Microsoft Sentinel Complete Expert Ninja Course NEW SC-200
Michael Davis
2:14:54
Description
LEARN Microsoft Sentinel Build The Next-Gen SOC - SIEM + SOAR + XDR
What You'll Learn?
- Microsoft Sentinel
- Learn Microsoft Sentinel & The Next Gen-SOC
- Learn What Is a SIEM + SOAR
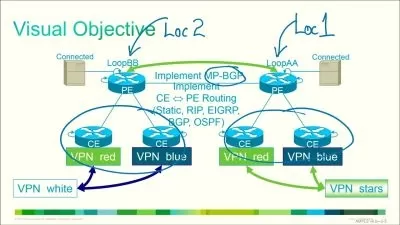
- Learn Microsoft Sentinel Design & Architecture
- The Life Cycle Of Microsoft Sentinel
- The Perquisites Of Microsoft Sentinel
- Learn About Threat Intelligence
- Hunting
- Learn How To Deploy Microsoft Sentinel
- Learn About Management Levels & Hierarchy
- Why Microsoft Sentinel
- Automation & Playbooks
- MITRE Attack
- Data Connectors
- Watchlist
- Microsoft Sentinel Workspace
- Analytic Rules
- Workbooks & Dashboards
- Repositories
- Learn About The Content Hub
- Learn About Notebooks
- Incidents
- Learn About Entity Behavior
Who is this for?
What You Need to Know?
More details
DescriptionMicrosoft Sentinel & The Next Gen-SOC
Learn Microsoft Sentinel Today!
Create interactive reports by using workbooks
Collect data at cloud scale across all users, devices, applications, and infrastructure, both on-premises and in multiple clouds.
Detect previously undetected threats, and minimize false positives using Microsoft's analytics and unparalleled threat intelligence.
Investigate threats with artificial intelligence, and hunt for suspicious activities at scale, tapping into years of cyber security work at Microsoft.
Respond to incidents rapidly with built-in orchestration and automation of common tasks.
Microsoft Sentinel monitors an organization’s entire IT infrastructure, 365 days 24/7, to detect any threat or alert in real time and solve them as quickly and effectively as possible and timely analysis of threats to find ways to improve the organization’s security posture.
Learn What Is a SIEM + SOAR
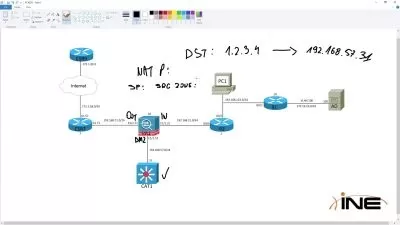
Learn How To Deploy Microsoft Sentinel
Learn Microsoft Sentinel Design & Architecture
Learn About Threat Intelligence
Hunting
Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise. With Microsoft Sentinel, you get a single solution for attack detection, threat visibility, proactive hunting, and threat response.
Deliver intelligent security analytics and threat intelligence across the enterprise. With Microsoft Sentinel, you get a single solution for attack detection, threat visibility, proactive hunting, and threat response.
Correlate alerts into incidents by using analytics rules
Automate and orchestrate common tasks by using playbooks
Automate your common tasks and simplify security orchestration with playbooks that integrate with Azure services and your existing tools.
Investigate the scope and root cause of security threats
Microsoft Sentinel deep investigation tools help you to understand the scope and find the root cause of a potential security threat. You can choose an entity on the interactive graph to ask interesting questions for a specific entity, and drill down into that entity and its connections to get to the root cause of the threat.
Who this course is for:
- Microsoft Sentinel Interactive Expert Course - Build The Next-Gen Soc With Microsoft Sentinel
- Microsoft Sentinel #1 Leader Of Cyber Security
Microsoft Sentinel & The Next Gen-SOC
Learn Microsoft Sentinel Today!
Create interactive reports by using workbooks
Collect data at cloud scale across all users, devices, applications, and infrastructure, both on-premises and in multiple clouds.
Detect previously undetected threats, and minimize false positives using Microsoft's analytics and unparalleled threat intelligence.
Investigate threats with artificial intelligence, and hunt for suspicious activities at scale, tapping into years of cyber security work at Microsoft.
Respond to incidents rapidly with built-in orchestration and automation of common tasks.
Microsoft Sentinel monitors an organization’s entire IT infrastructure, 365 days 24/7, to detect any threat or alert in real time and solve them as quickly and effectively as possible and timely analysis of threats to find ways to improve the organization’s security posture.
Learn What Is a SIEM + SOAR
Learn How To Deploy Microsoft Sentinel
Learn Microsoft Sentinel Design & Architecture
Learn About Threat Intelligence
Hunting
Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise. With Microsoft Sentinel, you get a single solution for attack detection, threat visibility, proactive hunting, and threat response.
Deliver intelligent security analytics and threat intelligence across the enterprise. With Microsoft Sentinel, you get a single solution for attack detection, threat visibility, proactive hunting, and threat response.
Correlate alerts into incidents by using analytics rules
Automate and orchestrate common tasks by using playbooks
Automate your common tasks and simplify security orchestration with playbooks that integrate with Azure services and your existing tools.
Investigate the scope and root cause of security threats
Microsoft Sentinel deep investigation tools help you to understand the scope and find the root cause of a potential security threat. You can choose an entity on the interactive graph to ask interesting questions for a specific entity, and drill down into that entity and its connections to get to the root cause of the threat.
Who this course is for:
- Microsoft Sentinel Interactive Expert Course - Build The Next-Gen Soc With Microsoft Sentinel
- Microsoft Sentinel #1 Leader Of Cyber Security
User Reviews
Rating
Michael Davis
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 28
- duration 2:14:54
- Release Date 2023/06/17