytics rules in Microsoft Sentinel
Fusion rule configuration
Security analytics rules
Working with scheduled query rules in Microsoft Sentinel
Custom scheduled query rules
Working with near-real-time (NRT) analytics rules
Content hub analytics rules
Watchlists in Microsoft Sentinel
Threat indicators in Microsoft Sentinel
Classification, normalization & security orchestration automated response (SOAR)
Working with using entities for classifying and analyzing data
Advanced Security Information Model(ASIM) queries with Microsoft Sentinel
ASIM parser management
Using automation rules
Using playbooks in Microsoft Sentinel
Automation rule triggering using analytic rules
Alert and incident playbook triggering
Dealing with Incidents and Workbooks for analyzes and interpretation of data
Incident generation in Microsoft Sentinel
Understanding the concepts of triaging incidents in Sentinel
Microsoft Sentinel incident investigation
How to respond to Microsoft Sentinel incidents
Multi-workspace incident investigation
Workbook template customization and management
Implementing custom workbooks in Microsoft Sentinel
Working with advanced visualizations
Threat hunting and entity behavior analytics in Microsoft Sentinel
MITRE ATT&CK attack vectors in Microsoft Sentinel
Using hunting queries from the content gallery
Hunting query customization
Data investigations with hunting bookmarks
Using Livestream to monitor hunting queries
How archived log data can be retrieved in Microsoft Sentinel
Search job management in Microsoft Sentinel
Entity Behavior Analytics settings
Entity page investigation of threats
Anomaly detection analytics rules in Microsoft Sentinel
Conclusion
Cleaning up your lab environment
Getting a Udemy certificate
BONUS Where do I go from here?
Who this course is for:
- IT people interested in learning a tremendous amount about Microsoft Sentinel (SOAR and SIEM)
User Reviews
Rating
John Christopher
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 59
- duration 6:24:03
- Release Date 2024/01/12